Our first story of 2026 revealed how a damaging new botnet referred to as Kimwolf has contaminated greater than two million units by mass-compromising an enormous variety of unofficial Android TV streaming bins. At the moment, we’ll dig via digital clues left behind by the hackers, community operators and companies that seem to have benefitted from Kimwolf’s unfold.
On Dec. 17, 2025, the Chinese language safety agency XLab revealed a deep dive on Kimwolf, which forces contaminated units to take part in distributed denial-of-service (DDoS) assaults and to relay abusive and malicious Web visitors for so-called “residential proxy” companies.
The software program that turns one’s system right into a residential proxy is usually quietly bundled with cellular apps and video games. Kimwolf particularly focused residential proxy software program that’s manufacturing unit put in on greater than a thousand totally different fashions of unsanctioned Android TV streaming units. In a short time, the residential proxy’s Web deal with begins funneling visitors that’s linked to advert fraud, account takeover makes an attempt and mass content material scraping.
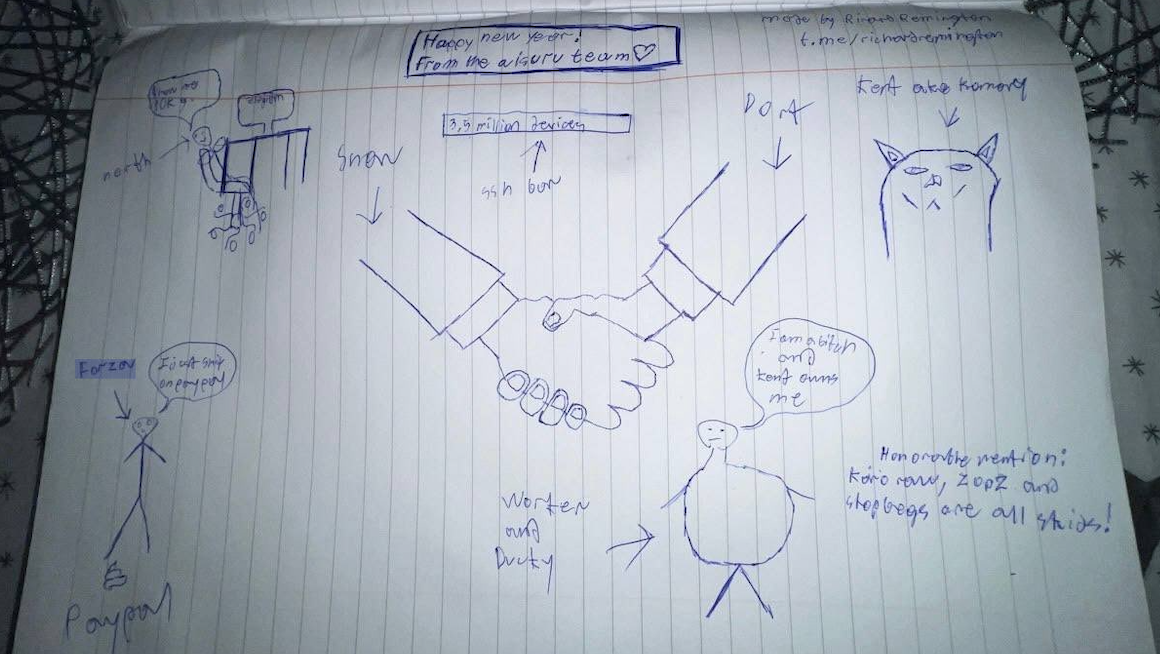
The XLab report defined its researchers discovered “definitive proof” that the identical cybercriminal actors and infrastructure had been used to deploy each Kimwolf and the Aisuru botnet — an earlier model of Kimwolf that additionally enslaved units to be used in DDoS assaults and proxy companies.
XLab stated it suspected since October that Kimwolf and Aisuru had the identical writer(s) and operators, based mostly partly on shared code modifications over time. Nevertheless it stated these suspicions had been confirmed on December 8 when it witnessed each botnet strains being distributed by the identical Web deal with at 93.95.112[.]59.
Picture: XLab.
RESI RACK
Public data present the Web deal with vary flagged by XLab is assigned to Lehi, Utah-based Resi Rack LLC. Resi Rack’s web site payments the corporate as a “Premium Recreation Server Internet hosting Supplier.” In the meantime, Resi Rack’s advertisements on the Web moneymaking discussion board BlackHatWorld consult with it as a “Premium Residential Proxy Internet hosting and Proxy Software program Options Firm.”
