On this blogpost we focus on an unusual kind of phishing marketing campaign focusing on cell customers and analyze a case that we noticed within the wild that focused shoppers of a distinguished Czech financial institution. This method is noteworthy as a result of it installs a phishing utility from a third-party web site with out the person having to permit third-party app set up. For iOS customers, such an motion would possibly break any “walled backyard” assumptions about safety. On Android, this might end result within the silent set up of a particular sort of APK, which on additional inspection even seems to be put in from the Google Play retailer.
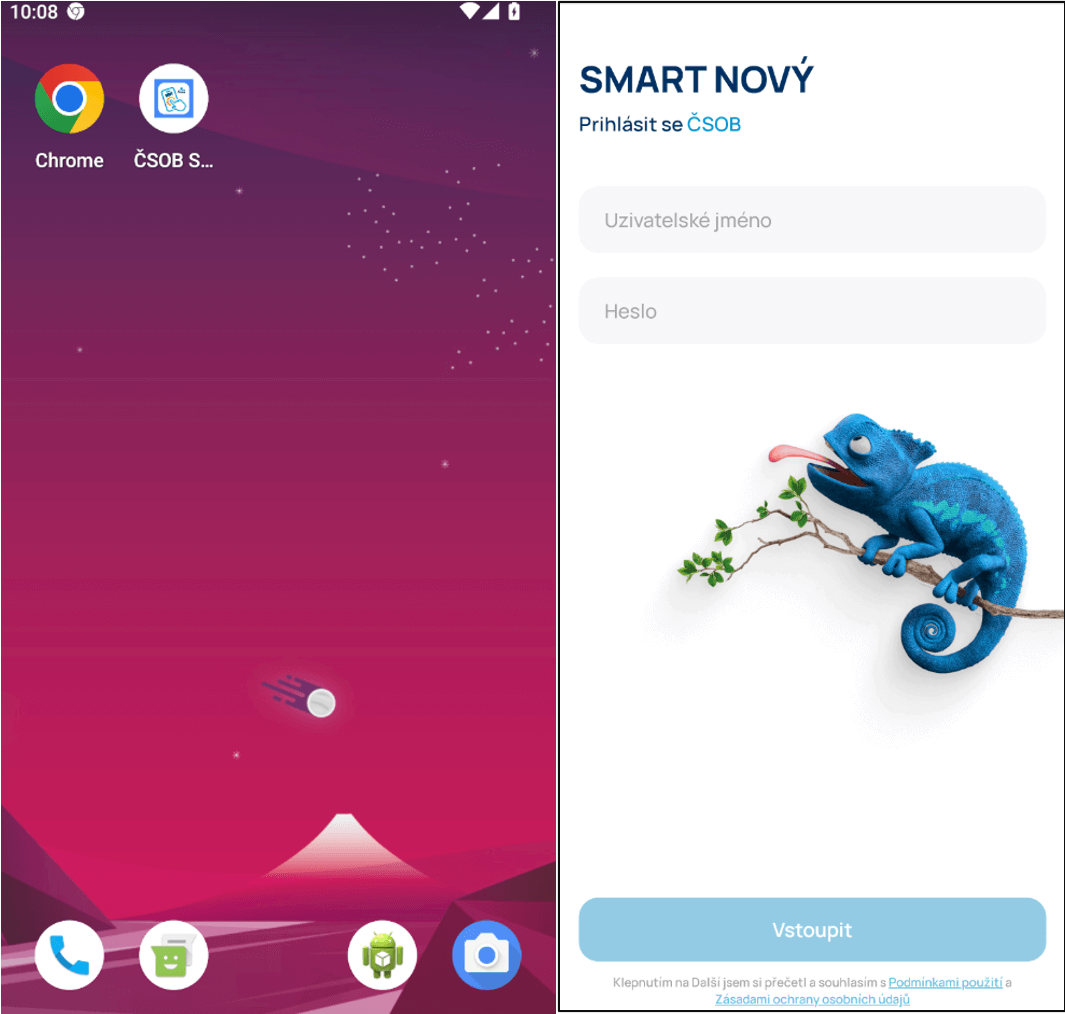
The phishing web sites focusing on iOS instruct victims so as to add a Progressive Net Software (PWA) to their home-screens, whereas on Android the PWA is put in after confirming customized pop-ups within the browser. At this level, on each working programs, these phishing apps are largely indistinguishable from the true banking apps that they mimic. PWAs are primarily web sites bundled into what seems like a standalone utility, with this sense being enhanced by the utilization of native system prompts. PWAs, similar to web sites, are cross-platform, explaining how these PWA phishing campaigns can goal each iOS and Android customers.
This method was first disclosed by CSIRT KNF in Poland in July 2023 and, in November 2023, noticed in Czechia by ESET analysts engaged on the Model Intelligence service. We additionally noticed two instances of cell campaigns in opposition to banks exterior of Czechia: one case focusing on the Hungarian OTP Financial institution and one other focusing on the Georgian TBC Financial institution.
Key factors of the blogpost:
- Normal phishing supply strategies had been mixed with a novel methodology of phishing; focusing on Android and iOS customers through PWAs, and on Android additionally WebAPKs.
- Insidiously, putting in a PWA/WebAPK utility doesn’t warn the sufferer about putting in a third-party utility.
- On Android, these phishing WebAPKs even seem to have been put in from the Google Play retailer.
- A lot of the noticed purposes focused shoppers of Czech banks, however we additionally noticed one phishing app that focused a Hungarian financial institution and one other focusing on a Georgian financial institution.
- Primarily based on the C&C servers utilized and backend infrastructure, we conclude that two totally different risk actors had been working the campaigns.
- Because of our discovery of operator panels on totally different domains, we had been capable of notify the victims’ banks as a way to shield them.
Overview
ESET analysts found a collection of phishing campaigns focusing on cell customers that used three totally different URL supply mechanisms (proven in Determine 1). These mechanisms embrace automated voice calls, SMS messages, and social media malvertising.
The voice name supply is completed through an automatic name that warns the person about an out-of-date banking app and asks the person to pick an choice on the numerical keyboard. After urgent the right button, a phishing URL is shipped through SMS. This was reported in a tweet, by Michal Bláha.
