For the previous week, the huge “Web of Issues” (IoT) botnet referred to as Kimwolf has been disrupting The Invisible Web Venture (I2P), a decentralized, encrypted communications community designed to anonymize and safe on-line communications. I2P customers began reporting disruptions within the community across the similar time the Kimwolf botmasters started counting on it to evade takedown makes an attempt in opposition to the botnet’s management servers.
Kimwolf is a botnet that surfaced in late 2025 and rapidly contaminated thousands and thousands of programs, turning poorly secured IoT gadgets like TV streaming bins, digital image frames and routers into relays for malicious site visitors and abnormally giant distributed denial-of-service (DDoS) assaults.
I2P is a decentralized, privacy-focused community that enables individuals to speak and share data anonymously.
“It really works by routing knowledge by a number of encrypted layers throughout volunteer-operated nodes, hiding each the sender’s and receiver’s areas,” the I2P web site explains. “The result’s a safe, censorship-resistant community designed for personal web sites, messaging, and knowledge sharing.”
On February 3, I2P customers started complaining on the group’s GitHub web page about tens of 1000’s of routers immediately overwhelming the community, stopping current customers from speaking with reputable nodes. Customers reported a quickly rising variety of new routers becoming a member of the community that had been unable to transmit knowledge, and that the mass inflow of recent programs had overwhelmed the community to the purpose the place customers may not join.
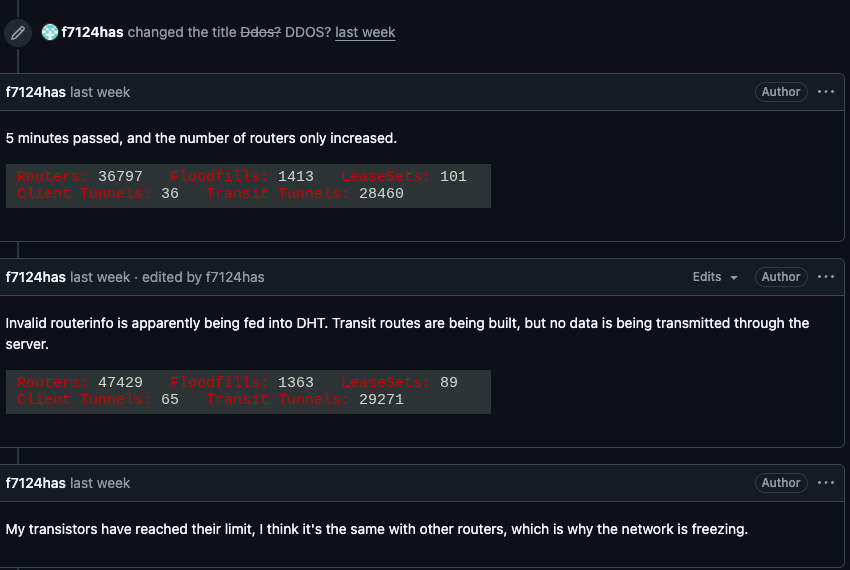
I2P customers complaining about service disruptions from a quickly rising variety of routers immediately swamping the community.
When one I2P person requested whether or not the community was underneath assault, one other person replied, “Appears prefer it. My bodily router freezes when the variety of connections exceeds 60,000.”
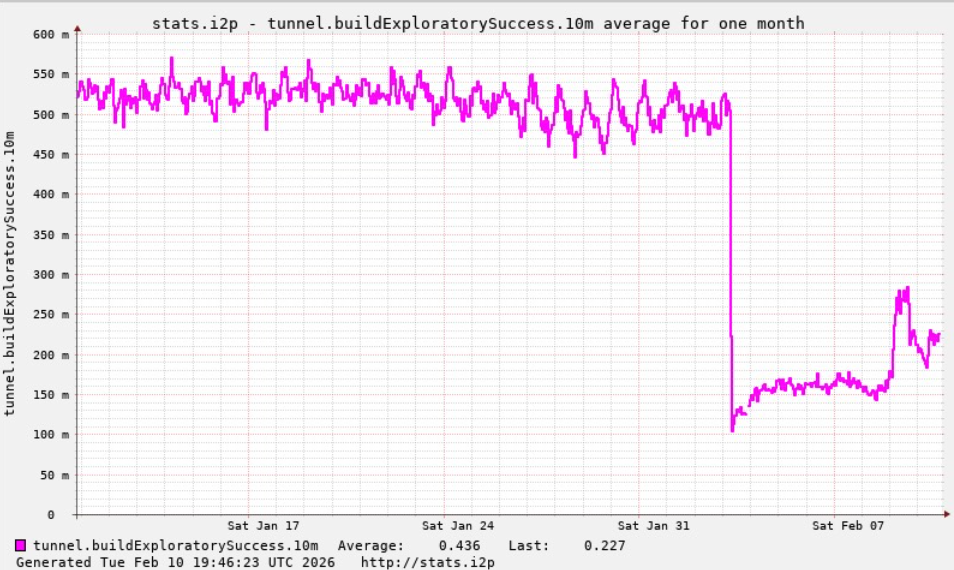
A graph shared by I2P builders exhibiting a marked drop in profitable connections on the I2P community across the time the Kimwolf botnet began making an attempt to make use of the community for fallback communications.
The identical day that I2P customers started noticing the outages, the people answerable for Kimwolf posted to their Discord channel that they’d unintentionally disrupted I2P after making an attempt to affix 700,000 Kimwolf-infected bots as nodes on the community.
