The 2024 vacation season revealed a posh and evolving risk panorama for Distributed Denial-of-Service (DDoS) assaults. This yr’s developments included superior ways reminiscent of a rise in DDoS-for-hire operations, the meeting of huge DDoS botnets by script kiddies, politically motivated assault campaigns, and the bypass of CDN (Content material Supply Community) protections amongst different evolving threats.
The 2024 vacation season revealed a posh and evolving risk panorama for Distributed Denial-of-Service (DDoS) assaults. This yr’s developments included superior ways reminiscent of a rise in DDoS-for-hire operations, the meeting of huge DDoS botnets by script kiddies, politically motivated assault campaigns, and the bypass of CDN (Content material Supply Community) protections amongst different evolving threats.
The 2024 vacation season assault panorama in Azure
In the course of the vacation season, we famous a shift in assault patterns from final yr, highlighting how malicious actors repeatedly refine their ways to bypass DDoS safety.
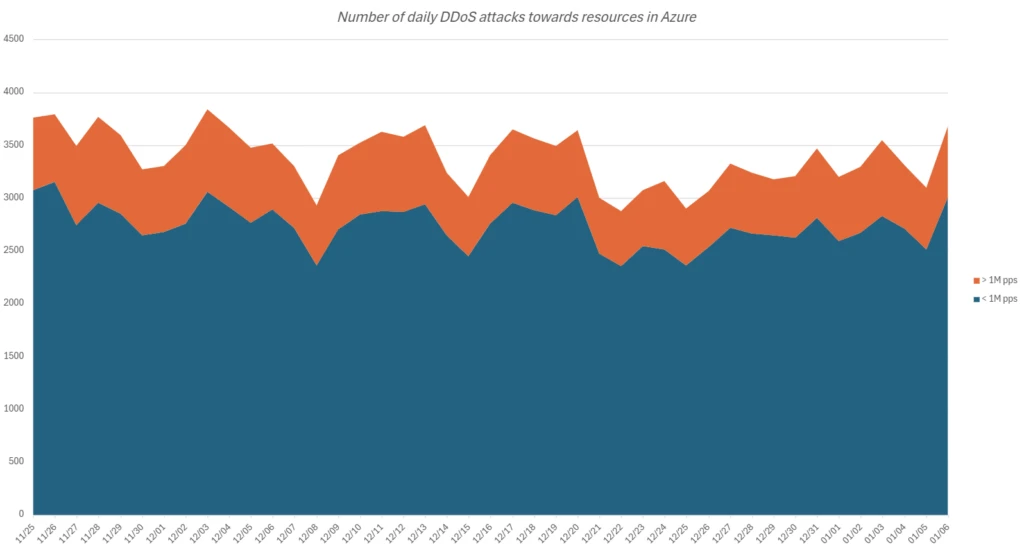
Every day assault quantity
Azure’s safety infrastructure mitigates as much as 3,800 assaults day by day. Giant-scale assaults over a million packets per second (pps) make up about 20% of those, just like final yr’s evaluation. Extremely volumetric assaults exceeding 10M pps are uncommon, at simply 0.2% of all assaults, reflecting attackers’ goal to reduce assets and keep away from detection.