Preliminary supply by SMS was carried out by sending messages indiscriminately to Czech cellphone numbers. The message despatched included a phishing hyperlink and textual content to socially engineer victims into visiting the hyperlink.
Spreading through malicious adverts was accomplished by registering ads on Meta platforms like Instagram and Fb. These adverts included a name to motion, like a restricted supply for customers who “obtain an replace under”. This method permits risk actors to specify the audience by age, gender, and so forth. The ads would then seem in a sufferer’s social media feed.
After opening the URL delivered within the first stage, Android victims are introduced with a high-quality phishing web page imitating the official Google Play retailer web page for the focused banking utility, or a copycat web site for the applying. These had been two distinct campaigns. It’s attainable that the marketing campaign using Google Play visuals would modify itself primarily based on the acquired Person-Agent, to mimic Apple Retailer visuals. We didn’t observe this system in analyzed instances.
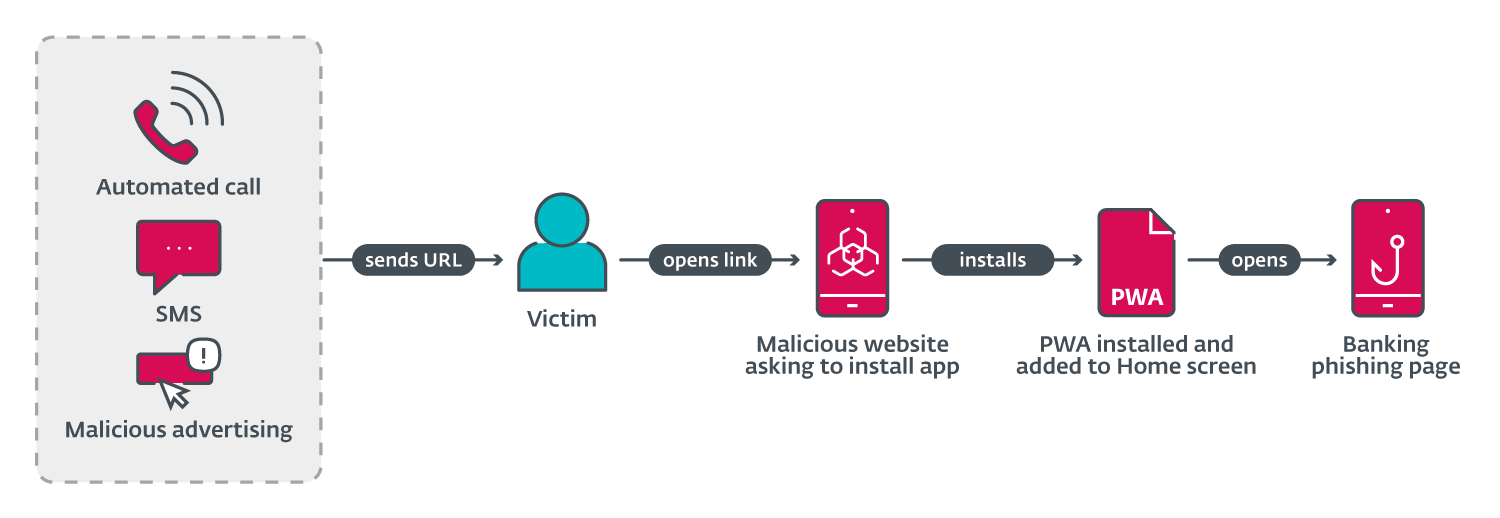
From right here victims are requested to put in a “new model” of the banking utility; an instance of this may be seen in Determine 2. Relying on the marketing campaign, clicking on the set up/replace button launches the set up of a malicious utility from the web site, immediately on the sufferer’s cellphone, both within the type of a WebAPK (for Android customers solely), or as a PWA for iOS and Android customers (if the marketing campaign just isn’t WebAPK primarily based). This significant set up step bypasses conventional browser warnings of “putting in unknown apps”: that is the default habits of Chrome’s WebAPK know-how, which is abused by the attackers.
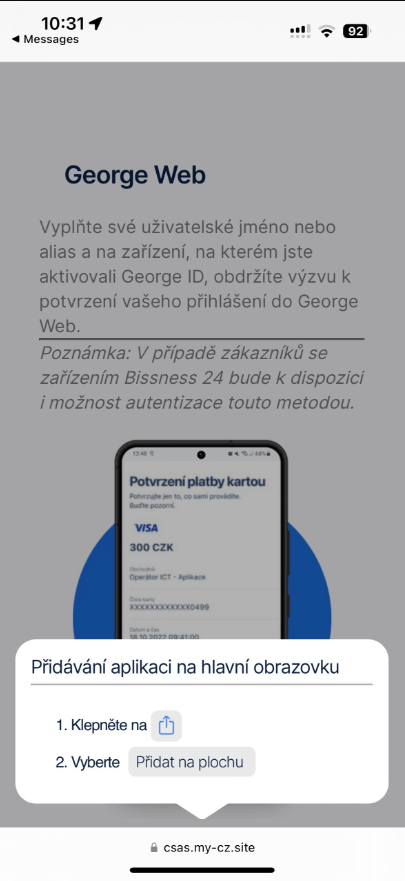
The method is a bit totally different for iOS customers, as an animated pop-up instructs victims the way to add the phishing PWA to their dwelling display screen (see Determine 3). The pop-up copies the look of native iOS prompts. In the long run, even iOS customers aren’t warned about including a doubtlessly dangerous app to their cellphone.
After set up, victims are prompted to submit their web banking credentials to entry their account through the brand new cell banking app. All submitted info is shipped to the attackers’ C&C servers.
Timeline
We found the primary phishing-via-PWA case in early November 2023, and observed the transition to WebAPKs in mid-November 2023. C&C servers that acquired info from phishing purposes had been first found in March 2024 (as might be seen in Determine 4), with knowledge in them confirming that they had been most likely not operational earlier.
