
A China-aligned APT risk actor named “TheWizards” abuses an IPv6 networking characteristic to launch adversary-in-the-middle (AitM) assaults that hijack software program updates to put in Home windows malware.
In response to ESET, the group has been lively since no less than 2022, concentrating on entities within the Philippines, Cambodia, the United Arab Emirates, China, and Hong Kong. Victims embrace people, playing corporations, and different organizations.
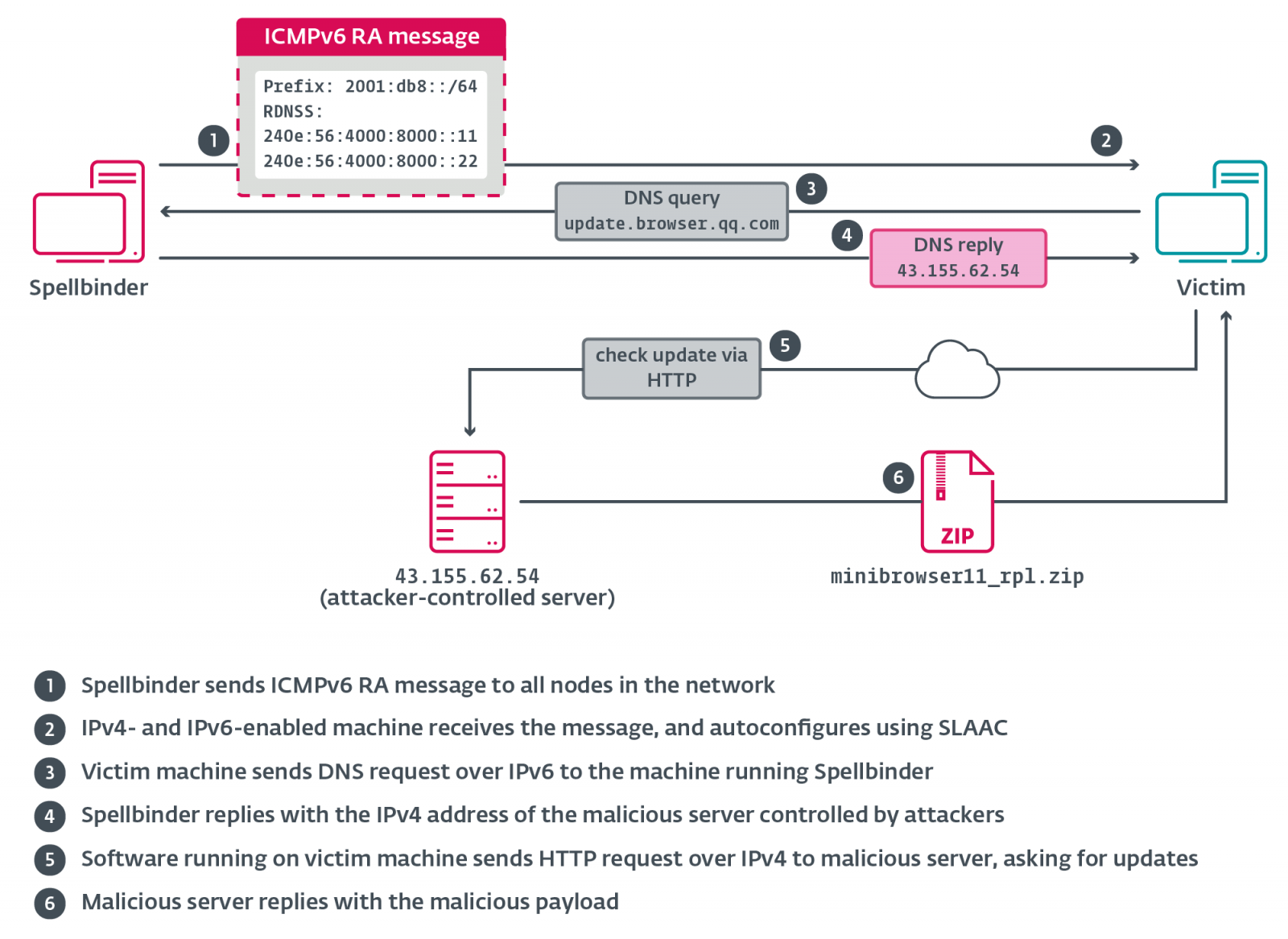
The assaults make the most of a customized software dubbed “Spellbinder” by ESET that abuses the IPv6 Stateless Deal with Autoconfiguration (SLAAC) characteristic to conduct SLACC assaults.
SLAAC is a characteristic of the IPv6 networking protocol that permits units to robotically configure their very own IP addresses and default gateway without having a DHCP server. As an alternative, it makes use of Router Commercial (RA) messages to obtain IP addresses from IPv6-supported routers.
The hacker’s Spellbinder software abuses this characteristic by sending spoofed RA messages over the community, inflicting close by programs to robotically obtain a brand new IPv6 IP deal with, new DNS servers, and a brand new, most popular IPv6 gateway.
This default gateway, although, is the IP deal with of the Spellbinder software, which permits it to intercept communications and reroute visitors by way of attacker-controlled servers.
“Spellbinder sends a multicast RA packet each 200 ms to ff02::1 (“all nodes”); Home windows machines within the community with IPv6 enabled will autoconfigure through stateless deal with autoconfiguration (SLAAC) utilizing info supplied within the RA message, and start sending IPv6 visitors to the machine operating Spellbinder, the place packets might be intercepted, analyzed, and replied to the place relevant,” explains ESET.
Supply: ESET
ESET stated assaults deploy Spellbinder utilizing an archive named AVGApplicationFrameHostS.zip, which extracts right into a listing mimicking authentic software program: “%PROGRAMFILESpercentAVG Applied sciences.”
Inside this listing are AVGApplicationFrameHost.exe, wsc.dll, log.dat, and a authentic copy of winpcap.exe. The WinPcap executable is used to side-load the malicious wsc.dll, which hundreds Spellbinder into reminiscence.
As soon as a tool is contaminated, Spellbinder begins capturing and analyzing community visitors making an attempt to attach particular domains, comparable to these associated to Chinese language software program replace servers.
ESET says the malware screens for domains belonging to the next corporations: Tencent, Baidu, Xunlei, Youku, iQIYI, Kingsoft, Mango TV, Funshion, Yuodao, Xiaomi, Xiaomi Miui, PPLive, Meitu, Quihoo 360, and Baofeng.
The software then redirects these requests to obtain and set up malicious updates that deploy a backdoor named “WizardNet.”
The WizardNet backdoor provides attackers persistent entry to the contaminated system and permits them to put in extra malware as wanted.
To guard towards a majority of these assaults, organizations can monitor IPv6 visitors or flip off the protocol if it isn’t required of their atmosphere.
In January, ESET additionally reported on one other hacking group named “Blackwood” hijacking the WPS Workplace software program replace characteristic to put in malware.


