Each group is challenged with appropriately prioritizing new vulnerabilities that have an effect on a big set of third-party libraries used inside their group. The sheer quantity of vulnerabilities revealed every day makes guide monitoring impractical and resource-intensive.
At Databricks, certainly one of our firm aims is to safe our Knowledge Intelligence Platform. Our engineering workforce has designed an AI-based system that may proactively detect, classify, and prioritize vulnerabilities as quickly as they’re disclosed, primarily based on their severity, potential impression, and relevance to Databricks infrastructure. This method permits us to successfully mitigate the chance of important vulnerabilities remaining unnoticed. Our system achieves an accuracy price of roughly 85% in figuring out business-critical vulnerabilities. By leveraging our prioritization algorithm, the safety workforce has considerably diminished their guide workload by over 95%. They’re now in a position to focus their consideration on the 5% of vulnerabilities that require rapid motion, quite than sifting by means of a whole bunch of points.
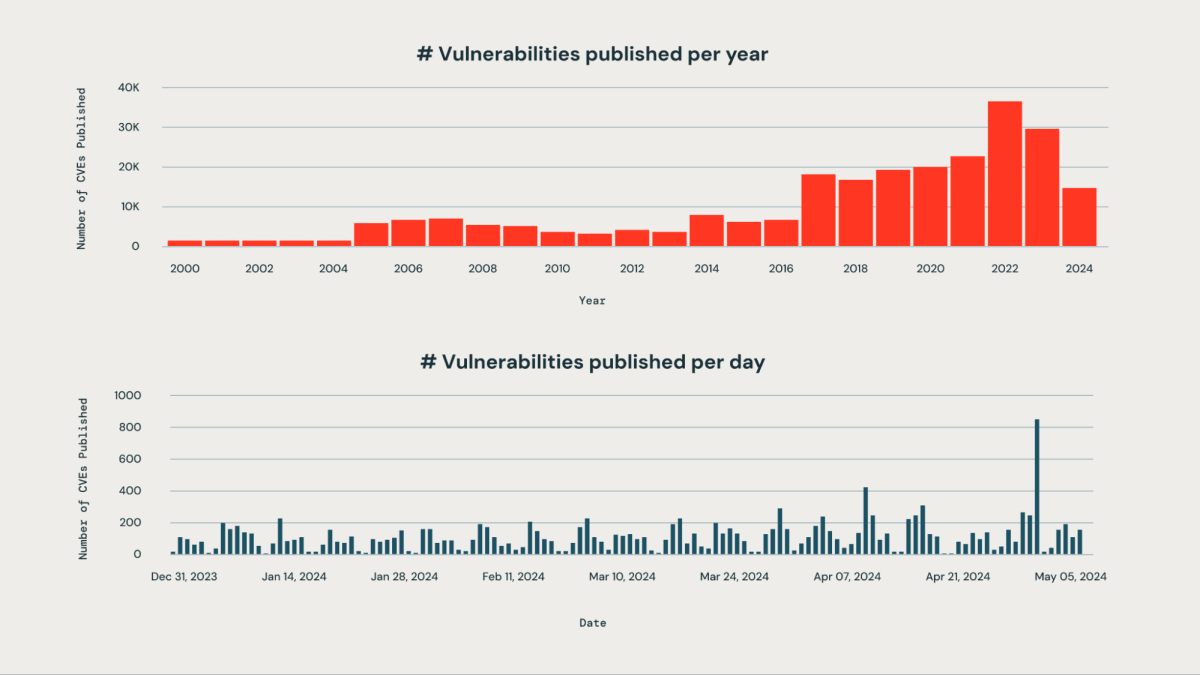
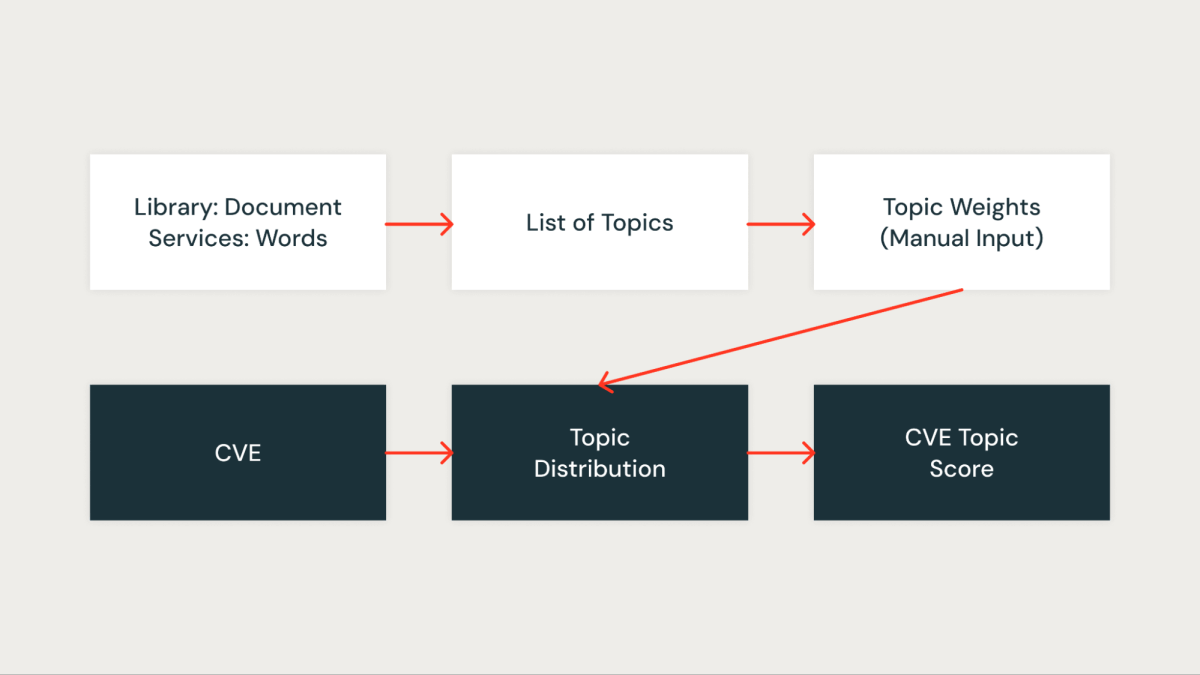
Within the subsequent few steps, we’re going to discover how our AI-driven method helps establish, categorize and rank vulnerabilities.
How Our System Constantly Flags Vulnerabilities
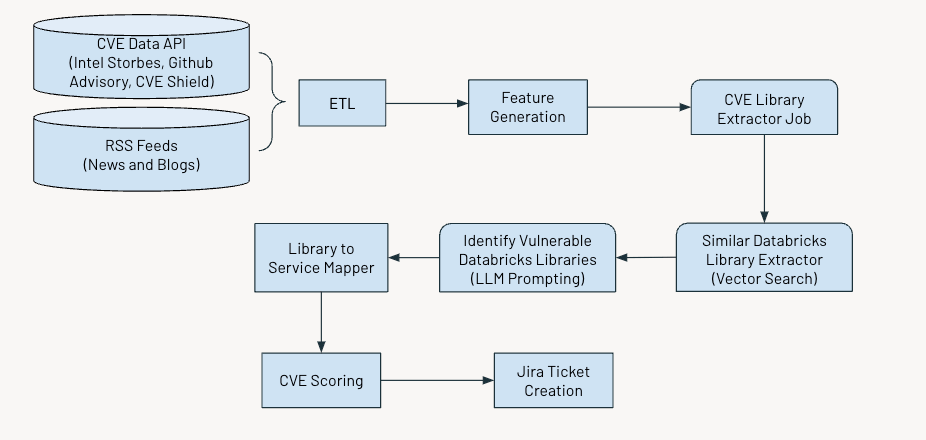
The system operates on a daily schedule to establish and flag important vulnerabilities. The method includes a number of key steps:
- Gathering and processing knowledge
- Producing related options
- Using AI to extract details about Widespread Vulnerabilities and Exposures (CVEs)
- Assessing and scoring vulnerabilities primarily based on their severity
- Producing Jira tickets for additional motion.
