A brand new Web-of-Issues (IoT) botnet referred to as Kimwolf has unfold to greater than 2 million gadgets, forcing contaminated methods to take part in large distributed denial-of-service (DDoS) assaults and to relay different malicious and abusive Web site visitors. Kimwolf’s skill to scan the native networks of compromised methods for different IoT gadgets to contaminate makes it a sobering menace to organizations, and new analysis reveals Kimwolf is surprisingly prevalent in authorities and company networks.
Picture: Shutterstock, @Elzicon.
Kimwolf grew quickly within the waning months of 2025 by tricking numerous “residential proxy” providers into relaying malicious instructions to gadgets on the native networks of these proxy endpoints. Residential proxies are offered as a technique to anonymize and localize one’s Net site visitors to a selected area, and the largest of those providers permit clients to route their Web exercise by gadgets in just about any nation or metropolis across the globe.
The malware that turns one’s Web connection right into a proxy node is commonly quietly bundled with numerous cell apps and video games, and it usually forces the contaminated gadget to relay malicious and abusive site visitors — together with advert fraud, account takeover makes an attempt, and mass content-scraping.
Kimwolf primarily focused proxies from IPIDEA, a Chinese language service that has tens of millions of proxy endpoints for hire on any given week. The Kimwolf operators found they may ahead malicious instructions to the inner networks of IPIDEA proxy endpoints, after which programmatically scan for and infect different susceptible gadgets on every endpoint’s native community.
Many of the methods compromised by Kimwolf’s native community scanning have been unofficial Android TV streaming containers. These are usually Android Open Supply Challenge gadgets — not Android TV OS gadgets or Play Shield licensed Android gadgets — and they’re usually marketed as a technique to watch limitless (learn:pirated) video content material from well-liked subscription streaming providers for a one-time charge.
Nonetheless, a fantastic many of those TV containers ship to shoppers with residential proxy software program pre-installed. What’s extra, they don’t have any actual safety or authentication built-in: Should you can talk instantly with the TV field, it’s also possible to simply compromise it with malware.
Whereas IPIDEA and different affected proxy suppliers not too long ago have taken steps to dam threats like Kimwolf from going upstream into their endpoints (reportedly with various levels of success), the Kimwolf malware stays on tens of millions of contaminated gadgets.
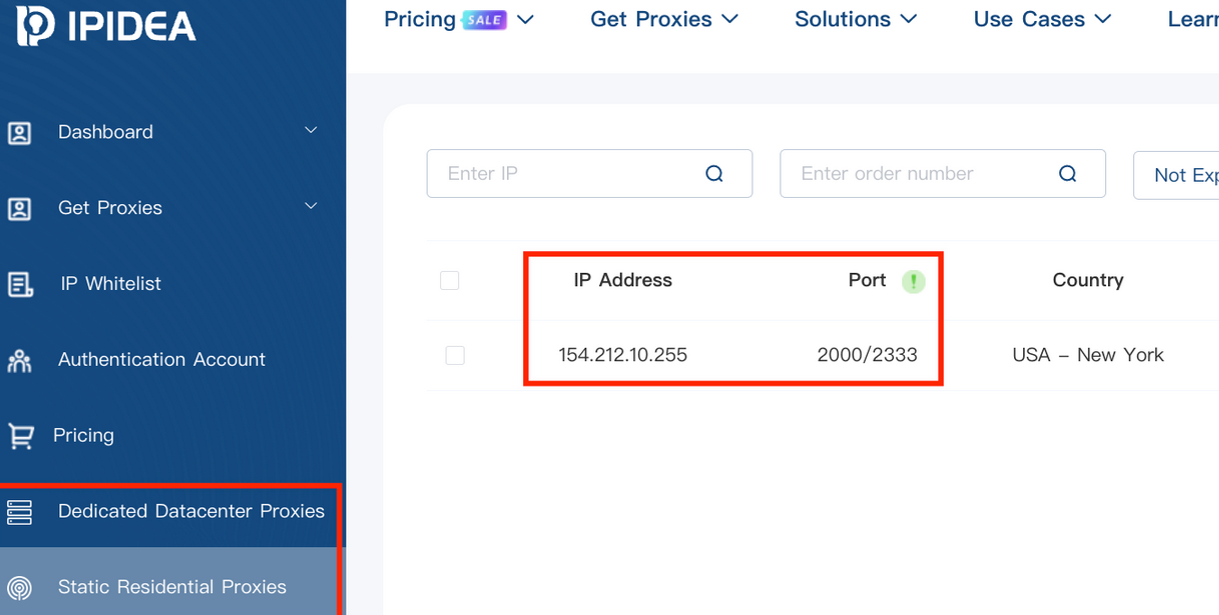
A screenshot of IPIDEA’s proxy service.
