A brand new report from cybersecurity firm Netskope reveals particulars about assault campaigns abusing Microsoft Sway and CloudFlare Turnstile and leveraging QR codes to trick customers into offering their Microsoft Workplace credentials to the phishing platform.
These campaigns have focused victims in Asia and North America throughout a number of segments led by expertise, manufacturing, and finance.
What’s quishing?
QR codes are a handy technique to browse web sites or entry info with out the necessity to enter any URL on a smartphone. However there’s a threat in utilizing QR codes: cybercriminals would possibly abuse them to guide victims to malicious content material.
This course of, known as “quishing,” entails redirecting victims to malicious web sites or prompting them to obtain dangerous content material by scanning a QR code. As soon as on the location, cybercriminals work to steal your private and monetary info. The design of QR codes makes it not possible for the person to know the place the code will direct them after scanning.
Thomas Damonneville, head of anti-phishing firm StalkPhish, informed TechRepublic that quishing “is a rising development” that “may be very simple to make use of and makes it more durable to examine if the content material is authentic.”
Quishing assaults by way of Microsoft Sway
In July 2024, Netskope Menace Labs found a 2000-fold improve in visitors to phishing pages by way of Microsoft Sway. Nearly all of the malicious pages used QR codes.
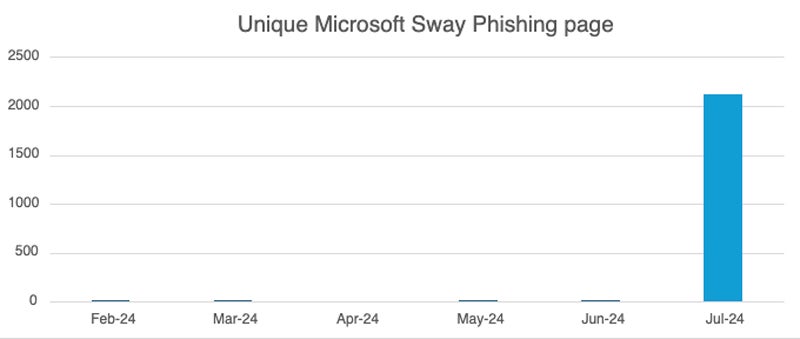
Microsoft Sway is a web based app from Microsoft Workplace that comes free and allows customers to simply create shows or different web-based content material. The app being freed from cost makes it a sexy goal for cybercriminals.
Within the assault campaigns uncovered by Netskope’s researcher Jan Michael Alcantara, victims are being focused with Microsoft Sway pages that result in phishing makes an attempt for Microsoft Workplace credentials.
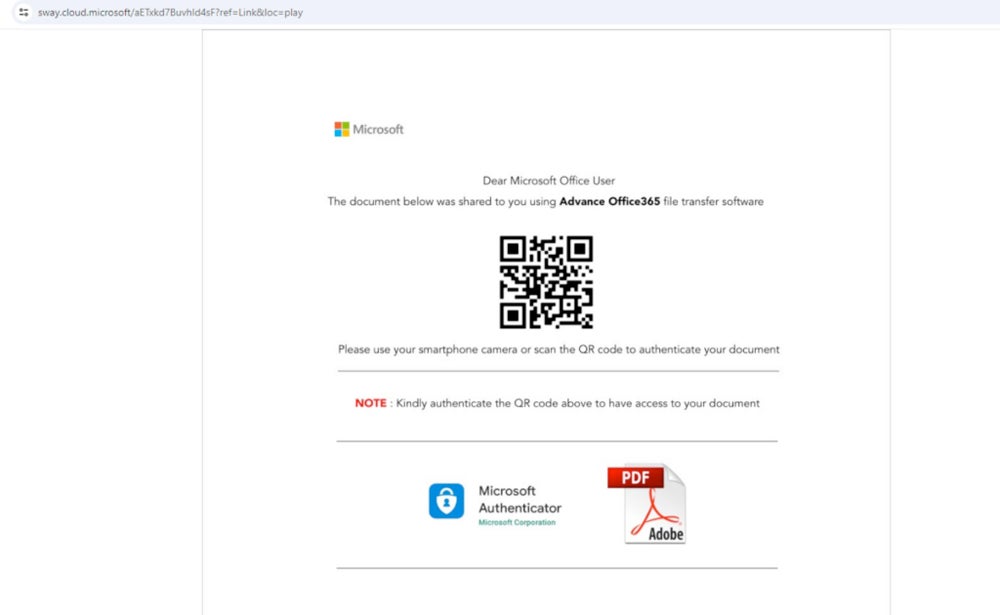
Netskope’s analysis doesn’t point out how the fraudulent hyperlinks had been despatched to victims. Nonetheless, it’s potential to unfold these hyperlinks by way of e mail, social networks, SMS, or prompt messaging software program.