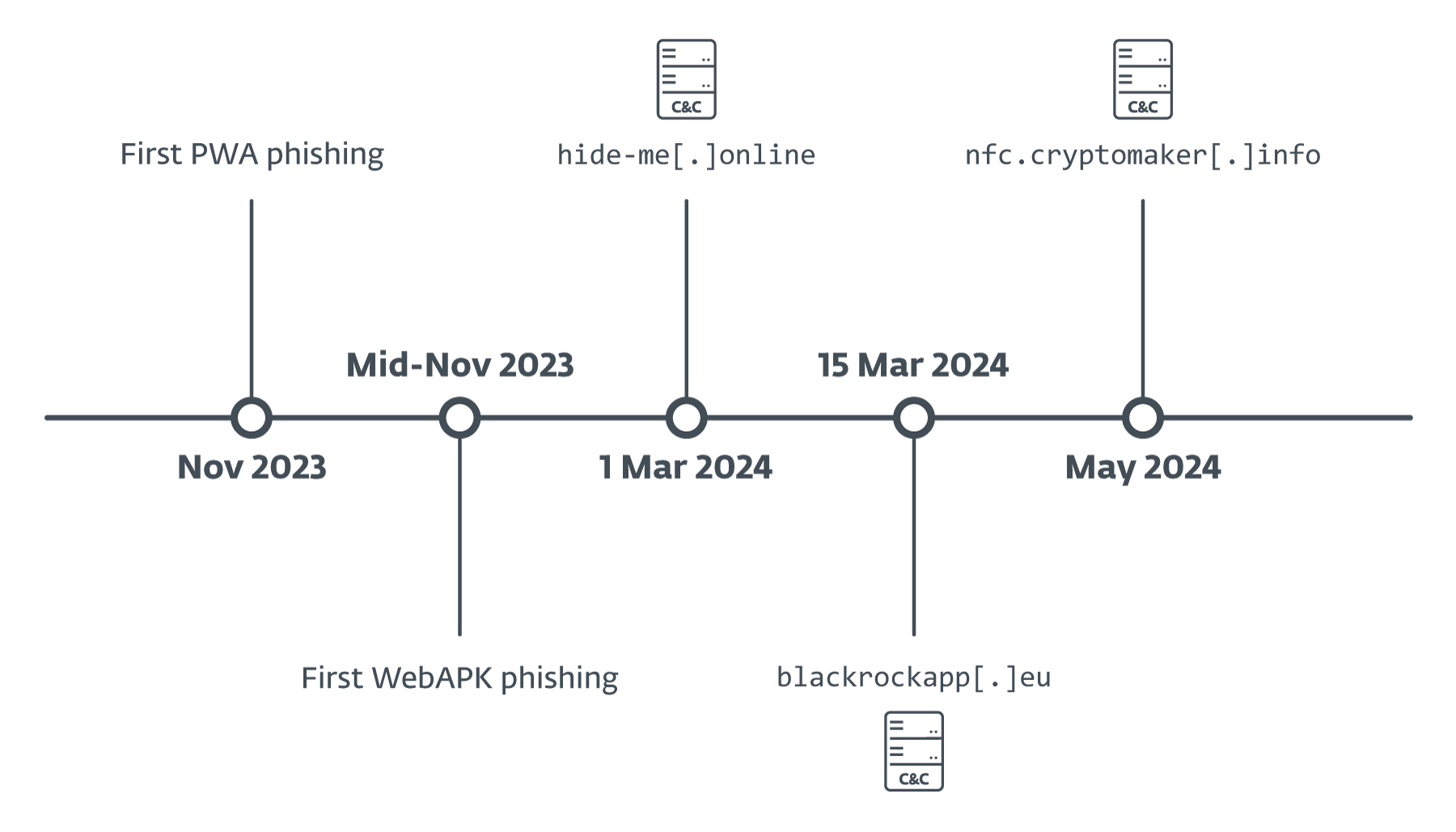
The one exception is the cryptomaker[.]information server, which we found in Could 2024, however included exercise from a marketing campaign in opposition to the Georgian TBC Financial institution in February 2024.
Technical evaluation
On this part we give attention to the evaluation of a marketing campaign in opposition to a distinguished Czech financial institution, using WebAPK know-how. We additionally briefly clarify the underlying know-how of progressive internet purposes (PWAs) and WebAPKs.
PWA and WebAPK purposes
PWAs
The phishing marketing campaign and methodology mentioned on this publish is feasible solely due to the know-how of progressive internet purposes (PWAs). Briefly, PWAs are purposes constructed utilizing conventional internet utility applied sciences that may run on a number of platforms and gadgets. These apps are then put in on the cell phone of the person after a pop-up set up immediate is robotically displayed, or the person manually selects the Set up app choice from a supported browser’s menu. The essential step right here is set up, which permits for the seamless utilization of apps in a separate window and provides them the flexibility to be launched from the menu bar or dwelling display screen. After set up, PWAs on the house display screen are distinguished by the brand of the person’s browser being superimposed on the PWA’s icon (Determine 5).

