U.S. prosecutors final week levied felony hacking expenses in opposition to 19-year-old U.Ok. nationwide Thalha Jubair for allegedly being a core member of Scattered Spider, a prolific cybercrime group blamed for extorting a minimum of $115 million in ransom funds from victims. The costs got here as Jubair and an alleged co-conspirator appeared in a London court docket to face accusations of hacking into and extorting a number of massive U.Ok. retailers, the London transit system, and healthcare suppliers in the US.
At a court docket listening to final week, U.Ok. prosecutors laid out a litany of expenses in opposition to Jubair and 18-year-old Owen Flowers, accusing the kids of involvement in an August 2024 cyberattack that crippled Transport for London, the entity answerable for the general public transport community within the Larger London space.

A court docket artist sketch of Owen Flowers (left) and Thalha Jubair showing at Westminster Magistrates’ Courtroom final week. Credit score: Elizabeth Cook dinner, PA Wire.
On July 10, 2025, KrebsOnSecurity reported that Flowers and Jubair had been arrested in the UK in reference to current Scattered Spider ransom assaults in opposition to the retailers Marks & Spencer and Harrods, and the British meals retailer Co-op Group.
That story cited sources near the investigation saying Flowers was the Scattered Spider member who anonymously gave interviews to the media within the days after the group’s September 2023 ransomware assaults disrupted operations at Las Vegas casinos operated by MGM Resorts and Caesars Leisure.
The story additionally famous that Jubair’s alleged handles on cybercrime-focused Telegram channels had far lengthier rap sheets involving among the extra consequential and headline-grabbing knowledge breaches over the previous 4 years. What follows is an account of cybercrime actions that prosecutors have attributed to Jubair’s alleged hacker handles, as instructed by these accounts in posts to public Telegram channels which are intently monitored by a number of cyber intelligence companies.
EARLY DAYS (2021-2022)
Jubair is alleged to have been a core member of the LAPSUS$ cybercrime group that broke into dozens of expertise firms starting in late 2021, stealing supply code and different inner knowledge from tech giants together with Microsoft, Nvidia, Okta, Rockstar Video games, Samsung, T-Cellular, and Uber.
That’s, in keeping with the previous chief of the now-defunct LAPSUS$. In April 2022, KrebsOnSecurity printed inner chat information taken from a server that LAPSUS$ used, and people chats point out Jubair was working with the group utilizing the nicknames Amtrak and Asyntax. In the midst of the gang’s cybercrime spree, Asyntax instructed the LAPSUS$ chief to not share T-Cellular’s brand in photos despatched to the group as a result of he’d been beforehand busted for SIM-swapping and his dad and mom would suspect he was again at it once more.
The chief of LAPSUS$ responded by gleefully posting Asyntax’s actual identify, cellphone quantity, and different hacker handles right into a public chat room on Telegram:
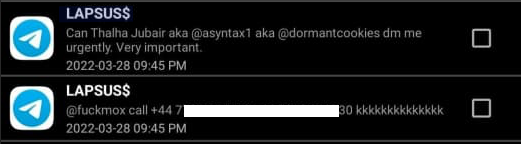
In March 2022, the chief of the LAPSUS$ knowledge extortion group uncovered Thalha Jubair’s identify and hacker handles in a public chat room on Telegram.
That story concerning the leaked LAPSUS$ chats additionally linked Amtrak/Asyntax to a number of earlier hacker identities, together with “Everlynn,” who in April 2021 started providing a cybercriminal service that bought fraudulent “emergency knowledge requests” concentrating on the most important social media and e-mail suppliers.
In these so-called “pretend EDR” schemes, the hackers compromise e-mail accounts tied to police departments and authorities businesses, after which ship unauthorized calls for for subscriber knowledge (e.g. username, IP/e-mail tackle), whereas claiming the data being requested can’t watch for a court docket order as a result of it pertains to an pressing matter of life and dying.
