The Balancer Protocol introduced that hackers had focused its v2 swimming pools, with losses reportedly estimated to be greater than $128 million.
Balancer is a decentralized finance (DeFi) protocol constructed on the Ethereum blockchain as an automatic market maker and liquidity infrastructure layer.
It supplies versatile swimming pools with customized token mixes, permitting customers to deposit belongings, earn charges, and let merchants swap belongings, and it’s ruled by the BAL token, which had a market cap of $65 million proper earlier than the incident.
Balancer has not shared many particulars in regards to the incident however warned customers to be cautious towards potential scams or phishing makes an attempt.
Balancer confirmed in the present day that an exploit affected its V2 Compostable Steady Swimming pools at 7:48 AM UTC and that the difficulty doesn’t affect another Balancer swimming pools, together with V3.
“Our crew is working with main safety researchers to know the difficulty,” the firm mentioned in an replace a number of hours in the past.
In line with GoPlus Safety, the Balancer V2 exploit stemmed from a precision rounding error within the Vault’s swap calculations.
Every swap operation rounded down token quantities, creating tiny discrepancies that the attacker may repeatedly exploit. By chaining a number of swaps by way of the batchSwap operate, these rounding losses compounded into a big worth distortion.
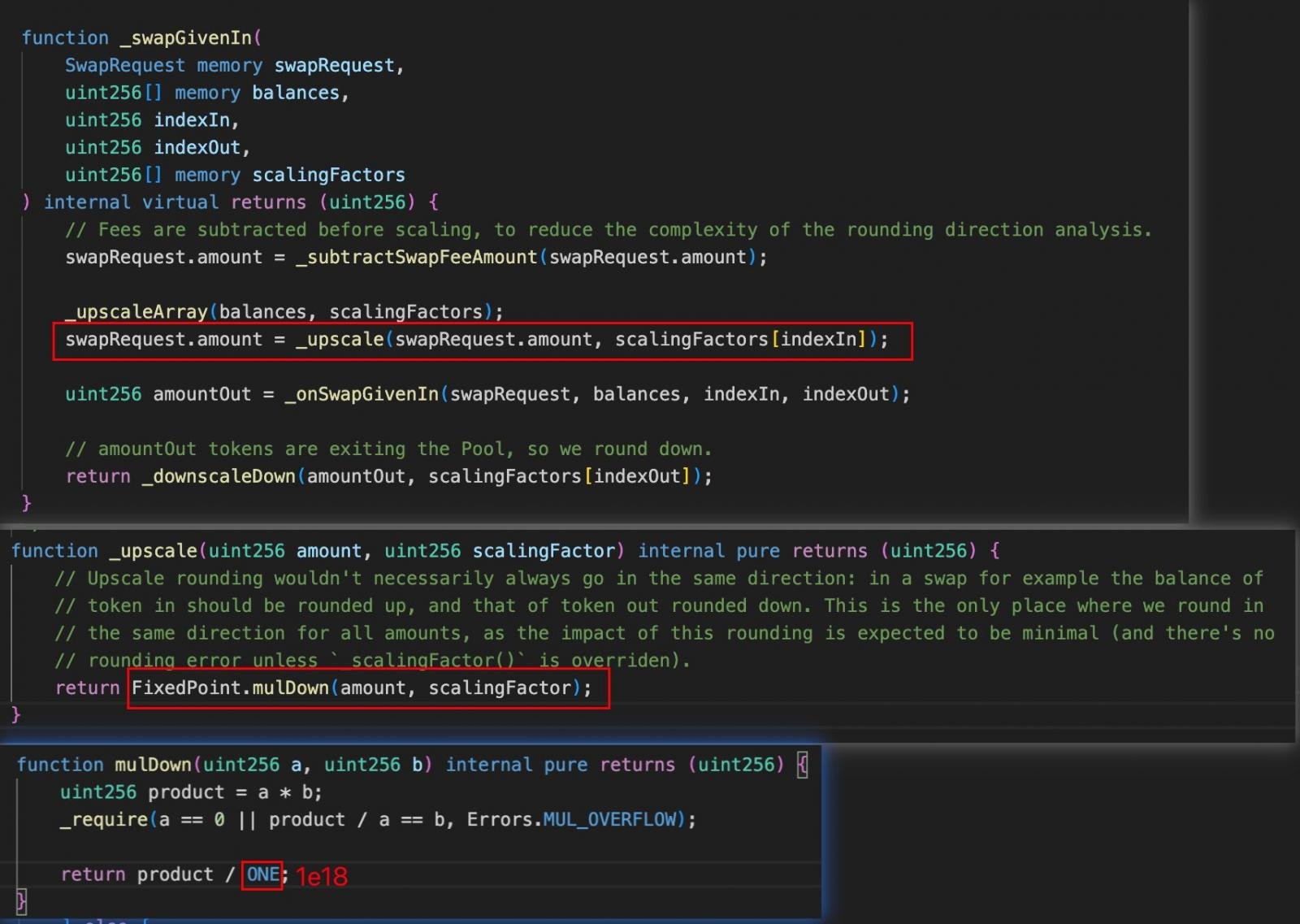
Supply: GoPlus Safety
Nevertheless, different customers claiming to know what occurred attribute the hack to improper authorization and callback dealing with inside Balancer’s V2 vaults.
In line with Aditya Bajaj, a maliciously deployed contract manipulated vault calls throughout pool initialization, successfully bypassing safeguards and enabling unauthorized swaps and steadiness manipulations throughout interconnected swimming pools.
Whereas there isn’t a settlement on the assault methodology but, Balancer promised to share extra particulars in regards to the hack “and a full autopsy as quickly as attainable.”
It’s price noting that Balancer V2 has been audited 11 occasions since 2021, with various examination scopes.
Try and trick the hacker
In the meantime, it seems that somebody tried to make the most of the scenario by impersonating Balancer and providing the hacker a “white-hat bounty” of 20% of the stolen quantity in the event that they agreed to return the remainder of the funds to a selected tackle.
The phishing message is well-written and checks the tips to look credible, together with the reward, a deadline, and a menace, all a part of a negotiation urgent for speedy cooperation.
If the hacker refuses the deal, the fraudster impersonating Balancer threatens to use all data they’ve from blockchain forensics consultants, regulation enforcement companies, and regulatory companions to determine and prosecute the attacker.
“Our companions have a excessive diploma of confidence you may be recognized from access-log metadata collected by our infrastructure, indicating connections from an outlined set of IP addresses/ASNs and related ingress timestamps that correlate with the transaction exercise on chain,” concludes the fraudulent message.
The Balancer hack is without doubt one of the largest cryptocurrency heists in 2025. Though there isn’t a attribution, the best menace to DeFi entities is North Korean hackers.
As of October 3, the quantity of cryptocurrency linked to North Korean thefts this yr had exceeded $2 billion, with the most important by far being the Bybit assault in February, once they stole $1.5 billion in cryptocurrency.