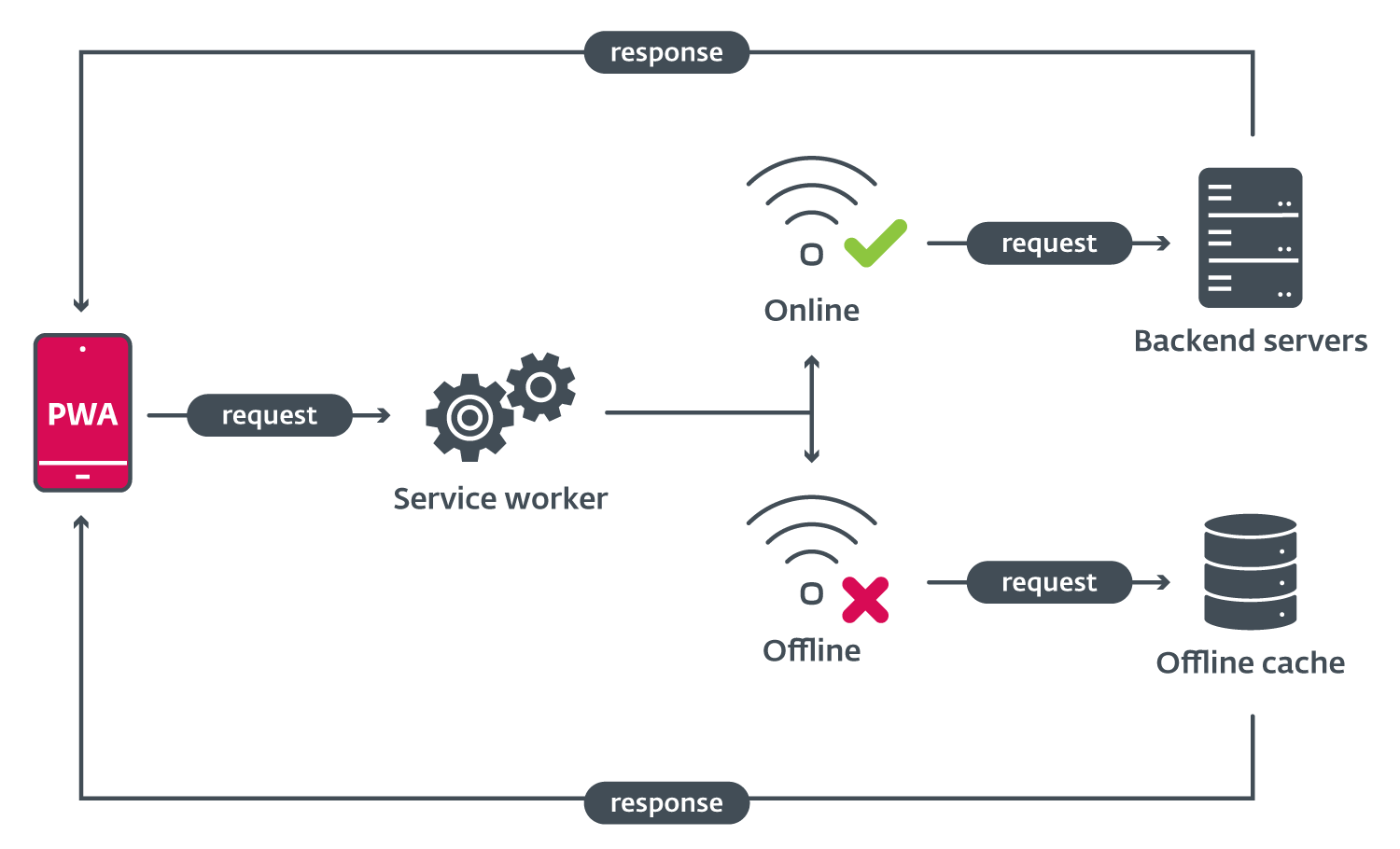
PWAs even have the benefit of a single codebase throughout a number of platforms, which now can also use fashionable browser APIs and even native code, due to WebAssembly. Progressive internet apps can also be used offline, due to service staff (see Determine 6). These staff act as a form of proxy system, retrieving knowledge from the native cache if no web connection is on the market.
All the applying habits is outlined in a single file known as the manifest. This can be a standardized file that defines the brand, title, internet utility scope, sources, and repair employee script of the applying, in addition to the launcher kind. Right here the risk actor can outline the app as standalone, which leads to the PWA behaving like an everyday cell app.
PWAs can also be assigned as default handlers for sure file codecs, however solely as an experimental function, which isn’t supported on cell browsers. This might lead to risk actors writing malicious purposes that register as a default handler for, for instance, all .docx paperwork, and so a easy but highly effective espionage app may very well be created. Nevertheless, even with out that function, entry to browser APIs provides PWAs the best to request entry to microphone, geolocation, digicam, and all different supported browser capabilities, which means that spy ware PWAs may very well be on the radar.
WebAPKs
WebAPKs may very well be thought of an upgraded model of progressive internet apps, because the Chrome browser generates a local Android utility from a PWA : in different phrases, an APK. These WebAPKs appear like common native apps, as their icons lack the browser brand (see Determine 7). Within the PWA/WebAPK phishing scheme, that is used to trick customers into believing that the put in phishing app is their reliable banking utility. The era of WebAPKs is at present solely supported by Google Chrome.

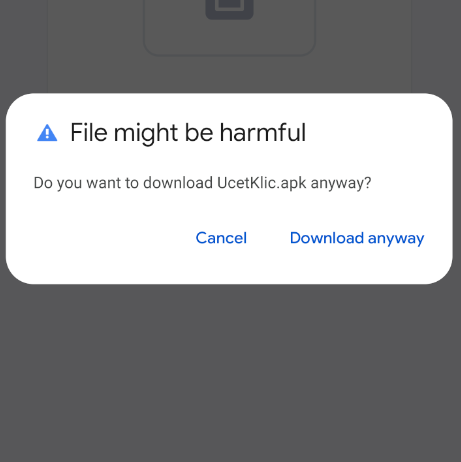
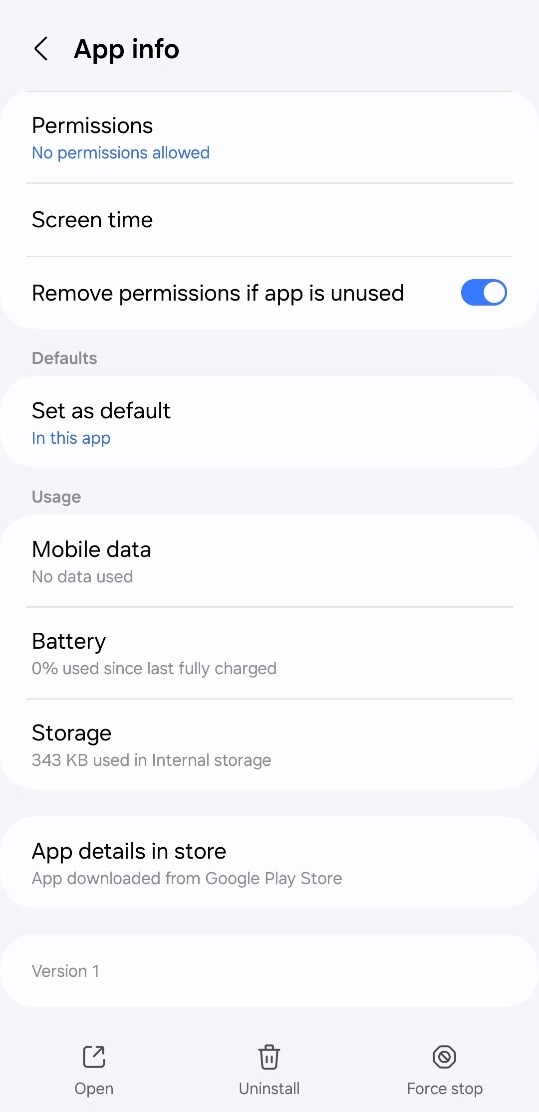
Moreover, putting in a WebAPK doesn’t produce any of the “set up from an untrusted supply” warnings, resembling the instance seen in Determine 8, that customers are generally educated to search for. The app will even be put in if set up from third-party sources just isn’t allowed.