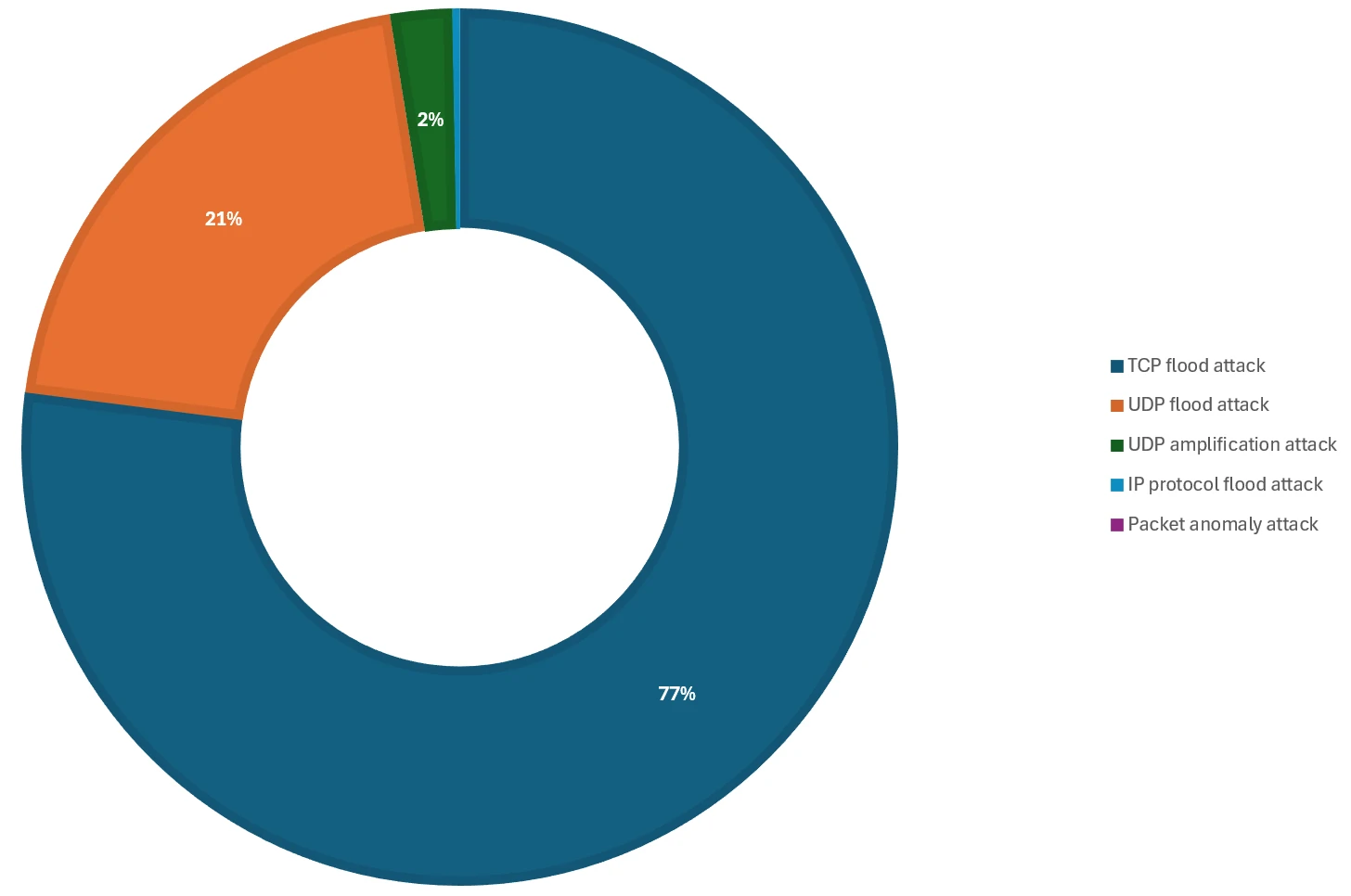
Assault protocols
The 2024 vacation season noticed a predominant use of TCP-based assaults (Transport Management Protocol), concentrating on numerous internet purposes and assets, accounting for 77% of the assaults. That is in distinction to final yr when UDP-based assaults (Person Datagram Protocol) accounted for practically 80% of the assaults on gaming and different assets. The principle TCP assault vectors this yr have been TCP SYN (Synchronize) and ACK (Acknowledge) floods.
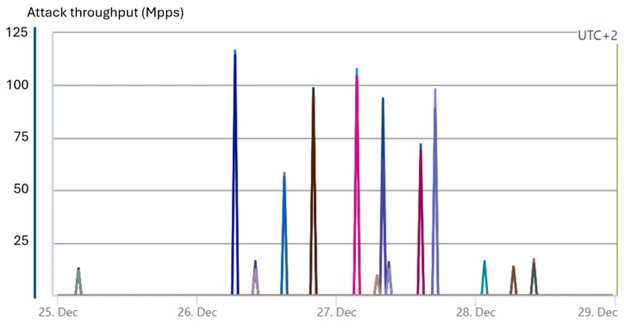
Azure blocks huge typhon assault
A staggering assault on gaming assets reached 100-125 million pps in a number of waves. This assault, whose signatures hyperlink to Typhon botnet, was totally mitigated by Azure’s defenses.
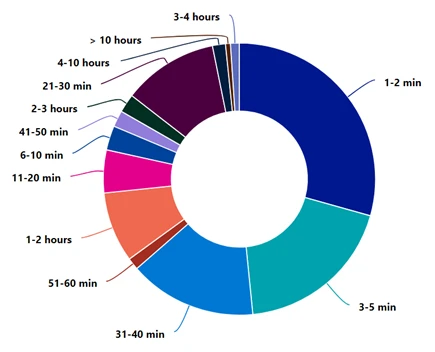
Assaults period
This vacation season once more we witnessed the identical adversaries’ ways of making an attempt to bypass DDoS mitigation methods by launching burst or short-lived assaults. 49% of all assaults lasted as much as 5 minutes, whereas 83% of assaults lasted lower than 40 minutes. It’s insightful to know that any DDoS mitigation countermeasure we implement to guard our software ought to kick in efficient mitigation as quickly as potential.