Resi Rack co-founder Cassidy Hales informed KrebsOnSecurity his firm acquired a notification on December 10 about Kimwolf utilizing their community “that detailed what was being completed by one in all our clients leasing our servers.”
“After we acquired this e-mail we took care of this difficulty instantly,” Hales wrote in response to an e-mail requesting remark. “That is one thing we’re very disenchanted is now related to our identify and this was not the intention of our firm in anyway.”
The Resi Rack Web deal with cited by XLab on December 8 got here onto KrebsOnSecurity’s radar greater than two weeks earlier than that. Benjamin Brundage is founding father of Synthient, a startup that tracks proxy companies. In late October 2025, Brundage shared that the folks promoting numerous proxy companies which benefitted from the Aisuru and Kimwolf botnets had been doing so at a brand new Discord server referred to as resi[.]to.

On November 24, 2025, a member of the resi-dot-to Discord channel shares an IP deal with chargeable for proxying visitors over Android TV streaming bins contaminated by the Kimwolf botnet.
When KrebsOnSecurity joined the resi[.]to Discord channel in late October as a silent lurker, the server had fewer than 150 members, together with “Shox” — the nickname utilized by Resi Rack’s co-founder Mr. Hales — and his enterprise accomplice “Linus,” who didn’t reply to requests for remark.
Different members of the resi[.]to Discord channel would periodically submit new IP addresses that had been chargeable for proxying visitors over the Kimwolf botnet. Because the screenshot from resi[.]to above exhibits, that Resi Rack Web deal with flagged by XLab was utilized by Kimwolf to direct proxy visitors way back to November 24, if not earlier. All informed, Synthient stated it tracked not less than seven static Resi Rack IP addresses linked to Kimwolf proxy infrastructure between October and December 2025.
Neither of Resi Rack’s co-owners responded to follow-up questions. Each have been lively in promoting proxy companies by way of Discord for almost two years. Based on a evaluation of Discord messages listed by the cyber intelligence agency Flashpoint, Shox and Linus spent a lot of 2024 promoting static “ISP proxies” by routing numerous Web deal with blocks at main U.S. Web service suppliers.
In February 2025, AT&T introduced that efficient July 31, 2025, it might not originate routes for community blocks that aren’t owned and managed by AT&T (different main ISPs have since made related strikes). Lower than a month later, Shox and Linus informed clients they might quickly stop providing static ISP proxies on account of these coverage modifications.
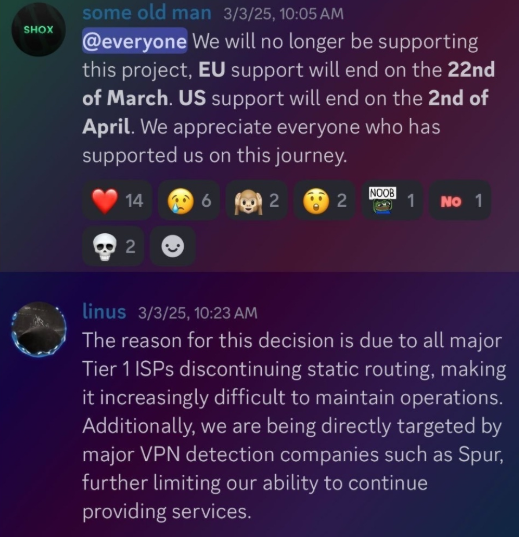
Shox and Linux, speaking about their determination to cease promoting ISP proxies.
DORT & SNOW
The acknowledged proprietor of the resi[.]to Discord server glided by the abbreviated username “D.” That preliminary seems to be quick for the hacker deal with “Dort,” a reputation that was invoked incessantly all through these Discord chats.
Dort’s profile on resi dot to.
This “Dort” nickname got here up in KrebsOnSecurity’s current conversations with “Forky,” a Brazilian man who acknowledged being concerned within the advertising and marketing of the Aisuru botnet at its inception in late 2024. However Forky vehemently denied having something to do with a sequence of huge and record-smashing DDoS assaults within the latter half of 2025 that had been blamed on Aisuru, saying the botnet by that time had been taken over by rivals.
Forky asserts that Dort is a resident of Canada and one in all not less than two people at the moment answerable for the Aisuru/Kimwolf botnet. The opposite particular person Forky named as an Aisuru/Kimwolf botmaster goes by the nickname “Snow.”