The determine under exhibits the general workflow.
Knowledge Ingestion
We ingest Widespread Vulnerabilities and Exposures (CVE) knowledge, which identifies publicly disclosed cybersecurity vulnerabilities from a number of sources equivalent to:
- Intel Strobes API: This offers info and particulars on the software program packages and variations.
- GitHub Advisory Database: Generally, when vulnerabilities are usually not recorded as CVE, they seem as Github advisories.
- CVE Defend: This offers the trending vulnerability knowledge from the latest social media feeds
Moreover, we collect RSS feeds from sources like securityaffairs and hackernews and different information articles and blogs that point out cybersecurity vulnerabilities.
Function Era
Subsequent, we are going to extract the next options for every CVE:
- Description
- Age of CVE
- CVSS rating (Widespread Vulnerability Scoring System)
- EPSS rating (Exploit Prediction Scoring System)
- Influence rating
- Availability of exploit
- Availability of patch
- Trending standing on X
- Variety of advisories
Whereas the CVSS and EPSS scores present priceless insights into the severity and exploitability of vulnerabilities, they might not absolutely apply for prioritization in sure contexts.
The CVSS rating doesn’t absolutely seize a corporation’s particular context or surroundings, which means {that a} vulnerability with a excessive CVSS rating may not be as important if the affected part isn’t in use or is sufficiently mitigated by different safety measures.
Equally, the EPSS rating estimates the likelihood of exploitation however does not account for a corporation’s particular infrastructure or safety posture. Subsequently, a excessive EPSS rating may point out a vulnerability that’s prone to be exploited basically. Nevertheless, it’d nonetheless be irrelevant if the affected programs are usually not a part of the group’s assault floor on the web.
Relying solely on CVSS and EPSS scores can result in a deluge of high-priority alerts, making managing and prioritizing them difficult.
Scoring Vulnerabilities
