In in the present day’s cybersecurity panorama, it’s not nearly having strong defenses—it’s additionally about constructing belief and partnerships with the broader safety neighborhood. One easy however efficient strategy to exhibit this openness is by implementing a safety.txt file. This small addition supplies a transparent, standardized pathway for safety researchers to report vulnerabilities, lowering friction for many who need to assist shield your group. Nevertheless, solely 4% of Fortune 500 corporations at the moment use one, and that absence may very well be sending the mistaken message.
1. A Easy Step with Direct Advantages
The worth of a safety.txt file is rapid and tangible. It creates a single, accessible level of contact for safety researchers who could uncover vulnerabilities and must report them shortly. In a world the place threats evolve always, the very last thing you need is for useful researchers to face hurdles in reaching your safety workforce. It is a low-cost, high-impact strategy to improve your responsiveness and streamline incident reporting.
Even when your organization doesn’t have a proper bug bounty program, a safety.txt file allows you to welcome and act on exterior safety disclosures. It’s about setting the proper tone and exhibiting that your group values safety contributions from exterior its partitions.
2. Balancing Disclosure Rewards: When and Easy methods to Talk
For corporations that do provide rewards for disclosures, a safety.txt file can function a clear strategy to talk program particulars—or sign openness to the opportunity of a reward. In case your bug bounty program is public, embrace it right here to offer researchers rapid readability on how they could be compensated. But when your method is extra versatile, think about a easy assertion like, “Contact for info on disclosure rewards,” which alerts a willingness to debate phrases with out committing to a inflexible construction.
This method enables you to talk curiosity with out limiting choices, permitting researchers to know that their contributions are appreciated, even when a structured reward isn’t outlined.
3. The Absence of Safety.txt: A Missed Alternative for Group Belief
Not having a safety.txt file is greater than a technical omission—it might sign a reluctance to interact with the safety neighborhood. By skipping this straightforward step, corporations can unintentionally talk that they don’t worth the efforts of moral hackers, researchers, and white hats who may assist safe their programs. In a world the place collaboration is essential to a resilient safety posture, that’s a pricey message to ship.
That is very true as your group matures. For corporations with well-developed safety postures (a cumulative rating of two.0 or above on frameworks like NIST or MITRE), the dearth of a safety.txt file turns into tougher to justify. As your safety capabilities develop, think about how this minor addition can improve your fame and replicate a dedication to open, constructive partnerships with the neighborhood.
Conclusion: Strengthening Safety By means of Openness and Belief
Adopting a safety.txt file isn’t nearly making a contact level; it’s a visual demonstration of your group’s perspective towards collaborative safety. Once you create a transparent, open channel for vulnerability reporting, you’re reinforcing a message that moral researchers are welcome and valued. It’s a cheap strategy to foster belief, increase transparency, and align with finest practices in safety governance.
In case your group hasn’t but applied a safety.txt file, think about the message this could be sending. In a time the place belief is paramount, a small step like this will have outsized affect. Don’t let an oversight be mistaken for indifference—take the chance to sign your dedication to safety and neighborhood.
Contemplating including a safety.txt file or need to discover extra methods to strengthen your safety program? Attain out—we’re right here to assist make safety finest practices accessible and actionable to your group.
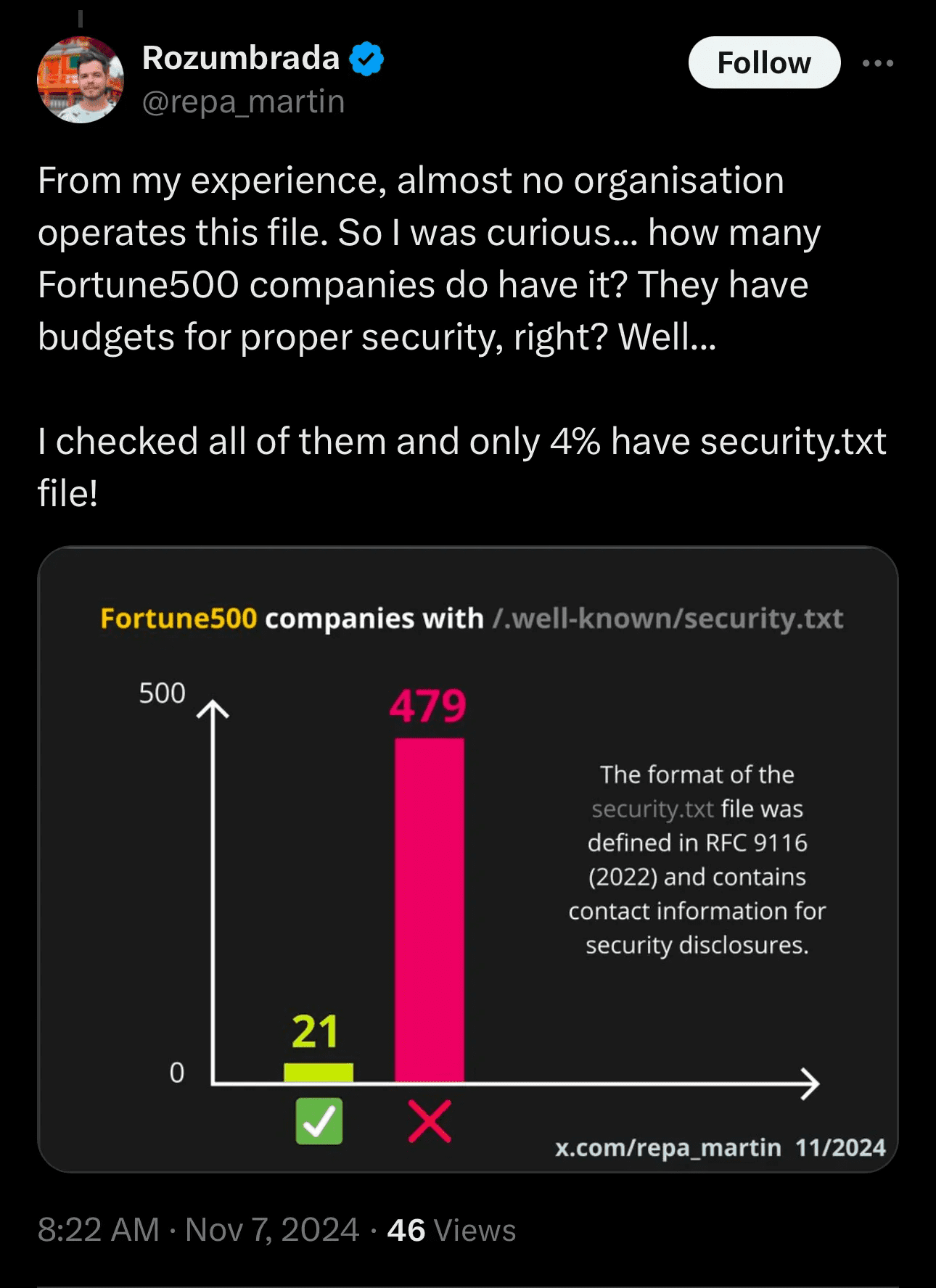
Determine 1. The Twitter Publish that Impressed this Weblog

