At Databricks, we all know that information is one in every of your most respected belongings. Our product and safety groups work collectively to ship an enterprise-grade Knowledge Intelligence Platform that allows you to defend in opposition to safety dangers and meet your compliance obligations. Over the previous 12 months, we’re proud to have delivered new capabilities and assets corresponding to securing information entry with Azure Non-public Hyperlink for Databricks SQL Serverless, protecting information personal with Azure firewall assist for Workspace storage, defending information in-use with Azure confidential computing, reaching FedRAMP Excessive Company ATO on AWS GovCloud, publishing the Databricks AI Safety Framework, and sharing particulars on our strategy to Accountable AI.
In keeping with the 2024 Verizon Knowledge Breach Investigations Report, the variety of information breaches has elevated by 30% since final 12 months. We imagine it’s essential so that you can perceive and appropriately make the most of our safety features and undertake really useful safety finest practices to mitigate information breach dangers successfully.
On this weblog, we’ll clarify how one can leverage a few of our platform’s prime controls and not too long ago launched safety features to determine a strong defense-in-depth posture that protects your information and AI belongings. We may also present an summary of our safety finest practices assets so that you can stand up and operating rapidly.
Shield your information and AI workloads throughout the Databricks Knowledge Intelligence Platform
The Databricks Platform offers safety guardrails to defend in opposition to account takeover and information exfiltration dangers at every entry level. Within the under picture, we define a typical lakehouse structure on Databricks with 3 surfaces to safe:
- Your shoppers, customers and functions, connecting to Databricks
- Your workloads connecting to Databricks companies (APIs)
- Your information being accessed out of your Databricks workloads
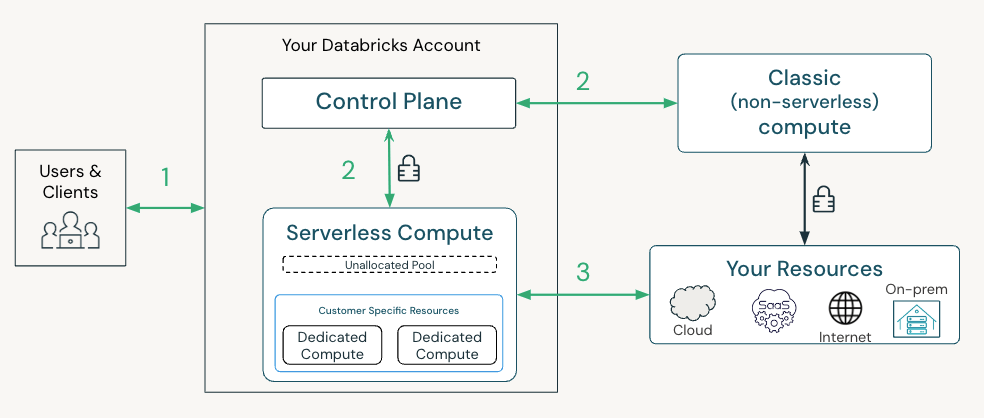
Let’s now stroll by at a excessive stage a number of the prime controls—both enabled by default or accessible so that you can activate—and new safety capabilities for every connection level. Our full checklist of suggestions primarily based on completely different menace fashions might be present in our safety finest follow guides.
Connecting customers and functions into Databricks (1)
To guard in opposition to access-related dangers, you need to use a number of elements for each authentication and authorization of customers and functions into Databricks. Utilizing solely passwords is insufficient as a consequence of their susceptibility to theft, phishing, and weak person administration. Actually, as of July 10, 2024, Databricks-managed passwords reached the end-of-life and are not supported within the UI or through API authentication. Past this extra default safety, we advise you to implement the under controls:
- Authenticate through single-sign-on on the account stage for all person entry (AWS, SSO is robotically enabled on Azure/GCP)
- Leverage multi-factor authentication supplied by your IDP to confirm all customers and functions which are accessing Databricks (AWS, Azure, GCP)
- Allow unified login for all workspaces utilizing a single account-level SSO and configure SSO Emergency entry with MFA for streamlined and safe entry administration (AWS, Databricks integrates with built-in identification suppliers on Azure/GCP)
- Use front-end personal hyperlink on workspaces to limit entry to trusted personal networks (AWS, Azure, GCP)
- Configure IP entry lists on workspaces and on your account to solely permit entry from trusted community areas, corresponding to your company community (AWS, Azure, GCP)
Connecting your workloads to Databricks companies (2)
To stop workload impersonation, Databricks authenticates workloads with a number of credentials throughout the lifecycle of the cluster. Our suggestions and accessible controls rely in your deployment structure. At a excessive stage:
- For Traditional clusters that run in your community, we advocate configuring a back-end personal hyperlink between the compute aircraft and the management aircraft. Configuring the back-end personal hyperlink ensures that your cluster can solely be authenticated over that devoted and personal channel.
- For Serverless, Databricks robotically offers a defense-in-depth safety posture on our platform utilizing a mix of application-level credentials, mTLS shopper certificates and personal hyperlinks to mitigate in opposition to Workspace impersonation dangers.
Connecting from Databricks to your storage and information sources (3)
To make sure that information can solely be accessed by the correct person and workload on the correct Workspace, and that workloads can solely write to approved storage areas, we advocate leveraging the next options:
- Utilizing Unity Catalog to manipulate entry to information: Unity Catalog offers a number of layers of safety, together with fine-grained entry controls and time-bound down-scoped credentials which are solely accessible to trusted code by default.
- Leverage Mosaic AI Gateway: Now in Public Preview, Mosaic AI Gateway means that you can monitor and management the utilization of each exterior fashions and fashions hosted on Databricks throughout your enterprise.