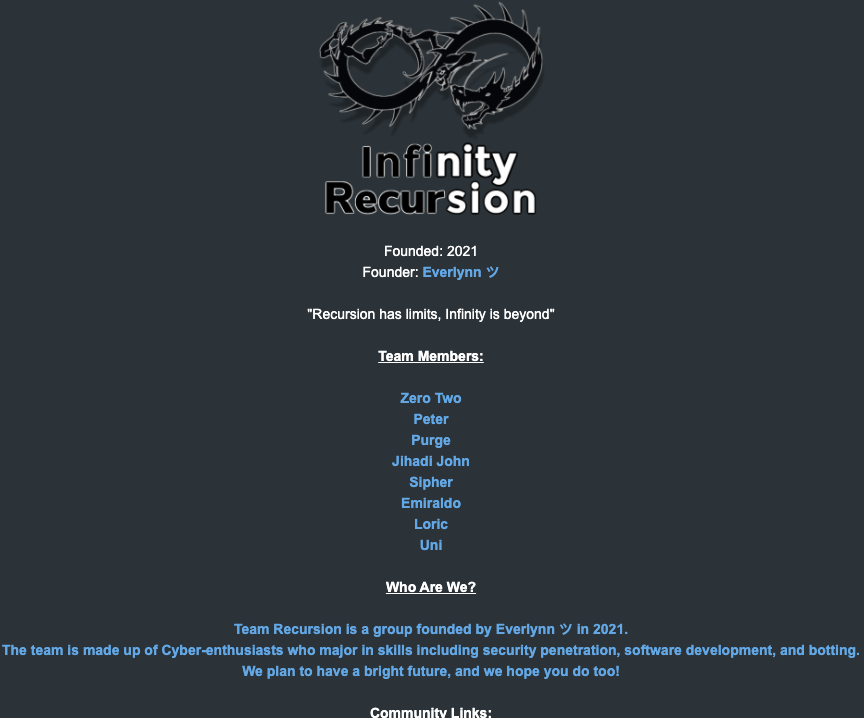
The roster of the now-defunct “Infinity Recursion” hacking workforce, which bought pretend EDRs between 2021 and 2022. The founder “Everlynn” has been tied to Jubair. The member listed as “Peter” grew to become the chief of LAPSUS$ who would later submit Jubair’s identify, cellphone quantity and hacker handles into LAPSUS$’s chat channel.
EARTHTOSTAR
Prosecutors in New Jersey final week alleged Jubair was a part of a menace group variously often called Scattered Spider, 0ktapus, and UNC3944, and that he used the nicknames EarthtoStar, Brad, Austin, and Austistic.
Starting in 2022, EarthtoStar co-ran a bustling Telegram channel known as Star Chat, which was residence to a prolific SIM-swapping group that relentlessly used voice- and SMS-based phishing assaults to steal credentials from workers on the main wi-fi suppliers within the U.S. and U.Ok.

Jubair allegedly used the deal with “Earth2Star,” a core member of a prolific SIM-swapping group working in 2022. This advert produced by the group lists varied costs for SIM swaps.
The group would then use that entry to promote a SIM-swapping service that might redirect a goal’s cellphone quantity to a tool the attackers managed, permitting them to intercept the sufferer’s cellphone calls and textual content messages (together with one-time codes). Members of Star Chat focused a number of wi-fi carriers with SIM-swapping assaults, however they centered primarily on phishing T-Cellular workers.
In February 2023, KrebsOnSecurity scrutinized greater than seven months of those SIM-swapping solicitations on Star Chat, which nearly every day peppered the general public channel with “Tmo up!” and “Tmo down!” notices indicating durations whereby the group claimed to have energetic entry to T-Cellular’s community.