Kimwolf’s shut affiliation with residential proxy networks and compromised Android TV containers may recommend we’d discover comparatively few infections on company networks. Nonetheless, the safety agency Infoblox mentioned a current assessment of its buyer site visitors discovered almost 25 % of them made a question to a Kimwolf-related area identify since October 1, 2025, when the botnet first confirmed indicators of life.
Infoblox discovered the affected clients are primarily based everywhere in the world and in a variety of trade verticals, from training and healthcare to authorities and finance.
“To be clear, this means that almost 25% of consumers had a minimum of one gadget that was an endpoint in a residential proxy service focused by Kimwolf operators,” Infoblox defined. “Such a tool, perhaps a cellphone or a laptop computer, was primarily co-opted by the menace actor to probe the native community for susceptible gadgets. A question means a scan was made, not that new gadgets had been compromised. Lateral motion would fail if there have been no susceptible gadgets to be discovered or if the DNS decision was blocked.”
Synthient, a startup that tracks proxy providers and was the primary to reveal on January 2 the distinctive strategies Kimwolf makes use of to unfold, discovered proxy endpoints from IPIDEA had been current in alarming numbers at authorities and tutorial establishments worldwide. Synthient mentioned it spied a minimum of 33,000 affected Web addresses at universities and schools, and almost 8,000 IPIDEA proxies inside numerous U.S. and overseas authorities networks.

The highest 50 domains sought out by customers of IPIDEA’s residential proxy service, in keeping with Synthient.
In a webinar on January 16, consultants on the proxy monitoring service Spur profiled Web addresses related to IPIDEA and 10 different proxy providers that had been regarded as susceptible to Kimwolf’s tips. Spur discovered residential proxies in almost 300 authorities owned and operated networks, 318 utility corporations, 166 healthcare corporations or hospitals, and 141 corporations in banking and finance.
“I appeared on the 298 [government] owned and operated [networks], and so lots of them had been DoD [U.S. Department of Defense], which is type of terrifying that DoD has IPIDEA and these different proxy providers positioned within it,” Spur Co-Founder Riley Kilmer mentioned. “I don’t understand how these enterprises have these networks arrange. It could possibly be that [infected devices] are segregated on the community, that even when you had native entry it doesn’t actually imply a lot. Nonetheless, it’s one thing to concentrate on. If a tool goes in, something that gadget has entry to the proxy would have entry to.”
Kilmer mentioned Kimwolf demonstrates how a single residential proxy an infection can shortly result in larger issues for organizations which might be harboring unsecured gadgets behind their firewalls, noting that proxy providers current a doubtlessly easy means for attackers to probe different gadgets on the native community of a focused group.
“If you understand you’ve got [proxy] infections which might be positioned in an organization, you’ll be able to selected that [network] to return out of after which regionally pivot,” Kilmer mentioned. “When you have an concept of the place to start out or look, now you’ve got a foothold in an organization or an enterprise primarily based on simply that.”
That is the third story in our collection on the Kimwolf botnet. Subsequent week, we’ll make clear the myriad China-based people and firms linked to the Badbox 2.0 botnet, the collective identify given to an enormous variety of Android TV streaming field fashions that ship with no discernible safety or authentication built-in, and with residential proxy malware pre-installed.
Additional studying:
The Kimwolf Botnet is Stalking Your Native Community
Who Benefitted from the Aisuru and Kimwolf Botnets?
A Damaged System Fueling Botnets (Synthient).