Political motives and DDoS-for-hire surge
This vacation season, Azure’s assault developments mirror world patterns. Politically motivated assaults, pushed by geopolitical tensions, persist. DDoS threats stay a big concern as new actors use accessible instruments to trigger disruption.
The rise of DDoS-for-hire companies, also known as stressers and booters, has gained vital recognition amongst attackers. These platforms, that are readily accessible on cybercriminal boards, have democratized the potential to launch sturdy DDoS assaults, making them attainable for much less subtle criminals at minimal prices. Lately, there was a rise in each the provision and utilization of those companies. Throughout this vacation season, worldwide legislation enforcement businesses performed operations reminiscent of Operation PowerOFF final December, ensuing within the arrest of three people and the shutdown of 27 domains related to DDoS-for-hire platforms. Regardless of these efforts, DDoS stressers proceed to thrive, providing a wide range of assault strategies and energy, and are more likely to persist of their prevalence.
Making ready for 2025
The 2024 vacation season has emphasised the continued risk of DDoS assaults. Organizations should improve their cybersecurity methods to counter these evolving threats within the new yr. Strengthening defenses and staying vigilant to new ways is essential in 2025. Azure’s resilience in opposition to superior DDoS threats highlights the significance of strong safety measures for safeguarding digital property and guaranteeing enterprise continuity.
Figuring out publicity factors
Begin by pinpointing which of your purposes are uncovered to the general public web. Evaluating the potential dangers and vulnerabilities of those purposes is essential to understanding the place it’s possible you’ll be most inclined to assaults.
Recognizing regular operations
Familiarize your self with the traditional conduct of your purposes. Azure offers monitoring companies and greatest practices that can assist you achieve insights into the well being of your purposes and diagnose points successfully.
Simulating assault eventualities
Frequently working assault simulations is an efficient option to check your companies’ responses to potential DDoS assaults. Throughout testing, validate that your companies or purposes proceed to operate as anticipated and that there’s no disruption to the consumer expertise. Establish gaps from each a know-how and course of standpoint and incorporate them into your DDoS response technique.
Making certain sturdy safety
With the excessive threat of DDoS assaults, it’s important to have a DDoS safety service like Azure DDoS Safety. This service offers always-on visitors monitoring, computerized assault mitigation upon detection, adaptive real-time tuning, and full visibility of DDoS assaults with real-time telemetry, monitoring, and alerts.
Implementing layered safety
For complete safety, arrange a multi-layered protection by deploying Azure DDoS Safety with Azure Net Utility Firewall (WAF). Azure DDoS Safety secures the community layer (Layer 3 and 4), whereas Azure WAF safeguards the appliance layer (Layer 7). This mixture ensures safety in opposition to numerous varieties of DDoS assaults.
Configuring alerts
Azure DDoS Safety can determine and mitigate assaults with out consumer intervention. Configuring alerts for energetic mitigations can maintain you knowledgeable in regards to the standing of protected public IP assets.
Formulating a response plan
Set up a DDoS response group with clearly outlined roles and duties. This group must be adept at figuring out, mitigating, and monitoring an assault, in addition to coordinating with inside stakeholders and clients. Use simulation testing to determine any gaps in your response technique, guaranteeing your group is ready for numerous assault eventualities.
Looking for skilled help
Within the occasion of an assault, reaching out to technical professionals is significant. Azure DDoS Safety clients have entry to the DDoS Speedy Response (DRR) group for help throughout and after assaults. Following an assault, proceed monitoring assets and conduct a retrospective evaluation. Apply learnings to enhance your DDoS response technique, guaranteeing higher preparedness for future incidents.
Name to motion
The 2024 vacation season highlighted the evolving risk panorama of DDoS assaults, with a big enhance in DDoS-for-hire operations, huge botnets, and politically motivated campaigns. These threats emphasize the necessity for sturdy DDoS safety and a DDoS response plan. Azure helps organizations to remain forward of those threats. Prospects ought to allow multi-layer safety by deploying Azure DDoS Safety with Azure Net Utility Firewall (WAF). Moreover, clients ought to allow telemetry and alerting capabilities to observe and reply to energetic mitigations successfully.