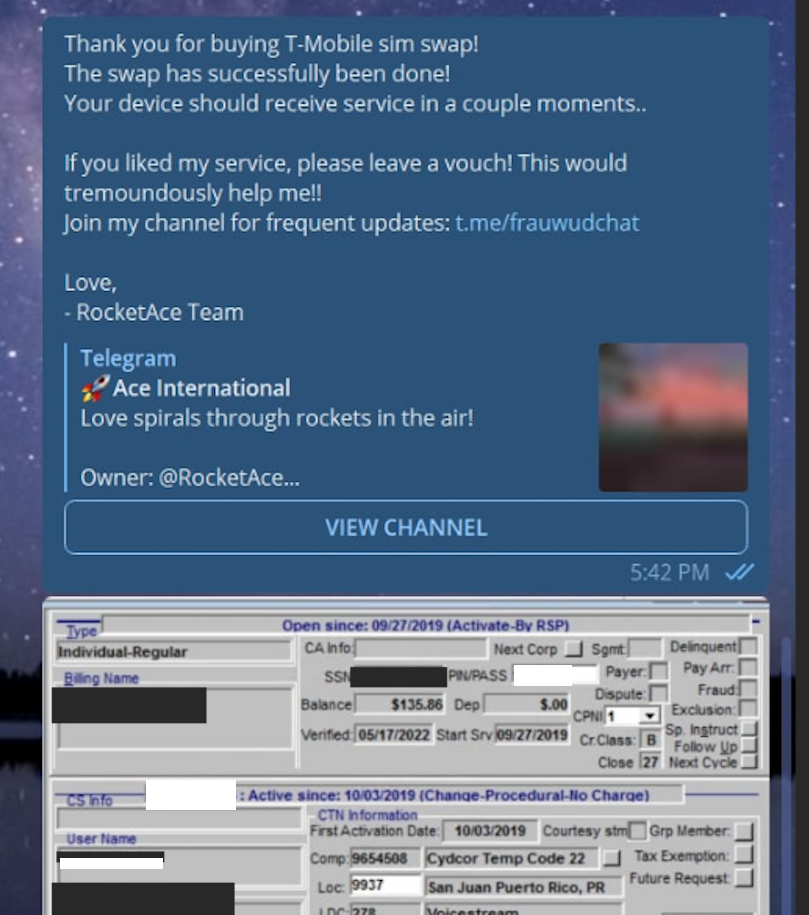
A redacted receipt from Star Chat’s SIM-swapping service concentrating on a T-Cellular buyer after the group gained entry to inner T-Cellular worker instruments.
The info confirmed that Star Chat — together with two different SIM-swapping teams working on the identical time — collectively broke into T-Cellular over 100 occasions within the final seven months of 2022. Nonetheless, Star Chat was by far essentially the most prolific of the three, answerable for a minimum of 70 of these incidents.
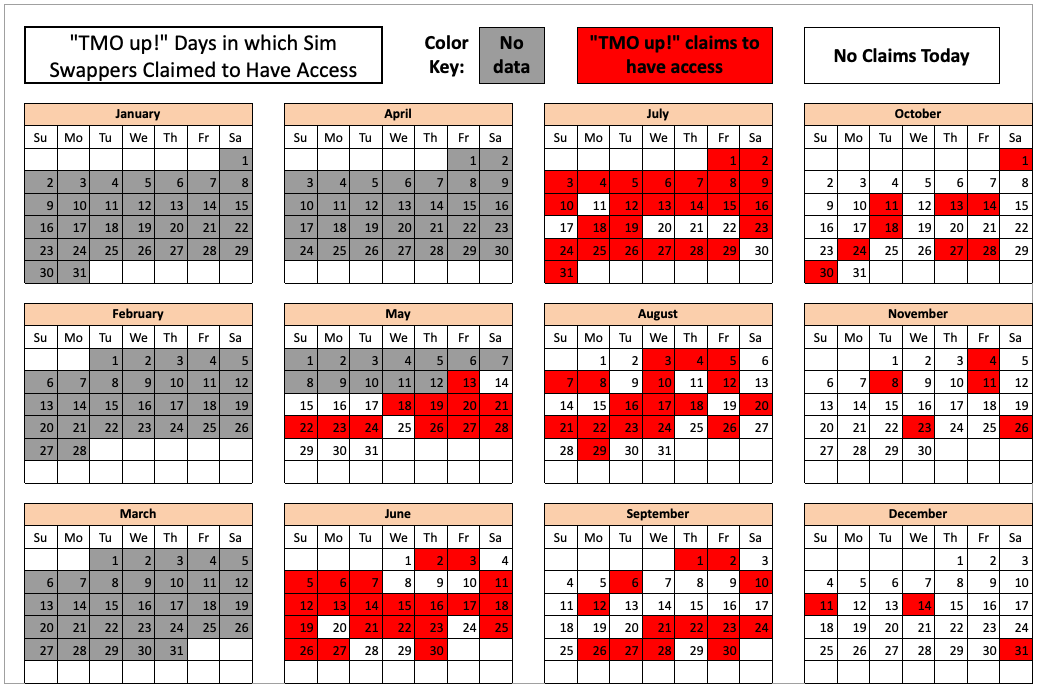
The 104 days within the latter half of 2022 by which completely different identified SIM-swapping teams claimed entry to T-Cellular worker instruments. Star Chat was answerable for a majority of those incidents. Picture: krebsonsecurity.com.