On January 2 — simply hours after our story on Kimwolf was revealed — the historic chat data on resi[.]to had been erased with out warning and changed by a profanity-laced message for Synthient’s founder. Minutes after that, your complete server disappeared.
Later that very same day, a number of of the extra lively members of the now-defunct resi[.]to Discord server moved to a Telegram channel the place they posted Brundage’s private info, and customarily complained about being unable to search out dependable “bulletproof” internet hosting for his or her botnet.
Hilariously, a consumer by the identify “Richard Remington” briefly appeared within the group’s Telegram server to submit a crude “Comfortable New 12 months” sketch that claims Dort and Snow are actually answerable for 3.5 million units contaminated by Aisuru and/or Kimwolf. Richard Remington’s Telegram account has since been deleted, however it beforehand acknowledged its proprietor operates a web site that caters to DDoS-for-hire or “stresser” companies looking for to check their firepower.
BYTECONNECT, PLAINPROXIES, AND 3XK TECH
Experiences from each Synthient and XLab discovered that Kimwolf was used to deploy applications that turned contaminated methods into Web visitors relays for a number of residential proxy companies. Amongst these was a element that put in a software program growth package (SDK) referred to as ByteConnect, which is distributed by a supplier referred to as Plainproxies.
ByteConnect says it focuses on “monetizing apps ethically and free,” whereas Plainproxies advertises the flexibility to offer content material scraping firms with “limitless” proxy swimming pools. Nevertheless, Synthient stated that upon connecting to ByteConnect’s SDK they as an alternative noticed a mass inflow of credential-stuffing assaults focusing on e-mail servers and standard on-line web sites.
A search on LinkedIn finds the CEO of Plainproxies is Friedrich Kraft, whose resume says he’s co-founder of ByteConnect Ltd. Public Web routing data present Mr. Kraft additionally operates a internet hosting agency in Germany referred to as 3XK Tech GmbH. Mr. Kraft didn’t reply to repeated requests for an interview.
In July 2025, Cloudflare reported that 3XK Tech (a.okay.a. Drei-Okay-Tech) had turn into the Web’s largest supply of application-layer DDoS assaults. In November 2025, the safety agency GreyNoise Intelligence discovered that Web addresses on 3XK Tech had been chargeable for roughly three-quarters of the Web scanning being completed on the time for a newly found and important vulnerability in safety merchandise made by Palo Alto Networks.
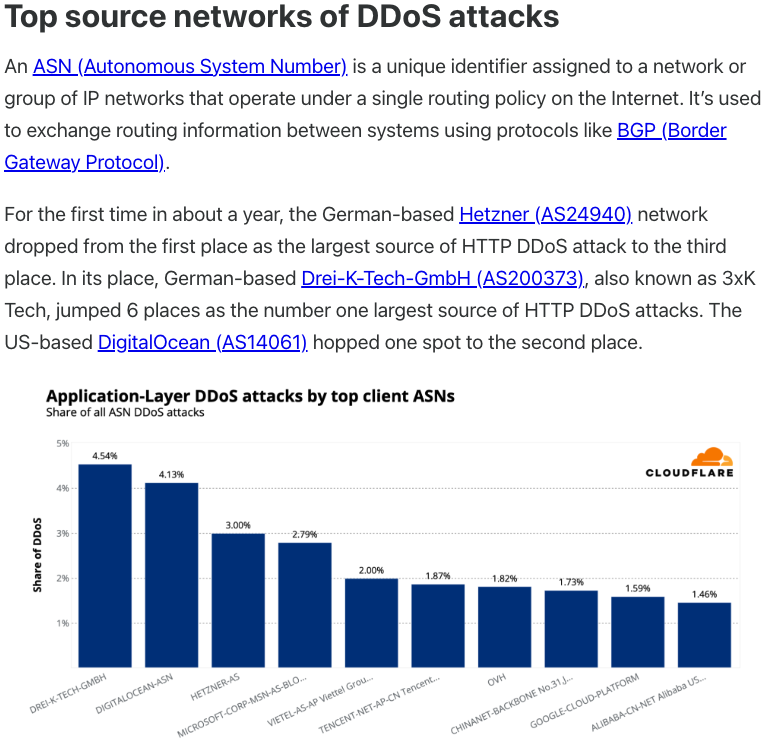
Supply: Cloudflare’s Q2 2025 DDoS menace report.