We developed an ensemble of scores primarily based on the above options – severity rating, part rating and subject rating – to prioritize CVEs, the main points of that are given under.
Severity Rating
This rating helps to quantify the significance of CVE to the broader neighborhood. We calculate the rating as a weighted common of the CVSS, EPSS, and Influence scores. The info enter from CVE Defend and different information feeds permits us to gauge how the safety neighborhood and our peer firms understand the impression of any given CVE. This rating’s excessive worth corresponds to CVEs deemed important to the neighborhood and our group.
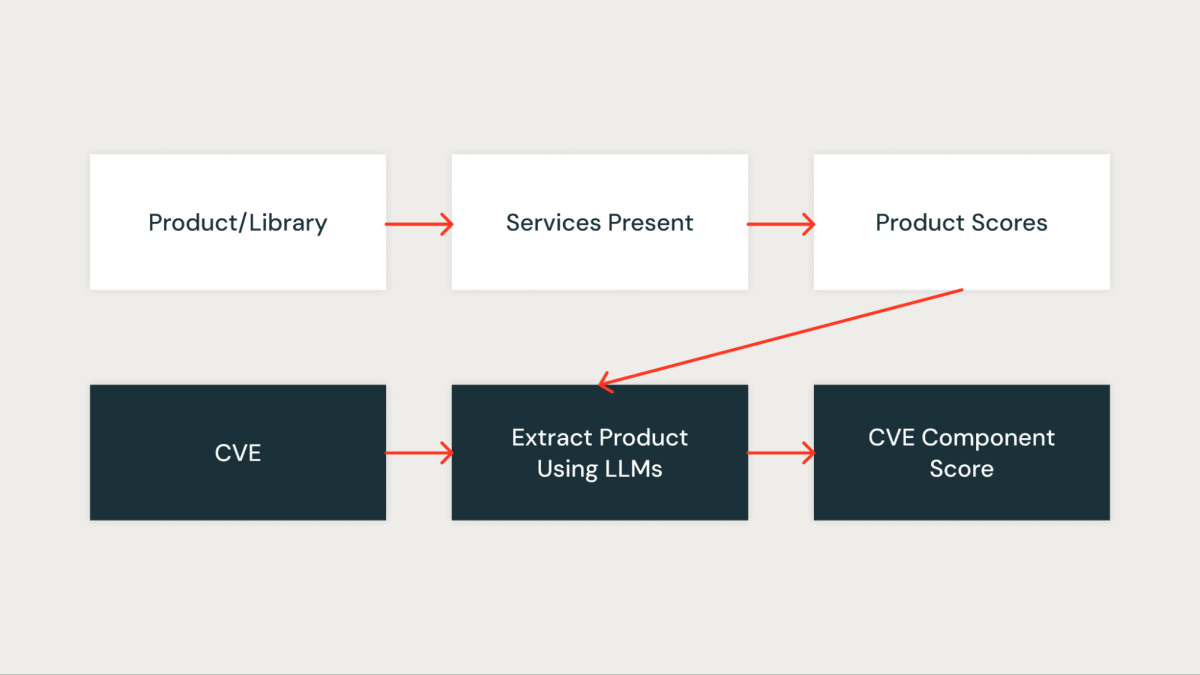
Part Rating
This rating quantitatively measures how vital the CVE is to our group. Each library within the group is first assigned a rating primarily based on the providers impacted by the library. A library that’s current in important providers will get the next rating, whereas a library that’s current in non-critical providers will get a decrease rating.
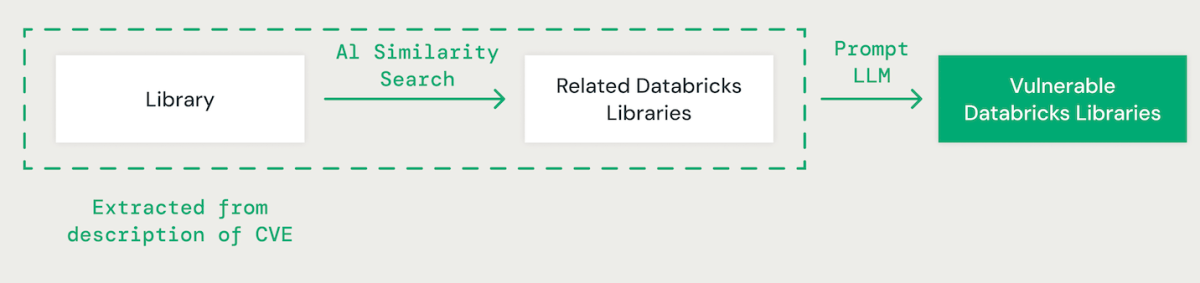
AI-Powered Library Matching
Using few-shot prompting with a big language mannequin (LLM), we extract the related library for every CVE from its description. Subsequently, we make use of an AI-based vector similarity method to match the recognized library with present Databricks libraries. This includes changing every phrase within the library identify into an embedding for comparability.
When matching CVE libraries with Databricks libraries, it is important to know the dependencies between completely different libraries. For instance, whereas a vulnerability in IPython could in a roundabout way have an effect on CPython, a problem in CPython may impression IPython. Moreover, variations in library naming conventions, equivalent to “scikit-learn”, “scikitlearn”, “sklearn” or “pysklearn” should be thought of when figuring out and matching libraries. Moreover, version-specific vulnerabilities ought to be accounted for. For example, OpenSSL variations 1.0.1 to 1.0.1f is perhaps susceptible, whereas patches in later variations, like 1.0.1g to 1.1.1, could deal with these safety dangers.
