Social media influencers can present attain and belief for scams and malware distribution. Strong account safety is essential to stopping the fraudsters.
25 Nov 2025
•
,
4 min. learn

It’s not a simple time to be an influencer. Manufacturers are spending much less, advert income is declining and competitors is fierce – together with from AI-generated influencers and impersonators. In accordance with one examine, round half of the business makes simply $15,000 or much less per yr, whereas only one in 10 pull in over $100,000. As if that wasn’t sufficient, there’s one other problem: influencers are an more and more fashionable goal for cybercriminals. A latest spear-phishing marketing campaign abusing manufacturers equivalent to Tesla and Purple Bull highlights the potential dangers.
Account compromise might have a devastating influence, not solely on the sufferer but additionally their followers and potential model purchasers. In case you’re a social media content material creator, it could be time to revisit these account safety greatest practices.
Why do influencers matter to hackers?
Menace actors are often on the lookout for a number of issues in a possible on-line sufferer. In the event that they’re on the hunt for influencer social media accounts to hijack, they’ll need ones with as many followers as doable. This implies their scams or malware will likely be distributed far and large. They ideally additionally wish to goal influencers who’ve constructed long-term belief with their viewers, by way of months or years of offering recommendation on-line. Belief is also earned by way of verified standing badges. Both manner, it means followers usually tend to click on on the hyperlinks in these accounts with out pondering.
It goes with out saying that hackers additionally want these accounts to be simple to compromise. Something protected with a single weak password is a present to an opportunistic cybercriminal.
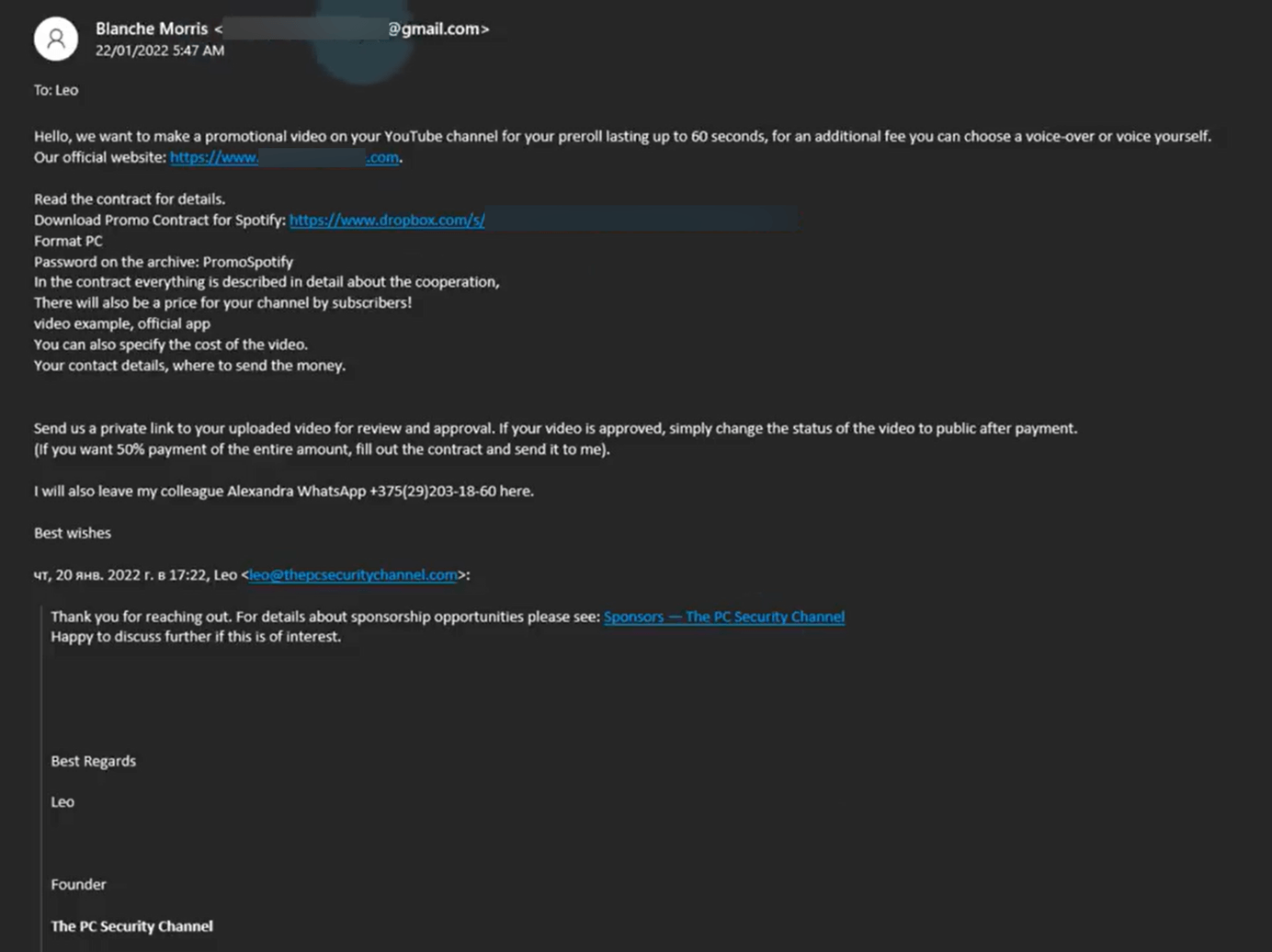
How do they get hacked?