LinkedIn has a profile for one more Plainproxies worker, Julia Levi, who’s listed as co-founder of ByteConnect. Ms. Levi didn’t reply to requests for remark. Her resume says she beforehand labored for 2 main proxy suppliers: Netnut Proxy Community, and Vibrant Knowledge.
Synthient likewise stated Plainproxies ignored their outreach, noting that the Byteconnect SDK continues to stay lively on units compromised by Kimwolf.
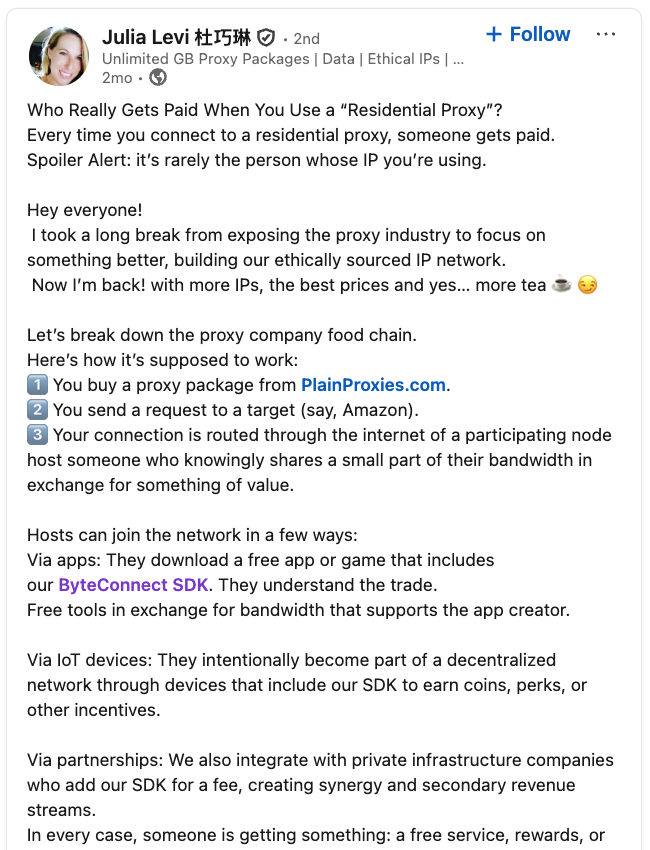
A submit from the LinkedIn web page of Plainproxies Chief Income Officer Julia Levi, explaining how the residential proxy enterprise works.
MASKIFY
Synthient’s January 2 report stated one other proxy supplier closely concerned within the sale of Kimwolf proxies was Maskify, which at the moment advertises on a number of cybercrime boards that it has greater than six million residential Web addresses for hire.
Maskify costs its service at a charge of 30 cents per gigabyte of information relayed via their proxies. Based on Synthient, that worth vary is insanely low and is way cheaper than every other proxy supplier in enterprise at present.
“Synthient’s Analysis Staff acquired screenshots from different proxy suppliers displaying key Kimwolf actors making an attempt to dump proxy bandwidth in alternate for upfront money,” the Synthient report famous. “This method doubtless helped gasoline early growth, with related members spending earnings on infrastructure and outsourced growth duties. Please observe that resellers know exactly what they’re promoting; proxies at these costs are usually not ethically sourced.”
Maskify didn’t reply to requests for remark.
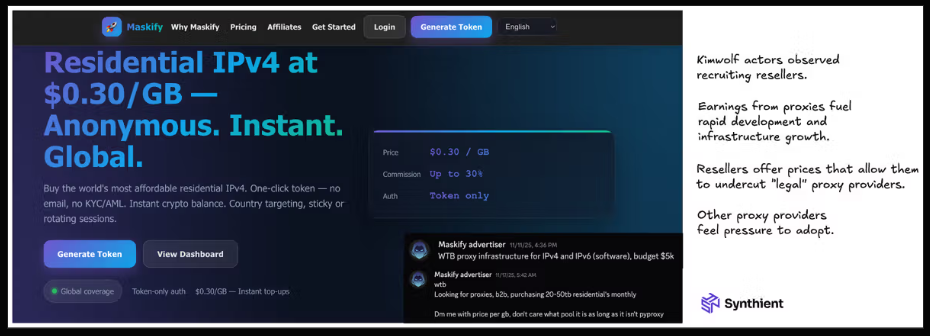
The Maskify web site. Picture: Synthient.