LLMs improve the library matching course of by leveraging superior reasoning and trade experience. We fine-tuned numerous fashions utilizing a floor fact dataset to enhance accuracy in figuring out susceptible dependent packages.
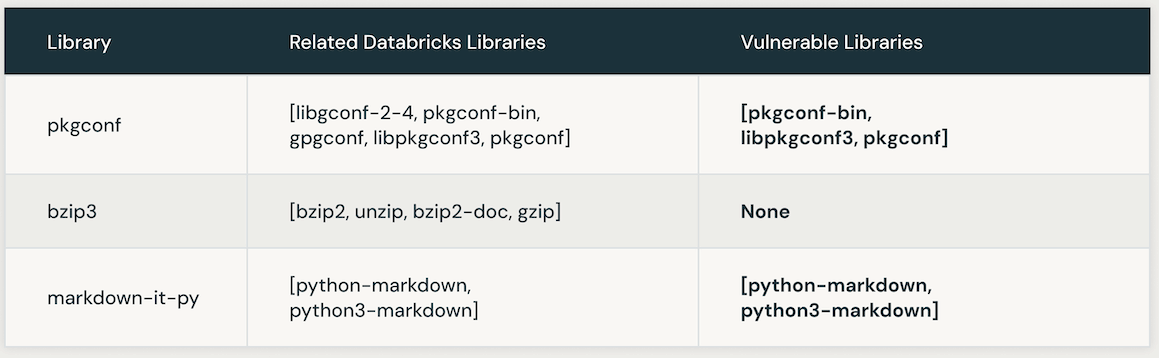
The next desk presents cases of susceptible Databricks libraries linked to a particular CVE. Initially, AI similarity search is leveraged to pinpoint libraries carefully related to the CVE library. Subsequently, an LLM is employed to establish the vulnerability of these related libraries inside Databricks.
Automating LLM Instruction Optimization for Accuracy and Effectivity
Manually optimizing directions in an LLM immediate may be laborious and error-prone. A extra environment friendly method includes utilizing an iterative technique to mechanically produce a number of units of directions and optimize them for superior efficiency on a ground-truth dataset. This technique minimizes human error and ensures a simpler and exact enhancement of the directions over time.
We utilized this automated instruction optimization method to enhance our personal LLM-based answer. Initially, we offered an instruction and the specified output format to the LLM for dataset labeling. The outcomes had been then in contrast in opposition to a floor fact dataset, which contained human-labeled knowledge offered by our product safety workforce.
Subsequently, we utilized a second LLM generally known as an “Instruction Tuner”. We fed it the preliminary immediate and the recognized errors from the bottom fact analysis. This LLM iteratively generated a sequence of improved prompts. Following a overview of the choices, we chosen the best-performing immediate to optimize accuracy.

After making use of the LLM instruction optimization method, we developed the next refined immediate:
Choosing the proper LLM
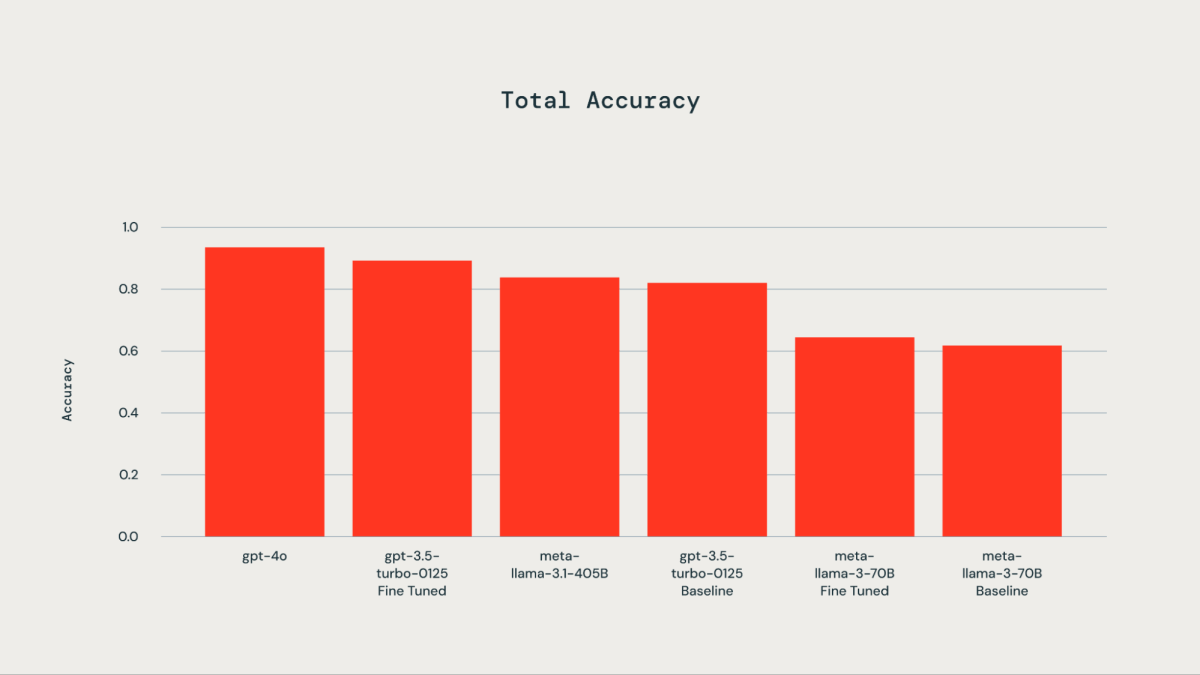