- Configuring entry from approved networks: You may configure entry insurance policies utilizing S3 bucket insurance policies on AWS, Azure storage firewall and VPC Service Controls on GCP.
- With Traditional clusters, you possibly can lock down entry to your community through the above-listed controls.
- With Serverless, you possibly can lock down entry to the Serverless community (AWS, Azure) or to a devoted personal endpoint on Azure. On Azure, now you can allow the storage firewall on your Workspace storage (DBFS root) account.
- Assets exterior to Databricks, corresponding to exterior fashions or storage accounts, might be configured with devoted and personal connectivity. Here’s a deployment information for accessing Azure OpenAI, one in every of our most requested situations.
- Configuring egress controls to forestall entry to unauthorized storage areas: With Traditional clusters, you possibly can configure egress controls in your community. With SQL Serverless, Databricks doesn’t permit web entry from untrusted code corresponding to Python UDFs. To find out how we’re enhancing egress controls as you undertake extra Serverless merchandise, please this manner to affix our previews.
The diagram under outlines how one can configure a personal and safe atmosphere for processing your information as you undertake Databricks Serverless merchandise. As described above, a number of layers of safety can shield all entry to and from this atmosphere.
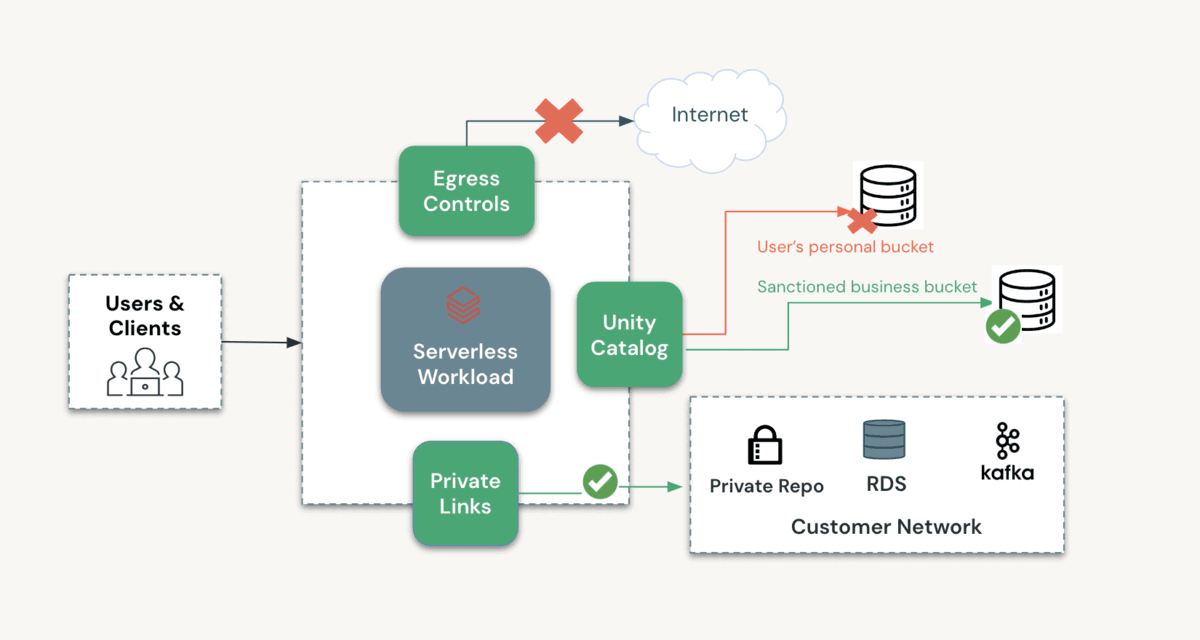
Outline, deploy and monitor your information and AI workloads with industry-leading safety finest practices
Now that we have now outlined a set of key controls accessible to you, you in all probability are questioning how one can rapidly operationalize them for your enterprise. Our Databricks Safety group recommends taking a “outline, deploy, and monitor” strategy utilizing the assets they’ve developed from their expertise working with a whole lot of consumers.
- Outline: You need to configure your Databricks atmosphere by reviewing our greatest practices together with the dangers particular to your group. We have crafted complete finest follow guides for Databricks deployments on all three main clouds. These paperwork supply a guidelines of safety practices, menace fashions, and patterns distilled from our enterprise engagements.
- Deploy: Terraform templates make deploying safe Databricks workspaces straightforward. You may programmatically deploy workspaces and the required cloud infrastructure utilizing the official Databricks Terraform supplier. These unified Terraform templates are preconfigured with hardened safety settings just like these utilized by our most security-conscious clients. View our GitHub to get began on AWS, Azure, and GCP.
- Monitor: The Safety Evaluation Software (SAT) can be utilized to observe adherence to safety finest practices in Databricks workspaces on an ongoing foundation. We not too long ago upgraded the SAT to streamline setup and improve checks, aligning them with the Databricks AI Safety Framework (DASF) for improved protection of AI safety dangers.
Keep forward in information and AI safety
The Databricks Knowledge Intelligence Platform offers an enterprise-grade defense-in-depth strategy for safeguarding information and AI belongings. For suggestions on mitigating safety dangers, please seek advice from our safety finest practices guides on your chosen cloud(s). For a summarized guidelines of controls associated to unauthorized entry, please seek advice from this doc.
We constantly improve our platform primarily based in your suggestions, evolving {industry} requirements, and rising safety threats to higher meet your wants and keep forward of potential dangers. To remain knowledgeable, bookmark our Safety and Belief weblog, head over to our YouTube channel, and go to the Databricks Safety and Belief Middle.