A evaluate of EarthtoStar’s messages on Star Chat as listed by the menace intelligence agency Flashpoint reveals this individual additionally bought “AT&T e-mail resets” and AT&T name forwarding providers for as much as $1,200 per line. EarthtoStar defined the aim of this service in submit on Telegram:
“Okay persons are confused, so you understand when u login to chase and it says ‘2fa required’ or regardless of the fuck, nicely it provides you two choices, SMS or Name. For those who press name, and I ahead the road to you then who do you assume will get mentioned name?”
New Jersey prosecutors allege Jubair additionally was concerned in a mass SMS phishing marketing campaign in the course of the summer season of 2022 that stole single sign-on credentials from workers at a whole lot of firms. The textual content messages requested customers to click on a hyperlink and log in at a phishing web page that mimicked their employer’s Okta authentication web page, saying recipients wanted to evaluate pending modifications to their upcoming work schedules.
The phishing web sites used a Telegram prompt message bot to ahead any submitted credentials in real-time, permitting the attackers to make use of the phished username, password and one-time code to log in as that worker at the true employer web site.
That weeks-long SMS phishing marketing campaign led to intrusions and knowledge thefts at greater than 130 organizations, together with LastPass, DoorDash, Mailchimp, Plex and Sign.

A visible depiction of the assaults by the SMS phishing group often called 0ktapus, ScatterSwine, and Scattered Spider. Picture: Amitai Cohen twitter.com/amitaico.
DA, COMRADE
EarthtoStar’s group Star Chat specialised in phishing their approach into enterprise course of outsourcing (BPO) firms that present buyer assist for a variety of multinational firms, together with a lot of the world’s largest telecommunications suppliers. In Could 2022, EarthtoStar posted to the Telegram channel “Frauwudchat”:
“Hello, I’m on the lookout for companions with a purpose to exfiltrate knowledge from massive telecommunications firms/name facilities/alike, I’ve main expertise on this discipline, [including] a large name heart which homes 200,000+ workers the place I’ve dumped all consumer credentials and gained entry to the [domain controller] + obtained world administrator I even have expertise with REST API’s and programming. I’ve intensive expertise with VPN, Citrix, cisco anyconnect, social engineering + privilege escalation. When you’ve got any Citrix/Cisco VPN or some other helpful issues please message me and lets work.”
At across the identical time within the Summer time of 2022, a minimum of two completely different accounts tied to Star Chat — “RocketAce” and “Lopiu” — launched the group’s providers to denizens of the Russian-language cybercrime discussion board Exploit, together with:
-SIM-swapping providers concentrating on Verizon and T-Cellular prospects;
-Dynamic phishing pages concentrating on prospects of single sign-on suppliers like Okta;
-Malware growth providers;
-The sale of prolonged validation (EV) code signing certificates.