BOTMASTERS LASH OUT
Hours after our first Kimwolf story was revealed final week, the resi[.]to Discord server vanished, Synthient’s web site was hit with a DDoS assault, and the Kimwolf botmasters took to doxing Brundage by way of their botnet.
The harassing messages appeared as textual content data uploaded to the Ethereum Identify Service (ENS), a distributed system for supporting sensible contracts deployed on the Ethereum blockchain. As documented by XLab, in mid-December the Kimwolf operators upgraded their infrastructure and started utilizing ENS to higher stand up to the near-constant takedown efforts focusing on the botnet’s management servers.
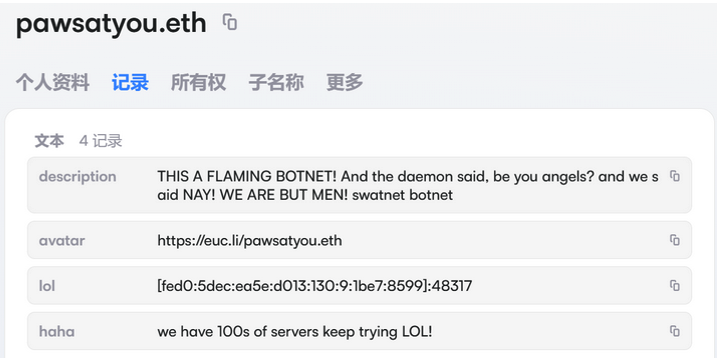
An ENS document utilized by the Kimwolf operators taunts safety corporations attempting to take down the botnet’s management servers. Picture: XLab.
By telling contaminated methods to hunt out the Kimwolf management servers by way of ENS, even when the servers that the botmasters use to regulate the botnet are taken down the attacker solely must replace the ENS textual content document to replicate the brand new Web deal with of the management server, and the contaminated units will instantly know the place to search for additional directions.
“This channel itself depends on the decentralized nature of blockchain, unregulated by Ethereum or different blockchain operators, and can’t be blocked,” XLab wrote.
The textual content data included in Kimwolf’s ENS directions may also function quick messages, similar to people who carried Brundage’s private info. Different ENS textual content data related to Kimwolf provided some sage recommendation: “If flagged, we encourage the TV field to be destroyed.”
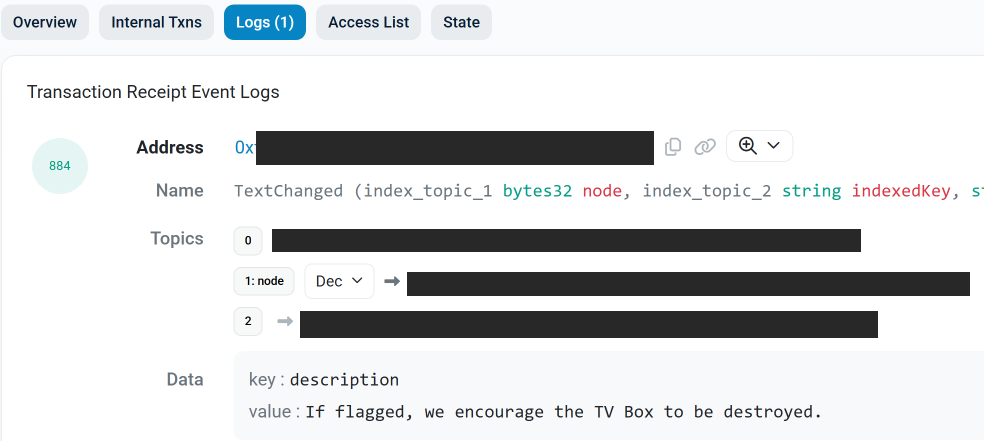
An ENS document tied to the Kimwolf botnet advises, “If flagged, we encourage the TV field to be destroyed.”
Each Synthient and XLabs say Kimwolf targets an enormous variety of Android TV streaming field fashions, all of which have zero safety protections, and plenty of of which ship with proxy malware in-built. Typically talking, if you happen to can ship an information packet to one in all these units you can too seize administrative management over it.
In case you personal a TV field that matches one in all these mannequin names and/or numbers, please simply rip it out of your community. In case you encounter one in all these units on the community of a member of the family or good friend, ship them a hyperlink to this story (or to our January 2 story on Kimwolf) and clarify that it’s not definitely worth the potential trouble and hurt created by preserving them plugged in.