A floor fact dataset comprising 300 manually labeled examples was utilized for fine-tuning functions. The examined LLMs included gpt-4o, gpt-3.5-Turbo, llama3-70B, and llama-3.1-405b-instruct. As illustrated by the accompanying plot, fine-tuning the bottom fact dataset resulted in improved accuracy for gpt-3.5-turbo-0125 in comparison with the bottom mannequin. Advantageous-tuning llama3-70B utilizing the Databricks fine-tuning API led to solely marginal enchancment over the bottom mannequin. The accuracy of the gpt-3.5-turbo-0125 fine-tuned mannequin was akin to or barely decrease than that of gpt-4o. Equally, the accuracy of the llama-3.1-405b-instruct was additionally akin to and barely decrease than that of the gpt-3.5-turbo-0125 fine-tuned mannequin.
As soon as the Databricks libraries in a CVE are recognized, the corresponding rating of the library (library_score as described above) is assigned because the part rating of the CVE.
Subject Rating
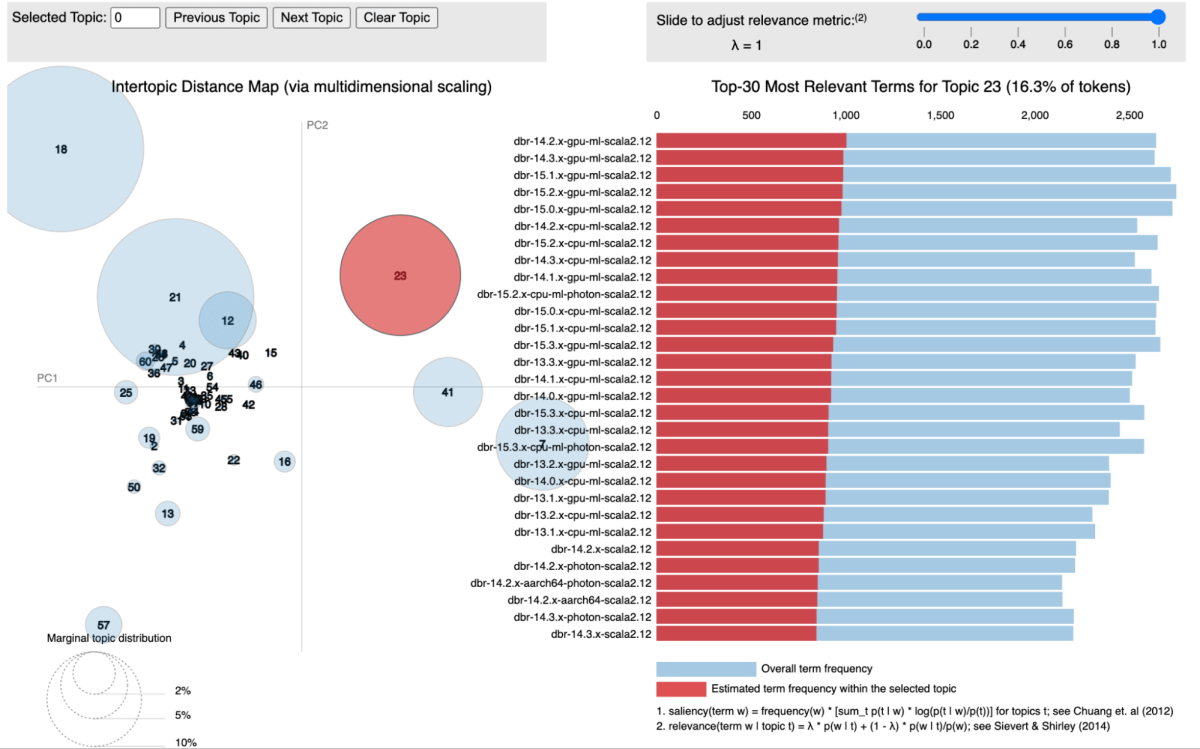
In our method, we utilized subject modeling, particularly Latent Dirichlet Allocation (LDA), to cluster libraries based on the providers they’re related to. Every library is handled as a doc, with the providers it seems in appearing because the phrases inside that doc. This technique permits us to group libraries into matters that signify shared service contexts successfully.
The determine under exhibits a particular subject the place all of the Databricks Runtime (DBR) providers are clustered collectively and visualized utilizing pyLDAvis.
For every recognized subject, we assign a rating that displays its significance inside our infrastructure. This scoring permits us to prioritize vulnerabilities extra precisely by associating every CVE with the subject rating of the related libraries. For instance, suppose a library is current in a number of important providers. In that case, the subject rating for that library will probably be greater, and thus, the CVE affecting it can obtain the next precedence.