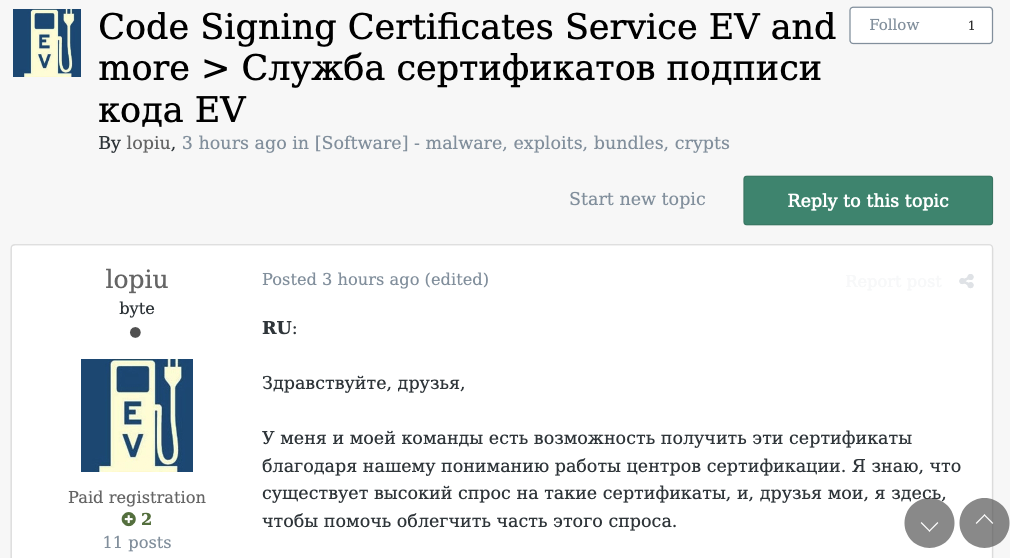
The consumer “Lopiu” on the Russian cybercrime discussion board Exploit marketed most of the identical distinctive providers supplied by EarthtoStar and different Star Chat members. Picture supply: ke-la.com.
These two accounts on Exploit created a number of gross sales threads by which they claimed administrative entry to U.S. telecommunications suppliers and requested different Exploit members for assist in monetizing that entry. In June 2022, RocketAce, which seems to have been simply considered one of EarthtoStar’s many aliases, posted to Exploit:
Howdy. I’ve entry to a telecommunications firm’s citrix and vpn. I would love somebody to assist me escape of the system and probably assault the area controller so all logins might be extracted we will talk about fee and issues depart your telegram within the feedback or non-public message me ! On the lookout for somebody with information in citrix/privilege escalation
On Nov. 15, 2022, EarthtoStar posted to their Star Sanctuary Telegram channel that they had been hiring malware builders with a minimal of three years of expertise and the flexibility to develop rootkits, backdoors and malware loaders.
“Non-compulsory: Endorsed by superior APT Teams (e.g. Conti, Ryuk),” the advert concluded, referencing two of Russia’s most rapacious and damaging ransomware affiliate operations. “A part of a nation-state / ex-3l (3 letter-agency).”
2023-PRESENT DAY
The Telegram and Discord chat channels whereby Flowers and Jubair allegedly deliberate and executed their extortion assaults are a part of a loose-knit community often called the Com, an English-speaking cybercrime neighborhood consisting principally of people dwelling in the US, the UK, Canada and Australia.
Many of those Com chat servers have a whole lot to 1000’s of members every, and among the extra attention-grabbing solicitations on these communities are job provides for in-person assignments and duties that may be discovered if one searches for posts titled, “For those who reside close to,” or “IRL job” — quick for “in actual life” job.
These “violence-as-a-service” solicitations sometimes contain “brickings,” the place somebody is employed to toss a brick by way of the window at a specified tackle. Different IRL jobs for rent embody tire-stabbings, molotov cocktail hurlings, drive-by shootings, and even residence invasions. The folks focused by these providers are sometimes different criminals inside the neighborhood, but it surely’s common to see Com members asking others for assist in harassing or intimidating safety researchers and even the very regulation enforcement officers who’re investigating their alleged crimes.
It stays unclear what precipitated this incident or what adopted instantly after, however on January 13, 2023, a Star Sanctuary account utilized by EarthtoStar solicited the house invasion of a sitting U.S. federal prosecutor from New York. That submit included a photograph of the prosecutor taken from the Justice Division’s web site, together with the message:
“Want irl niggas, in residence hostage shit no fucking pussies no skinny glock holding 100 pound niggas both”
All through late 2022 and early 2023, EarthtoStar’s alias “Brad” (a.okay.a. “Brad_banned”) continuously marketed Star Chat’s malware growth providers, together with customized malicious software program designed to cover the attacker’s presence on a sufferer machine:
We will develop KERNEL malware which can obtain persistence for a very long time,
bypass firewalls and have reverse shell entry.This shit is actually like STAGE 4 CANCER FOR COMPUTERS!!!