Phishing stream
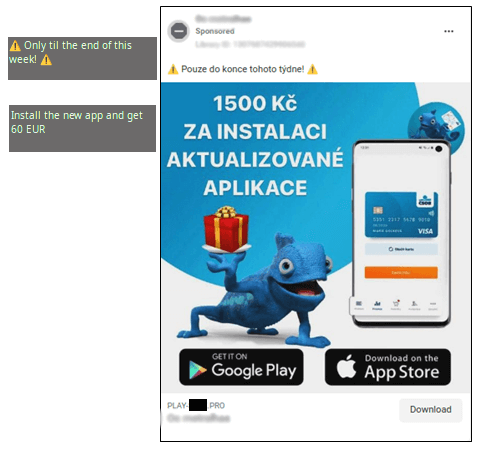
As talked about in our overview of the monitored campaigns, a number of kinds of supply mechanisms had been used. Within the case of the phishing marketing campaign in opposition to the distinguished Czech financial institution, the entire stream began with a phishing hyperlink being unfold by a number of malicious adverts on Fb (see Determine 9). These ads had been registered in bulk, usually 5 – 6 at a time, with every registration at a separate time. The risk actor used specifically created Meta accounts and presumably compromised accounts.
The malicious adverts included a mixture of the financial institution’s official mascot (blue chameleon), in addition to the financial institution’s logos and textual content that both promised a monetary reward upon putting in the app or warned customers {that a} crucial replace had been rolled out.
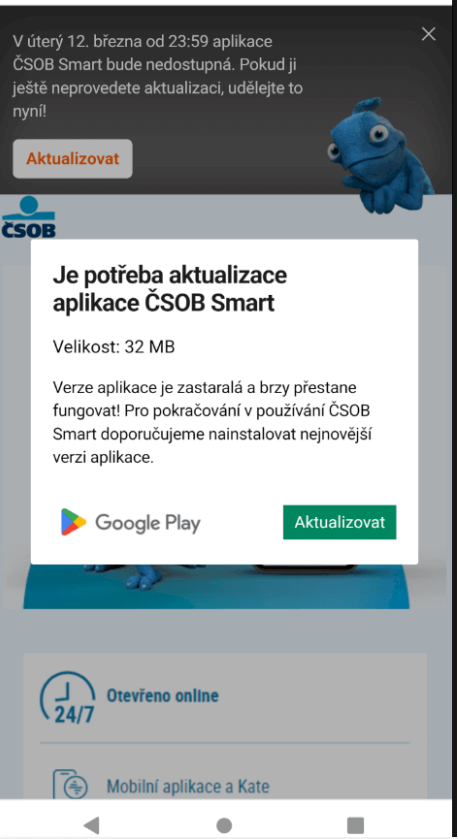
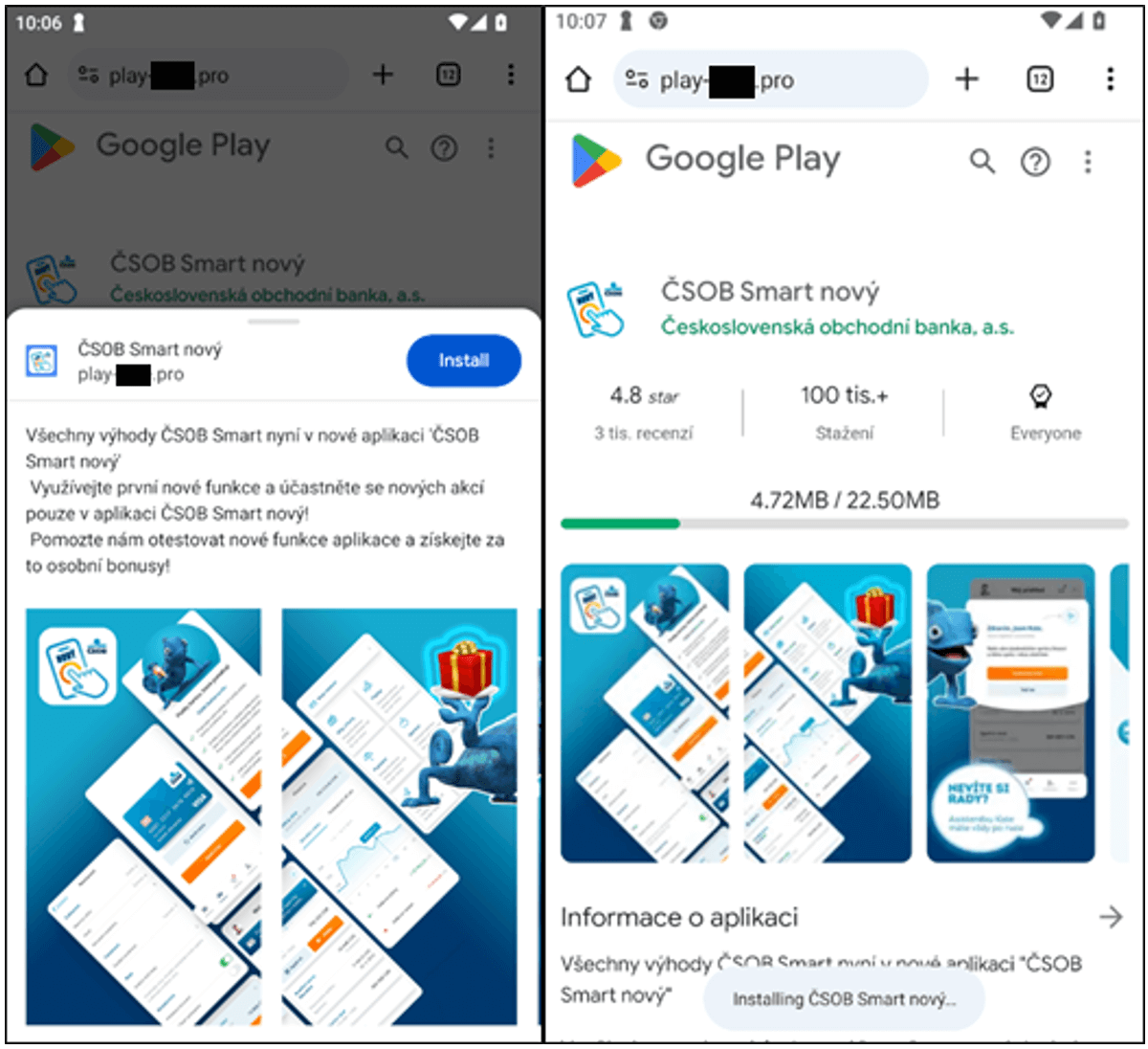
Within the instance case, a limited-time supply of a monetary reward was used to entice victims into visiting the malicious hyperlink. After visiting the hyperlink, customers had been prompted with a convincing, albeit faux, Google Play web page (Determine 10). That is the location from which the phishing WebAPK is downloaded.

