
China-linked APT24 hackers have been utilizing a beforehand undocumented malware known as BadAudio in a three-year espionage marketing campaign that just lately switched to extra refined assault strategies.
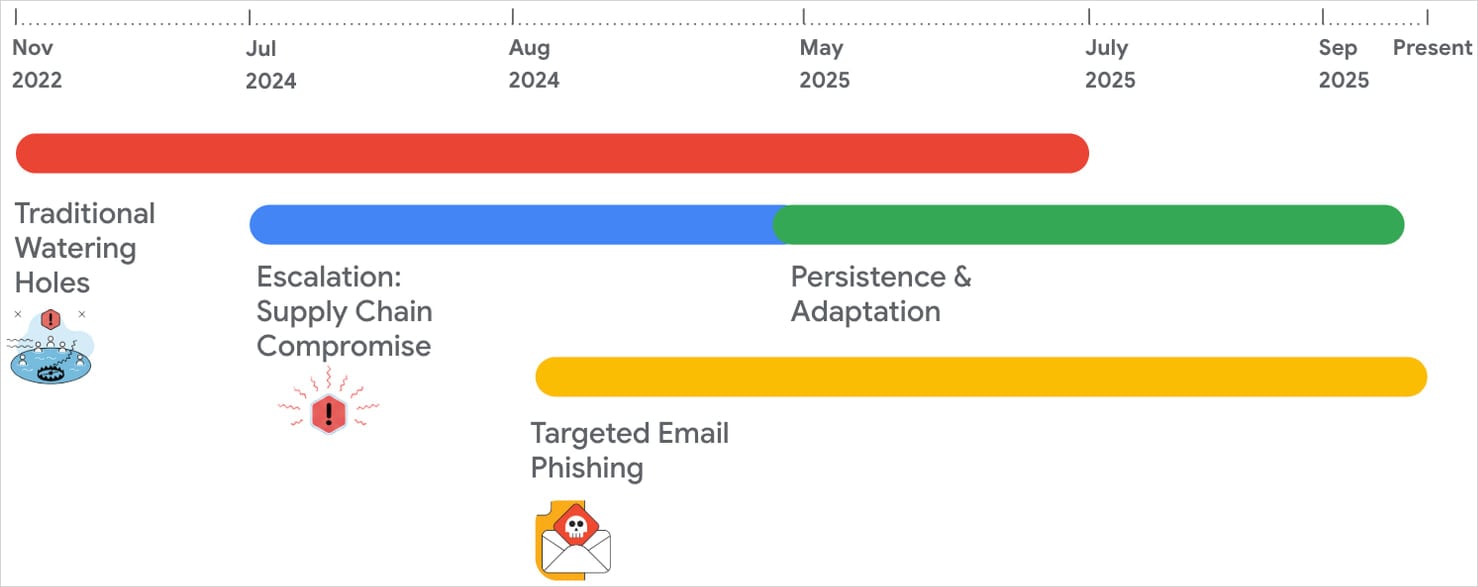
Since 2022, the malware has been delivered to victims by a number of strategies that embody spearphishing, supply-chain compromise, and watering gap assaults.
Marketing campaign evolution
From November 2022 till at the very least September 2025, APT24 compromised greater than 20 reliable public web sites from varied domains to inject malicious JavaScript code that chosen guests of curiosity – the main focus was completely on Home windows programs.
Researchers at Google Menace Intelligence Group (GTIG) say that the script fingerprinted guests who certified as targets and loaded a pretend software program replace pop-up to lure them into downloading BadAudio.