Kernel that means the best degree of authority on a machine.
This will vary to easy shells to Bootkits.Bypass all main EDR’s (SentinelOne, CrowdStrike, and so on)
Patch EDR’s scanning performance so it’s rendered ineffective!As soon as implanted, extraordinarily tough to take away (principally unimaginable to even discover)
Improvement Expertise of a number of years and in a number of APT Teams.Be one step forward of the sport. Costs begin from $5,000+. Message @brad_banned to get a quote
In September 2023 , each MGM Resorts and Caesars Leisure suffered ransomware assaults by the hands of a Russian ransomware associates program often called ALPHV and BlackCat. Caesars reportedly paid a $15 million ransom in that incident.
Inside hours of MGM publicly acknowledging the 2023 breach, members of Scattered Spider had been claiming credit score and telling reporters they’d damaged in by social engineering a third-party IT vendor. At a listening to in London final week, U.Ok. prosecutors instructed the court docket Jubair was present in possession of greater than $50 million in ill-gotten cryptocurrency, together with funds that had been linked to the Las Vegas on line casino hacks.
The Star Chat channel was lastly banned by Telegram on March 9, 2025. However U.S. prosecutors say Jubair and fellow Scattered Spider members continued their hacking, phishing and extortion actions up till September 2025.
In April 2025, the Com was buzzing concerning the publication of “The Com Forged,” a prolonged screed detailing Jubair’s alleged cybercriminal actions and nicknames through the years. This account included images and voice recordings allegedly of Jubair, and asserted that in his early days on the Com Jubair used the nicknames Clark and Miku (these are each aliases utilized by Everlynn in reference to their pretend EDR providers).

Thalha Jubair (proper), with out his large-rimmed glasses, in an undated picture posted in The Com Forged.
Extra just lately, the nameless Com Forged creator(s) claimed, Jubair had used the nickname “Operator,” which corresponds to a Com member who ran an automatic Telegram-based doxing service that pulled shopper information from hacked knowledge dealer accounts. That public outing got here after Operator allegedly seized management over the Doxbin, a long-running and extremely poisonous neighborhood that’s used to “dox” or submit deeply private data on folks.
“Operator/Clark/Miku: A key member of the ransomware group Scattered Spider, which consists of a various combine of people concerned in SIM swapping and phishing,” the Com Forged account said. “The group is an amalgamation of a number of key organizations, together with Infinity Recursion (owned by Operator), True Alcorians (owned by earth2star), and Lapsus, which have come collectively to type a single collective.”
The New Jersey criticism (PDF) alleges Jubair and different Scattered Spider members dedicated laptop fraud, wire fraud, and cash laundering in relation to a minimum of 120 laptop community intrusions involving 47 U.S. entities between Could 2022 and September 2025. The criticism alleges the group’s victims paid a minimum of $115 million in ransom funds.
U.S. authorities say they traced a few of these funds to Scattered Spider to an Web server managed by Jubair. The criticism states {that a} cryptocurrency pockets found on that server was used to buy a number of reward playing cards, considered one of which was used at a meals supply firm to ship meals to his house. One other reward card bought with cryptocurrency from the identical server was allegedly used to fund on-line gaming accounts below Jubair’s identify. U.S. prosecutors mentioned that once they seized that server additionally they seized $36 million in cryptocurrency.
The criticism additionally expenses Jubair with involvement in a hacking incident in January 2025 in opposition to the U.S. courts system that focused a U.S. Justice of the Peace choose overseeing a associated Scattered Spider investigation. That different investigation seems to have been the prosecution of Noah Michael City, a 20-year-old Florida man charged in November 2024 by prosecutors in Los Angeles as considered one of 5 alleged Scattered Spider members.
City pleaded responsible in April 2025 to wire fraud and conspiracy expenses, and in August he was sentenced to 10 years in federal jail. Talking with KrebsOnSecurity from jail after his sentencing, City asserted that the choose case gave him extra time than prosecutors requested as a result of he was mad that Scattered Spider hacked his e-mail account.