Influence and Outcomes
We have now utilized a variety of aggregation strategies to consolidate the scores talked about above. Our mannequin underwent testing utilizing three months’ value of CVE knowledge, throughout which it achieved a powerful true optimistic price of roughly 85% in figuring out CVEs related to our enterprise. The mannequin has efficiently pinpointed important vulnerabilities on the day they’re revealed (day 0) and has additionally highlighted vulnerabilities warranting safety investigation.
To gauge the false negatives produced by the mannequin, we in contrast the vulnerabilities flagged by exterior sources or manually recognized by our safety workforce that the mannequin didn’t detect. This allowed us to calculate the proportion of missed important vulnerabilities. Notably, there have been no false negatives within the back-tested knowledge. Nevertheless, we acknowledge the necessity for ongoing monitoring and analysis on this space.
Our system has successfully streamlined our workflow, remodeling the vulnerability administration course of right into a extra environment friendly and centered safety triage step. It has considerably mitigated the chance of overlooking a CVE with direct buyer impression and has diminished the guide workload by over 95%. This effectivity acquire has enabled our safety workforce to focus on a choose few vulnerabilities, quite than sifting by means of the a whole bunch revealed every day.
Acknowledgments
This work is a collaboration between the Knowledge Science workforce and Product Safety workforce. Thanks to Mrityunjay Gautam Aaron Kobayashi Anurag Srivastava and Ricardo Ungureanu from the Product Safety workforce, Anirudh Kondaveeti Benjamin Ebanks Jeremy Stober and Chenda Zhang from the Safety Knowledge Science workforce.