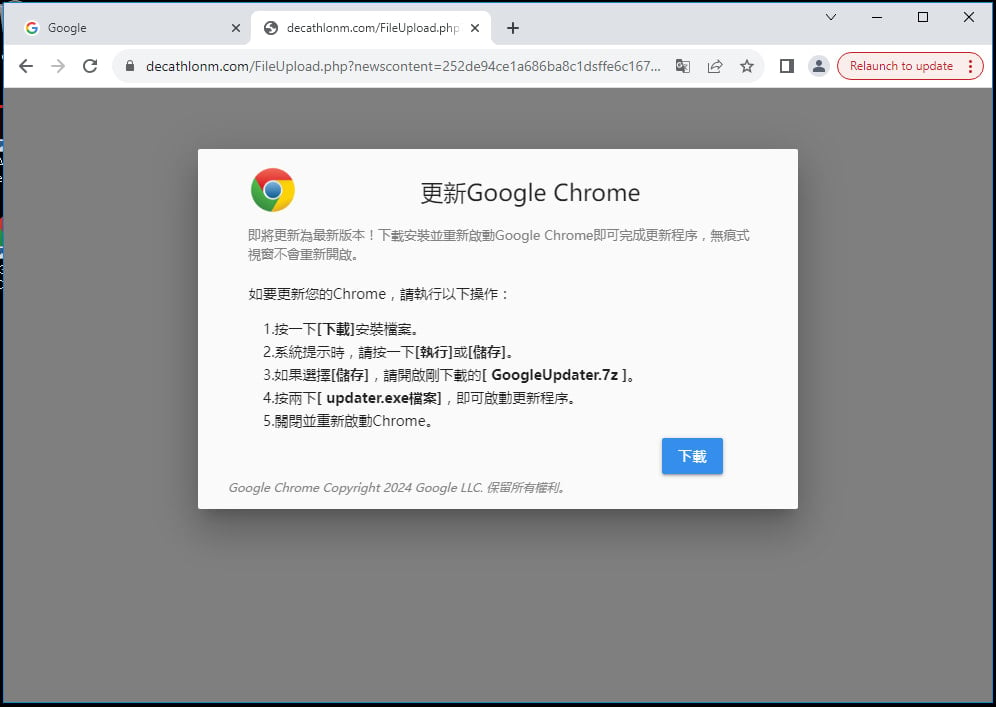
Supply: Google
Beginning July 2024, APT24 compromised a number of occasions a digital advertising and marketing firm in Taiwan that gives JavaScript libraries to shopper web sites.
By way of this tactic, the attackers injected malicious JavaScript right into a extensively used library that the agency distributed, and registered a website title that impersonated a reliable Content material Supply Community (CDN). This enabled the attacker to compromise greater than 1,000 domains.
From late 2024 till July 2025, APT24 repeatedly compromised the identical advertising and marketing agency by injecting malicious, obfuscated JavaScript right into a modified JSON file, which was loaded by a separate JavaScript file from the identical vendor.
As soon as executed, it fingerprinted every web site customer and despatched a base64-encoded report back to the attackers’ server, permitting them to resolve if they’d reply with the next-stage URL.
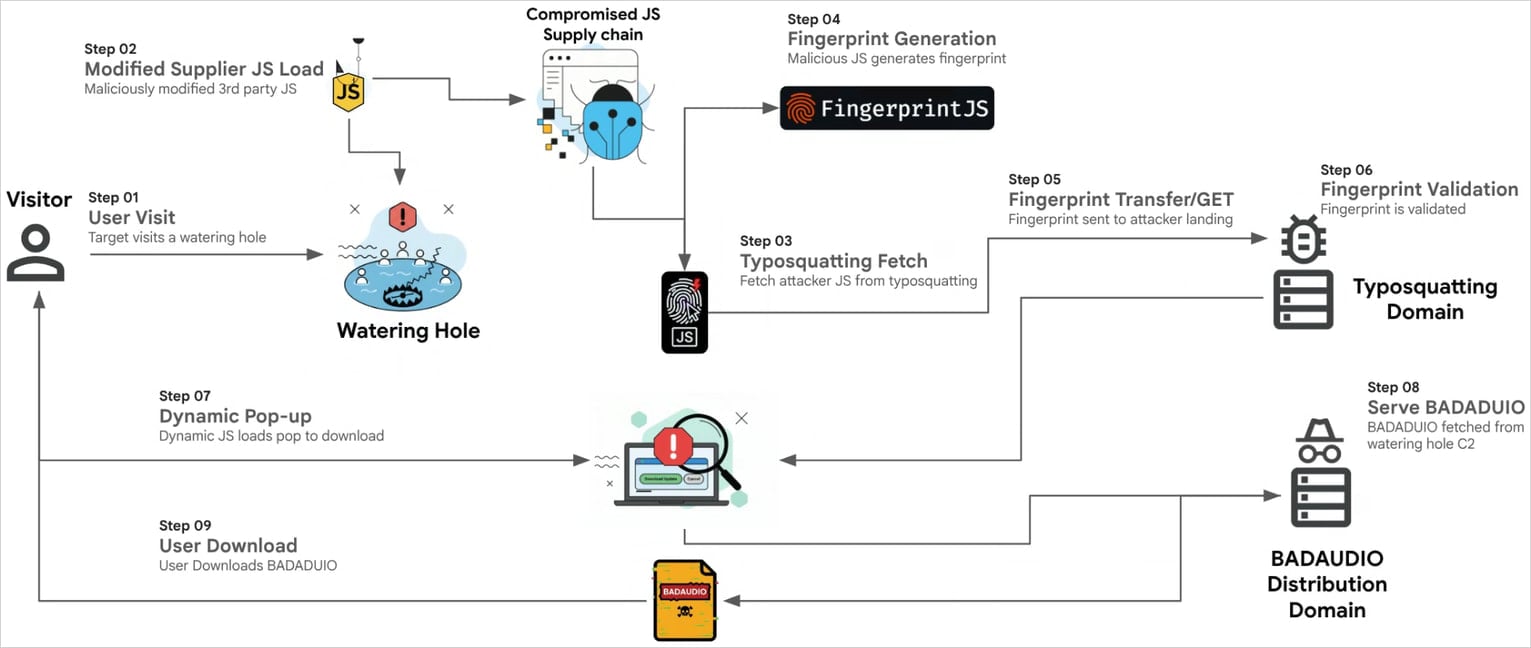
Supply: Google
In parallel, ranging from August 2024, APT24 launched spearphishing operations that delivered the BadAudio malware utilizing as lures emails that impersonated animal rescue organizations.
In some variants of those assaults, APT24 used reliable cloud providers like Google Drive and OneDrive for malware distribution, as an alternative of their very own servers. Nonetheless, Google says that most of the makes an attempt had been detected, and the messages ended up within the spam field.
Within the noticed instances, although, the emails included monitoring pixels to verify when recipients opened them.
Supply: Google
BadAudio malware loader
Based on GTIG’s evaluation, the BadAudio malware is closely obfuscated to evade detection and hinder evaluation by safety researchers.
It achieves execution by DLL search order hijacking, a way that permits a malicious payload to be loaded by a reliable utility.