The positioning checks for the utilization of a cell consumer through the Person-Agent HTTP header. If the sufferer is certainly on a cell gadget, the “Set up” button prompts the sufferer for set up through a pop-up. If the Person-Agent header is for a desktop, the set up button does nothing. The immediate additionally imitates Google Play animations, additional enhancing the believability of this marketing campaign (Determine 11).
The demonstrated marketing campaign clearly targets Android customers, due to the Google Play visible and animations. Different campaigns (that we noticed and that had been publicly reported) focused customers of each iOS (Determine 12) and Android programs. These websites utilized the visible of a widely known utility on the touchdown web page and prompted victims for the set up of a brand new model. Android customers had been led to put in a WebAPK, and iOS customers to PWAs.
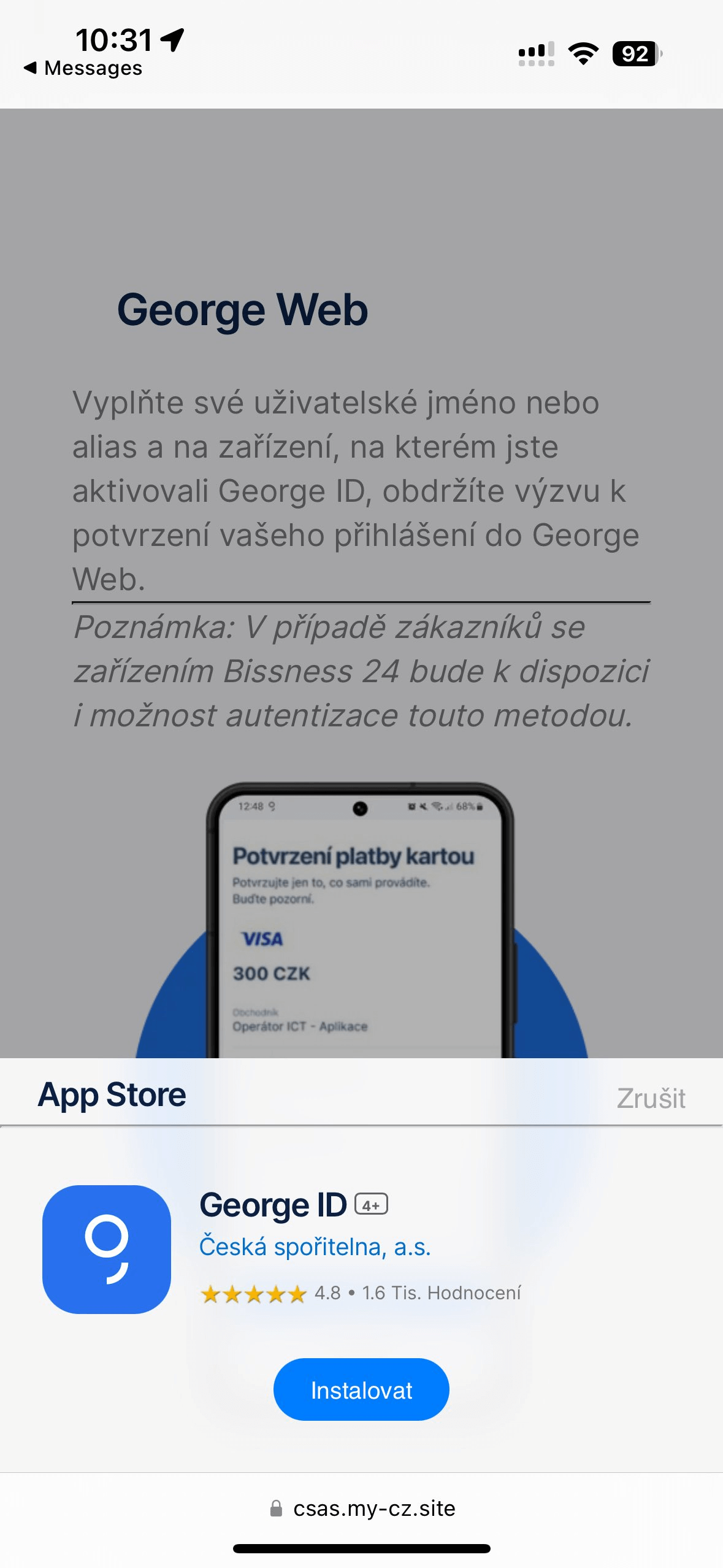
After set up, the phishing PWA/WebAPK is added to the person’s dwelling display screen, and opening it results in a phishing login web page, immediately within the utility (Determine 13).