Noah “Kingbob” City, posting to Twitter/X across the time of his sentencing on Aug. 20.
A court docket transcript (PDF) from a standing listening to in February 2025 reveals City was telling the reality concerning the hacking incident that occurred whereas he was in federal custody. The choose instructed attorneys for each side {that a} co-defendant within the California case was looking for out about Mr. City’s exercise within the Florida case, and that the hacker accessed the account by impersonating a choose over the cellphone and requesting a password reset.
Allison Nixon is chief analysis officer on the New York primarily based safety agency Unit 221B, and simply one of many world’s main consultants on Com-based cybercrime exercise. Nixon mentioned the core downside with legally prosecuting well-known cybercriminals from the Com has historically been that the highest offenders are typically below the age of 18, and thus tough to cost below federal hacking statutes.
In the US, prosecutors sometimes wait till an underage cybercrime suspect turns into an grownup to cost them. However till that day comes, she mentioned, Com actors usually really feel emboldened to proceed committing — and fairly often bragging about — severe cybercrime offenses.
“Right here now we have a particular class of Com offenders that successfully take pleasure in authorized immunity,” Nixon instructed KrebsOnSecurity. “Most get recruited to Com teams when they’re older, however of those who be part of very younger, resembling 12 or 13, they appear to be essentially the most harmful as a result of at that age they haven’t any grounding in actuality and a lot longevity earlier than they exit their authorized immunity.”
Nixon mentioned U.Ok. authorities face the identical problem once they briefly detain and search the houses of underage Com suspects: Specifically, the teenager suspects merely go proper again to their respective cliques within the Com and begin robbing and hurting folks once more the minute they’re launched.
Certainly, the U.Ok. court docket heard from prosecutors final week that each Scattered Spider suspects had been detained and/or searched by native regulation enforcement on a number of events, solely to return to the Com lower than 24 hours after being launched every time.
“What we see is these younger Com members turn out to be vectors for perpetrators to commit enormously dangerous acts and even youngster abuse,” Nixon mentioned. “The members of this particular class of people that take pleasure in authorized immunity are assembly up with overseas nationals and conducting these generally heinous acts at their behest.”
Nixon mentioned many of those people have few mates in actual life as a result of they spend nearly all of their waking hours on Com channels, and so their whole sense of identification, neighborhood and self-worth will get wrapped up of their involvement with these on-line gangs. She mentioned if the regulation was such that prosecutors might deal with these folks commensurate with the quantity of hurt they trigger society, that will in all probability clear up numerous this downside.
“If regulation enforcement was allowed to maintain them in jail, they’d give up reoffending,” she mentioned.
The Instances of London studies that Flowers is going through three expenses below the Laptop Misuse Act: two of conspiracy to commit an unauthorized act in relation to a pc inflicting/creating threat of great injury to human welfare/nationwide safety and considered one of trying to commit the identical act. Most sentences for these offenses can vary from 14 years to life in jail, relying on the influence of the crime.
Jubair is reportedly going through two expenses within the U.Ok.: Considered one of conspiracy to commit an unauthorized act in relation to a pc inflicting/creating threat of great injury to human welfare/nationwide safety and considered one of failing to adjust to a piece 49 discover to reveal the important thing to protected data.
In the US, Jubair is charged with laptop fraud conspiracy, two counts of laptop fraud, wire fraud conspiracy, two counts of wire fraud, and cash laundering conspiracy. If extradited to the U.S., tried and convicted on all expenses, he faces a most penalty of 95 years in jail.
In July 2025, the UK barred victims of hacking from paying ransoms to cybercriminal teams until accepted by officers. U.Ok. organizations which are thought of a part of essential infrastructure reportedly will face an entire ban, as will the complete public sector. U.Ok. victims of a hack are actually required to inform officers to higher inform policymakers on the size of Britain’s ransomware downside.
For additional studying (bless you), take a look at Bloomberg’s poignant story final week primarily based on a yr’s value of jailhouse interviews with convicted Scattered Spider member Noah City.

