
Salesforce has confirmed that it’s going to not negotiate with or pay a ransom to the menace actors behind a large wave of knowledge theft assaults that impacted the corporate’s prospects this 12 months.
As first reported by Bloomberg, Salesforce emailed prospects on Tuesday to say they might not be paying a ransom and warned that “credible menace intelligence” signifies the menace actors had been planning to leak the stolen knowledge.
“I can affirm Salesforce is not going to interact, negotiate with, or pay any extortion demand,” Salesforce additionally confirmed to BleepingComputer.
This assertion follows the launch of a knowledge leak web site by menace actors often known as “Scattered Lapsus$ Hunters,” who’re trying to extort 39 firms whose knowledge was stolen from Salesforce. The web site was situated on the breachforums[.]hn area, which is called after the infamous BreachForums web site, a hacking discussion board recognized for promoting and leaking stolen knowledge.
The businesses being extorted on the information leak web site included well-known manufacturers and organizations, together with FedEx, Disney/Hulu, House Depot, Marriott, Google, Cisco, Toyota, Hole, Kering, McDonald’s, Walgreens, Instacart, Cartier, Adidas, Sake Fifth Avenue, Air France & KLM, Transunion, HBO MAX, UPS, Chanel, and IKEA.
In whole, the menace actors claimed to have stolen almost 1 billion knowledge information, which might be publicly launched if an extortion demand was paid by particular person firms or as a single cost from Salesforce that will cowl all of the impacted prospects listed on the location.
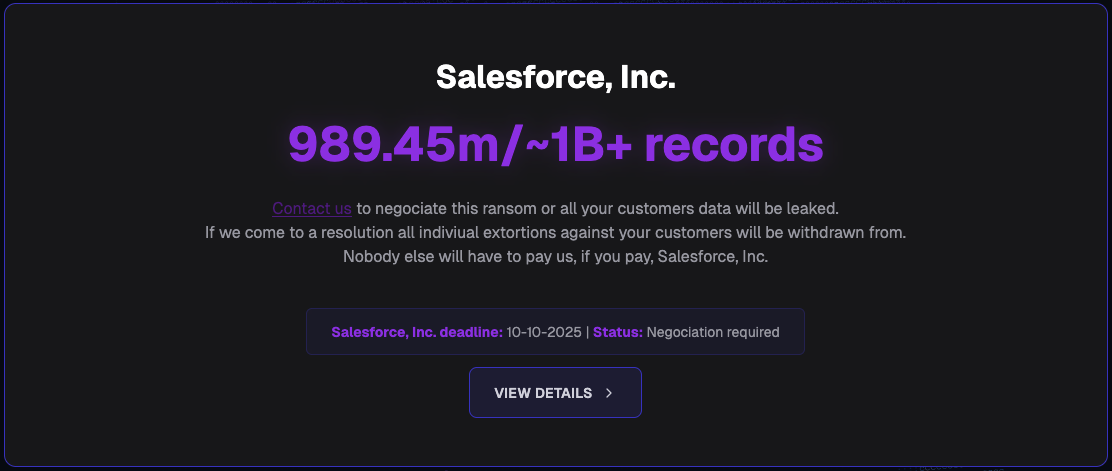
Supply: BleepingComputer
This knowledge was stolen from Salesforce cases in two separate campaigns that occurred in 2025.
The primary knowledge theft marketing campaign started on the finish of 2024, when menace actors began conducting social engineering assaults impersonating IT help workers to trick staff into connecting a malicious OAuth utility to their firm’s Salesforce occasion.
As soon as linked, the menace actors used the connection to obtain and steal the databases, which had been then used to extort the corporate via e mail.
These social engineering assaults impacted Google, Cisco, Qantas, Adidas, Allianz Life, Farmers Insurance coverage, Workday, Kering, and LVMH subsidiaries, resembling Dior, Louis Vuitton, and Tiffany & Co.
A second Salesforce data-theft marketing campaign started in early August 2025, when the menace actors used stolen SalesLoft Drift OAuth tokens to pivot to prospects’ CRM environments and exfiltrate knowledge.
The Salesloft data-theft assaults primarily centered on stealing help ticket knowledge to scan for credentials, API tokens, authentication tokens, and different delicate info that will allow the attackers to breach the corporate’s infrastructure and cloud companies.
One of many menace actors behind the Salesloft assaults, often known as ShinyHunters, informed BleepingComputer that they stole roughly 1.5 billion knowledge information for over 760 firms throughout this marketing campaign.
Many firms have already confirmed they had been impacted by the Salesloft supply-chain assault, together with Google, Cloudflare, Zscaler, Tenable, CyberArk, Elastic, BeyondTrust, Proofpoint, JFrog, Nutanix, Qualys, Rubrik, Cato Networks, Palo Alto Networks, and many extra.
The not too long ago launched knowledge leak web site was used primarily to extort prospects within the unique social engineering assaults, with the menace actors stating they might start publicly extorting these impacted by the Salesloft assaults after October tenth.
Nonetheless, the information leak web site is now shut down, with the area now utilizing nameservers of surina.ns.cloudflare.com and hans.ns.cloudflare.com, which have each been utilized by the FBI previously when seizing domains.
BleepingComputer contacted the FBI about whether or not they seized the area however has not acquired a response right now.