On prime of all of the beforehand talked about hurdles for an everyday person, the applying’s information tab additionally states that the app was downloaded from the Google Play retailer, which is the default habits (Determine 14). This is applicable to all WebAPK apps.
The phishing utility and phishing URL mentioned on this publish had been reported to ČSOB. The phishing purposes have by no means been out there on the Google Play retailer.
C&C infrastructure
Primarily based on the truth that the campaigns used two distinct C&C infrastructures, we’ve decided that two separate teams had been working the PWA/WebAPK phishing campaigns in opposition to Czech and different banks.
One group used a Telegram bot to log all entered info right into a Telegram group chat through the official Telegram API, and one other used a standard C&C server with an administrative panel. The second group is liable for the marketing campaign lined in one in all our upcoming blogposts.
Telegram bots
All stolen login info was logged through a backend server, which then despatched the person’s entered banking login knowledge right into a Telegram group chat. HTTP calls to ship messages to the risk actor’s group chat had been made through the official Telegram API. This isn’t a brand new method and is utilized in numerous phishing kits.
After loading the phishing web page of the PWA, a stack hint is displayed on prime of the display screen (see Determine 15). The stack hint consists of details about the Telegram API and bot token used, and was seen even on the login display screen.
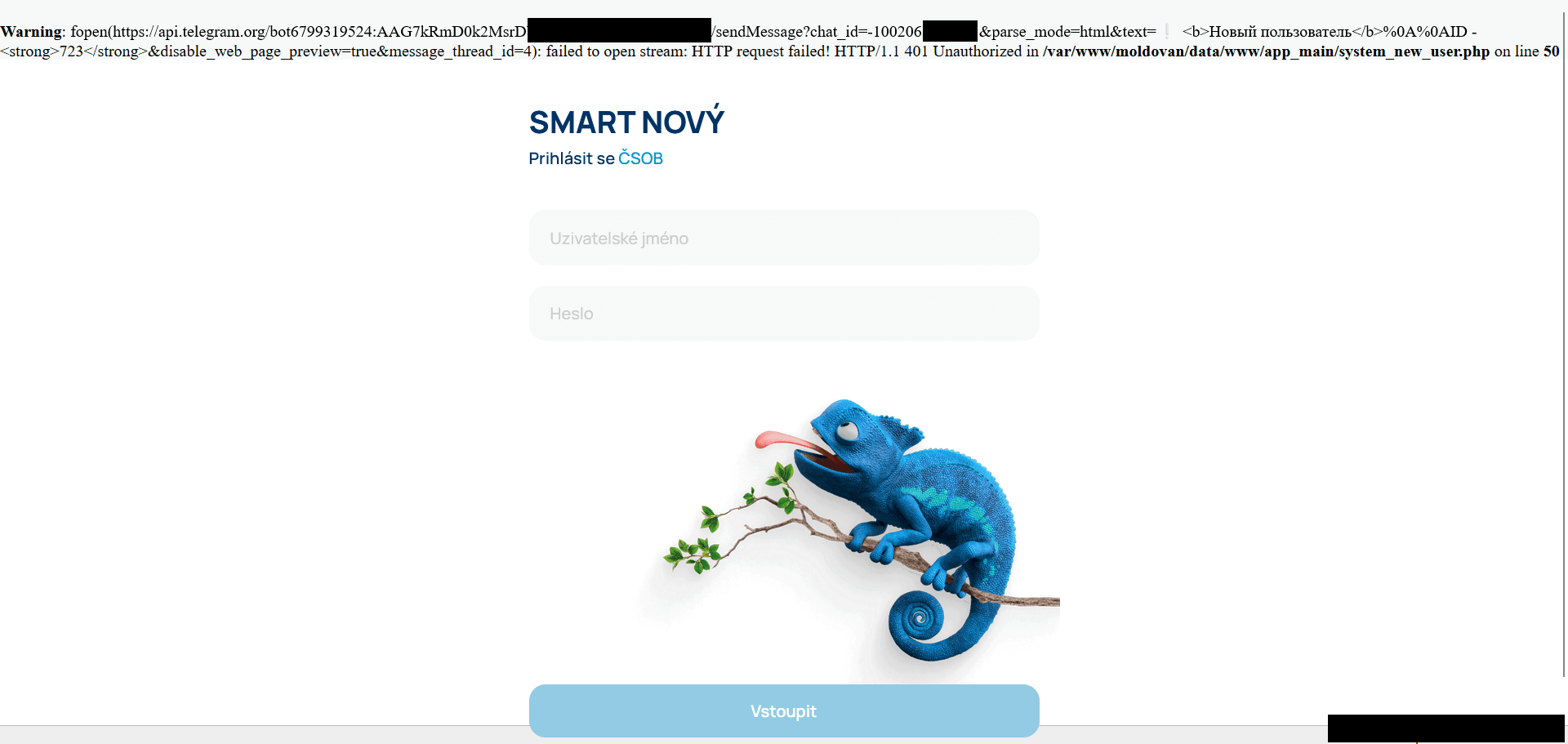
Primarily based on this, we recognized that the risk actor logged all knowledge right into a Telegram group chat. We reported all delicate info of compromised financial institution shoppers to the related banks.
C&C servers
Throughout evaluation of one of many put in PWAs, we observed that entered sufferer knowledge was despatched to a distinct backend server. Upon inspection of the contacted C&C server, we uncovered an operator panel (Determine 16) that included delicate info of victims, at present lively phishing URLs, and a full historical past of visiting victims.