With regards to the concentrating on of influencers, assaults start with the social media account itself – whether or not it’s X (previously Twitter), YouTube, TikTok, Instagram or one other platform. On uncommon events, the tip purpose is state-sponsored disinformation. However most of the time we’re speaking about financially motivated cybercrime. There are a number of methods to achieve entry to accounts, notably:
- Spearphishing: Extremely focused phishing assaults designed to trick the person into handing over their logins. These might use publicly obtainable data on the goal to make them appear extra life like. A phishing electronic mail or textual content is also booby trapped with a malicious hyperlink or attachment, which quietly installs infostealing malware on the sufferer’s gadget. It’s one other option to pay money for delicate data like passwords.
- Credential stuffing/brute forcing: Brute-force assaults are a type of trial and error the place automated software program tries both fashionable passwords (password spraying) or beforehand breached passwords (credential stuffing) in opposition to massive numbers of accounts/web sites. When one username/password combo works, they’re in.
- SIM swapping: Hackers socially engineer a telco employee into transferring the sufferer’s cellphone quantity to a SIM beneath their management. That permits them to intercept two-factor authentication (2FA) codes typically used to authenticate and entry social media accounts.
It must be famous that AI helps cybecriminals obtain their objectives by crafting extra convincing phishing emails in flawless native languages. It additionally helps campaigns by gathering background data on targets which can be utilized for these and SIM swapping assaults. And AI could make brute-force assaults sooner and more practical.
What occurs subsequent?
With entry to a high-value influencer account, a cybercriminal would possibly wish to promote it instantly on-line to the very best bidder. Or they might use it themselves. Both manner, it’s almost definitely for use to promote crypto funding scams and different get-rich-quick schemes designed to trick followers out of their hard-earned money. Or to submit malicious hyperlinks which might set up malware on followers’ machines.
A menace actor may attempt to extort their sufferer into paying them cash to regain entry; for instance by threatening to submit vulgar or inflammatory content material. They are able to entry follower contact databases, which may very well be offered and/or used to focus on followers instantly with spam and phishing assaults. A hijacked account would possibly theoretically even be abused to submit false claims about manufacturers related with that influencer.
If menace actors additionally handle to compromise an influencer’s e-commerce account (utilizing the identical methods listed above), they are able to divert incoming funds from followers.
The underside line is id theft-related safety dangers for followers, trashed status for manufacturers and influencers, and probably direct losses for content material creators.
Beneath lock and key
Confronted with what may very well be an existential danger, influencers want a plan of motion. That must be based mostly round stable greatest practices for account safety. Think about:
- Lengthy, sturdy and distinctive passwords which can be tougher for password spraying instruments to crack.
- App-based 2FA (e.g., apps equivalent to Google Authenticator or Microsoft Authenticator) quite than text-based 2FA codes that may be intercepted. These will be sure that, even when hackers pay money for a password, they received’t have the ability to entry the account.
- Better phishing consciousness; particularly a number of the lures that hackers usually use to entice influencers, like profitable seeming sponsorship offers with big-name manufacturers. If one thing appears to be like too good to be true, it often is.
- Separate units and electronic mail accounts for work and private use, with the enterprise ones fitted with higher-grade safety controls.
- Safety software program from a good supplier on all units and machines. This could stop malicious downloads and block phishing emails.
- All the time conserving gadget and PC software program/working system on the newest model, which can imply essentially the most safe model.
- By no means downloading apps from unofficial app shops, as they could be harboring info-stealing malware.
An influencer’s status finally defines their business success. It should be protected in any respect prices.