“The malware is engineered with management stream flattening—a classy obfuscation approach that systematically dismantles a program’s pure, structured logic,” GTIG explains in a report as we speak.
“This methodology replaces linear code with a collection of disconnected blocks ruled by a central ‘dispatcher’ and a state variable, forcing analysts to manually hint every execution path and considerably impeding each automated and guide reverse engineering efforts.”
As soon as BadAudio is executed on a goal machine, it collects fundamental system particulars (hostname, username, structure), encrypts the data utilizing a hard-coded AES key, and sends it to a hard-coded command-and-control (C2) deal with.
Subsequent, it downloads an AES-encrypted payload from the C2, decrypts it, and executes it in reminiscence for evasion utilizing DLL sideloading.
In at the very least one case, Google researchers noticed the deployment of the Cobalt Strike Beacon by way of BadAudio, a extensively abused penetration-testing framework.
The researchers underline that they could not verify the presence of a Cobalt Strike Beacon in each occasion they analyzed.
It needs to be famous that regardless of utilizing BadAudio for 3 years, APT24’s ways succeeded in conserving it largely undetected.
From the eight samples GTIG researchers offered of their report, solely two are flagged as malicious by greater than 25 antivirus engines on the VirusTotal scanning platform. The remainder of the samples, with a creation date of December 7, 2022, are detected by as much as 5 safety options.
GTIG says that APT24’s evolution in the direction of stealthier assaults is pushed by the risk actor’s operational capabilities and its “capability for persistent and adaptive espionage.”
It is price range season! Over 300 CISOs and safety leaders have shared how they’re planning, spending, and prioritizing for the yr forward. This report compiles their insights, permitting readers to benchmark methods, establish rising traits, and evaluate their priorities as they head into 2026.
Learn the way high leaders are turning funding into measurable affect.