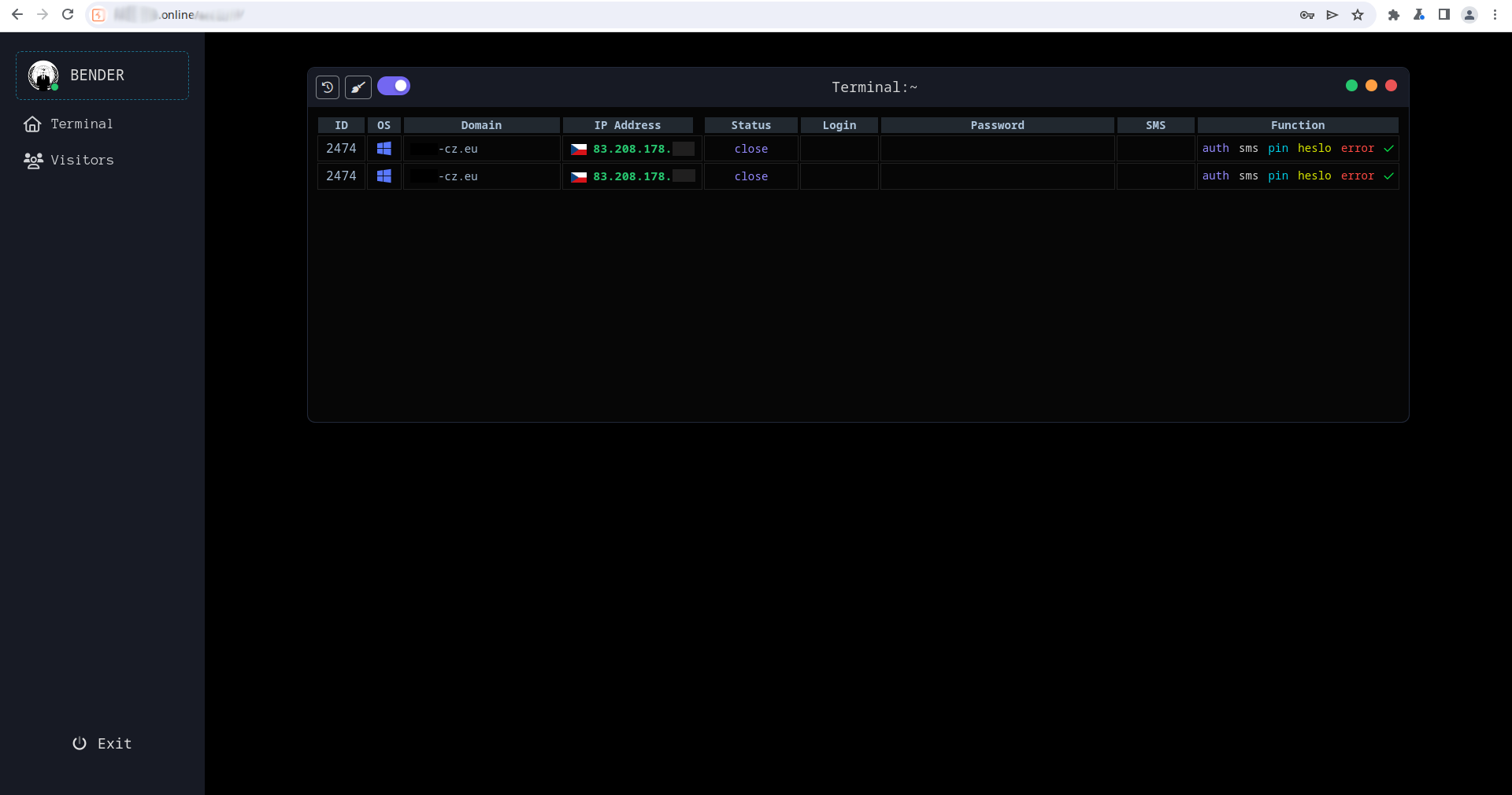
The risk actors didn’t keep put, and after the primary C&C area was deactivated (hide-me[.]on-line) they continued to ascertain extra domains and even ready a very new malicious marketing campaign, operated from the identical panel. The second marketing campaign shall be analyzed in upcoming analysis.
Because of the knowledge recovered from the panel, we had been capable of contact the affected banks and shield the affected shoppers.
Conclusion
We recognized a novel methodology of phishing, combining well-established strategies of social engineering together with the cross-platform know-how of PWA purposes. Instances focusing on Android customers, particularly through a copycat web page of the focused app’s Google Play retailer web page and utilizing WebAPK know-how, had been additionally discovered.
A lot of the identified instances have been inside Czechia, with solely two phishing purposes showing exterior of this area (in Hungary and Georgia).
As a result of two drastically totally different C&C infrastructures had been employed, we’ve decided that two totally different teams are liable for the unfold of the phishing apps.
We count on extra copycat purposes to be created and distributed, since after set up it’s troublesome to separate the reliable apps from the phishing ones.
All delicate info discovered throughout our analysis was promptly despatched to the affected banks for processing. We additionally negotiated the takedowns of a number of phishing domains and C&C servers.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis provides non-public APT intelligence reviews and knowledge feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
Recordsdata
|
SHA-1 |
Filename |
Detection |
Description |
|
D3D5AE6B8AE9C7C1F869 |
base.apk |
Android/Spy.Banker.CIC |
Android cell phishing app |
|
66F97405A1538A74CEE4 |
base.apk |
Android/Spy.Banker.CLW |
Android cell phishing app |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
46.175.145[.]67 |
hide-me[.]on-line |
Cloudflare, Inc. |
2024‑03‑05 |
C&C server. |
|
185.181.165[.]124 |
cyrptomaker[.]information |
NETH LLC |
2024‑02‑21 |
C&C server. |
|
172.67.182[.]151 |
blackrockapp[.]eu |
Cloudflare, Inc. |
2024‑04‑07 |
C&C server. |
|
185.68.16[.]56 |
csas.georgecz[.]on-line |
Internet hosting Ukraine LTD |
2023-11-29 |
Distribution server. |
|
188.114.96[.]9 |
play-protect[.]professional |
Cloudflare, Inc. |
2024-01-18 |
Distribution server. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Preliminary Entry |
Phishing |
Functions are first distributed by malicious promoting or mass phishing. After set up, the applying itself is used for phishing. |
|
|
Credential Entry |
Enter Seize: GUI Enter Seize |
Credentials are harvested by impersonating the login pages of focused banks. |
|
|
Command and Management |
Software Layer Protocol: Net Protocols |
PWA/WebAPK phishing apps ship login knowledge through JavaScript interfaces, in addition to monitoring knowledge. |