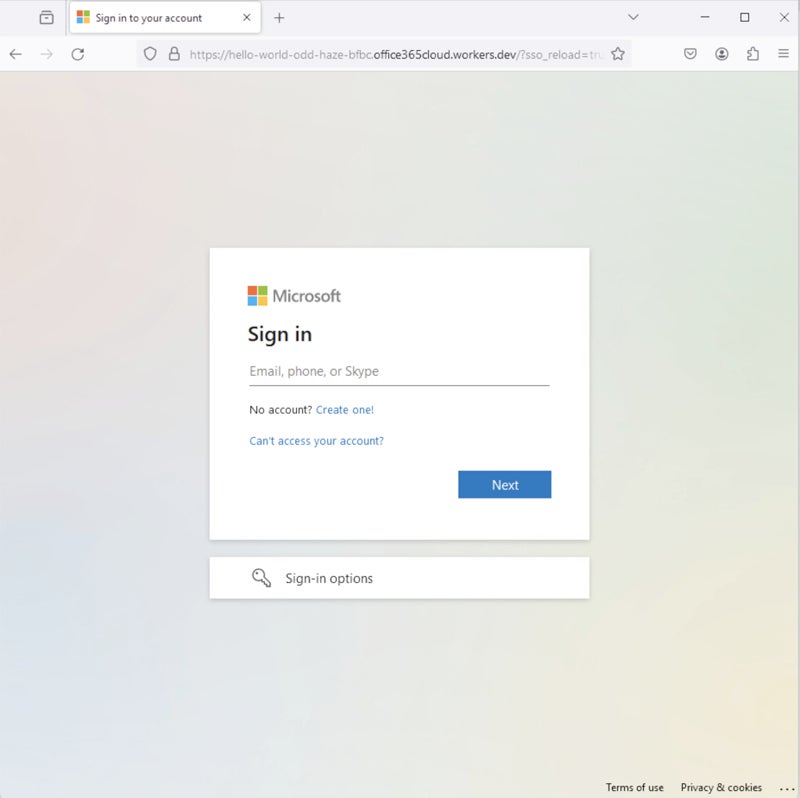
The ultimate payload appears to be like just like the authentic Microsoft Workplace login web page, as uncovered in a Might 2024 publication from the identical researcher.
Stealthier assault utilizing CloudFlare Turnstile
CloudFlare’s Turnstile is a free instrument that replaces captchas, which have been exploited in reported assault campaigns. This authentic service permits web site house owners to simply add the mandatory Turnstile code to their content material, enabling customers to easily click on on a verification code as a substitute of fixing a captcha.

From an attacker perspective, utilizing this free instrument is interesting as a result of it requires customers to click on on a CloudFlare Turnstile earlier than being redirected to the phishing web page. This provides a layer of safety in opposition to detection for the attacker, as the ultimate phishing payload is hid from on-line URL scanners.
Attacker-in-the-middle phishing method
Conventional phishing methods sometimes gather credentials earlier than displaying an error web page or redirecting the person to the authentic login web page. This method makes customers consider they’ve entered incorrect credentials, probably leaving them unaware of the fraud.
The attacker-in-the-middle phishing method is extra discreet. The person’s credentials are collected and instantly used to log into the authentic service. This methodology, additionally known as clear phishing, permits the person to be efficiently logged after the fraudulent credential theft, making the assault much less noticeable.
Malicious QR code detection difficulties
“No person can learn a QR code along with his personal eyes,” Damonneville stated. “You may solely scan it with the suitable system, a smartphone. Some hyperlinks may be so lengthy that you would be able to’t examine the entire hyperlink, when you examine it … However who checks hyperlinks?”
Textual content-only-based detections are additionally ineffective in opposition to QR codes as they’re photos. There’s additionally no widespread customary for verifying the authenticity of a QR code. Safety mechanisms similar to digital signatures for QR codes should not generally applied, making it troublesome to confirm the supply or integrity of the content material.
How will you stop a QR code from phishing?
Many QR code readers present a preview of the URL, although, enabling customers to see the URL earlier than scanning it. Any suspicion on the URL ought to entice the person to not use the QR code. Moreover:
- QR codes resulting in actions similar to login or present info ought to elevate suspicion and needs to be fastidiously analyzed.
- Safety options additionally would possibly assist, as they will detect phishing URLs. URLs ought to at all times be scanned by such a instrument.
- Funds shouldn’t be executed by way of QR code until you’re assured that it’s authentic.
Microsoft Sway is just not the one authentic product that is likely to be used by cybercriminals to host phishing pages.
“We often observe authentic websites or purposes getting used to host quishing or phishing, together with Github, Gitbooks or Google Docs, for instance, every day,” Damonneville stated. “To not point out all of the URL shorteners available on the market, or free internet hosting websites, broadly used to cover a URL simply.”
This as soon as once more enforces the concept that customers’ consciousness must be raised and workers have to be educated to differentiate a suspicious URL from a authentic one.
Disclosure: I work for Pattern Micro, however the views expressed on this article are mine.