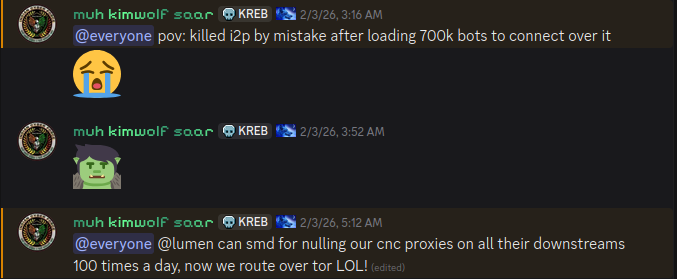
The Kimwolf botmaster overtly discusses what they’re doing with the botnet in a Discord channel with my title on it.
Though Kimwolf is called a potent weapon for launching DDoS assaults, the outages brought about this week by some portion of the botnet making an attempt to affix I2P are what’s referred to as a “Sybil assault,” a menace in peer-to-peer networks the place a single entity can disrupt the system by creating, controlling, and working a lot of pretend, pseudonymous identities.
Certainly, the variety of Kimwolf-infected routers that attempted to affix I2P this previous week was many instances the community’s regular dimension. I2P’s Wikipedia web page says the community consists of roughly 55,000 computer systems distributed all through the world, with every participant appearing as each a router (to relay site visitors) and a consumer.
Nonetheless, Lance James, founding father of the New York Metropolis based mostly cybersecurity consultancy Unit 221B and the unique founding father of I2P, instructed KrebsOnSecurity your entire I2P community now consists of between 15,000 and 20,000 gadgets on any given day.
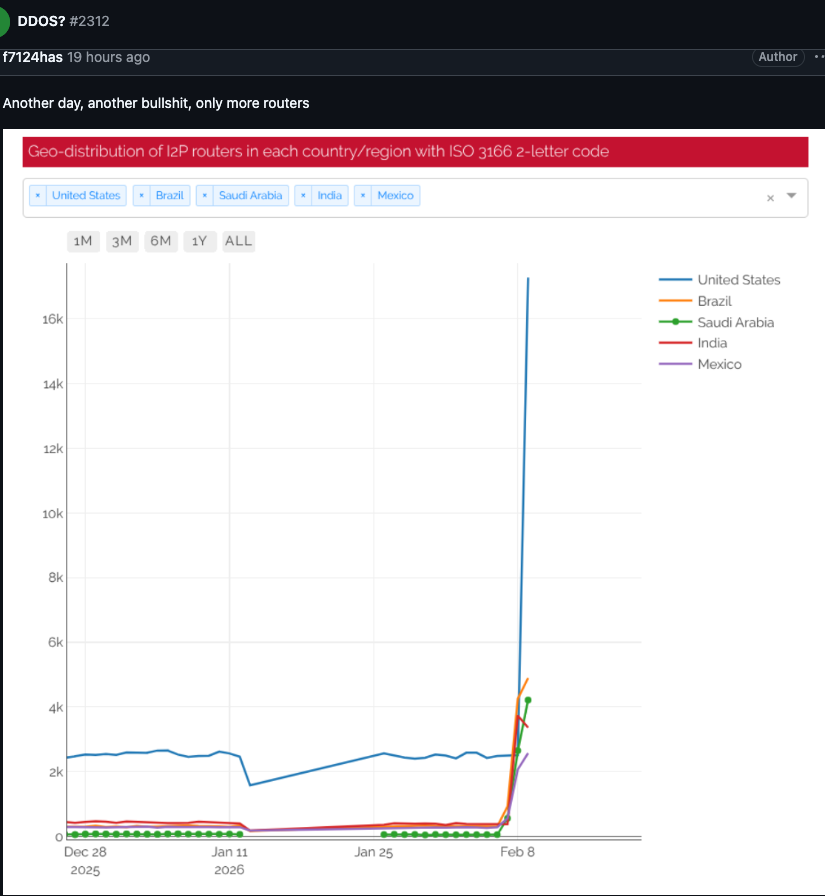
An I2P person posted this graph on Feb. 10, exhibiting tens of 1000’s of routers — principally from the US — immediately making an attempt to affix the community.
Benjamin Brundage is founding father of Synthient, a startup that tracks proxy providers and was the primary to doc Kimwolf’s distinctive spreading methods. Brundage stated the Kimwolf operator(s) have been making an attempt to construct a command and management community that may’t simply be taken down by safety firms and community operators which can be working collectively to fight the unfold of the botnet.
Brundage stated the individuals answerable for Kimwolf have been experimenting with utilizing I2P and the same anonymity community — Tor — as a backup command and management community, though there have been no studies of widespread disruptions within the Tor community just lately.
“I don’t suppose their purpose is to take I2P down,” he stated. “It’s extra they’re in search of an alternative choice to preserve the botnet steady within the face of takedown makes an attempt.”
The Kimwolf botnet created challenges for Cloudflare late final yr when it started instructing thousands and thousands of contaminated gadgets to make use of Cloudflare’s area title system (DNS) settings, inflicting management domains related to Kimwolf to repeatedly usurp Amazon, Apple, Google and Microsoft in Cloudflare’s public rating of probably the most incessantly requested web sites.
James stated the I2P community continues to be working at about half of its regular capability, and {that a} new launch is rolling out which ought to convey some stability enhancements over the subsequent week for customers.
In the meantime, Brundage stated the excellent news is Kimwolf’s overlords seem to have fairly just lately alienated a few of their extra competent builders and operators, resulting in a rookie mistake this previous week that brought about the botnet’s general numbers to drop by greater than 600,000 contaminated programs.
“It looks as if they’re simply testing stuff, like working experiments in manufacturing,” he stated. “However the botnet’s numbers are dropping considerably now, and so they don’t appear to know what they’re doing.”

