
Safety researchers at Apiiro have launched two free, open-source instruments designed to detect and block malicious code earlier than they’re added to software program initiatives to curb provide chain assaults.
The 2 instruments include a complete ruleset for Semgrep and Opengrep designed to detect malicious code patterns with minimal false positives and PRevent, a GitHub-integrated scanner, that detects and alerts on suspicious code in pull requests (PRs).
Based on Apiiro‘s safety researcher Matan Giladi, the instruments have a minimal false optimistic detection charge, making them notably invaluable in real-world observe.
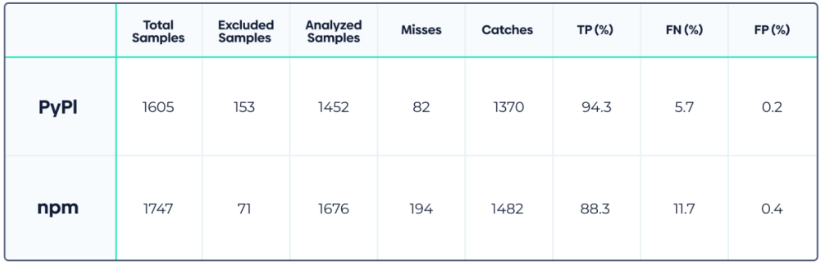
Particularly, the detection accuracy of the ruleset for PyPI packages is 94.3%, whereas it drops to the nonetheless spectacular 88.4% for npm packages. PRevent efficiently flags malicious PRs in 91.5% of the examined circumstances.
Supply: Apiiro
Catching malicious code
Apiiro’s malicious code detection technique relies on figuring out “code anti-patterns,” that are suspicious patterns in code that show behaviors which can be uncommon in respectable code however widespread in malware.
The detection system makes use of static evaluation, that means it examines code with out executing it, protecting the surroundings secure from unintentional infections.
These anti-patterns embrace:
- Numerous obfuscation strategies like encoding, nested transformations, and runtime modifications that assist disguise the code’s performance and intent.
- Use of exec(), eval(), or comparable capabilities, which permit arbitrary code execution at runtime.
- Code that downloads and executes distant payloads from exterior, unknown servers.
- Strategies for exfiltrating delicate consumer information to exterior places.
This ruleset could be built-in into CI/CD pipelines for automated repository scanning, used for scanning npm and PyPI packages, or tailored to different platforms utilizing Semgrep or Opengrep.
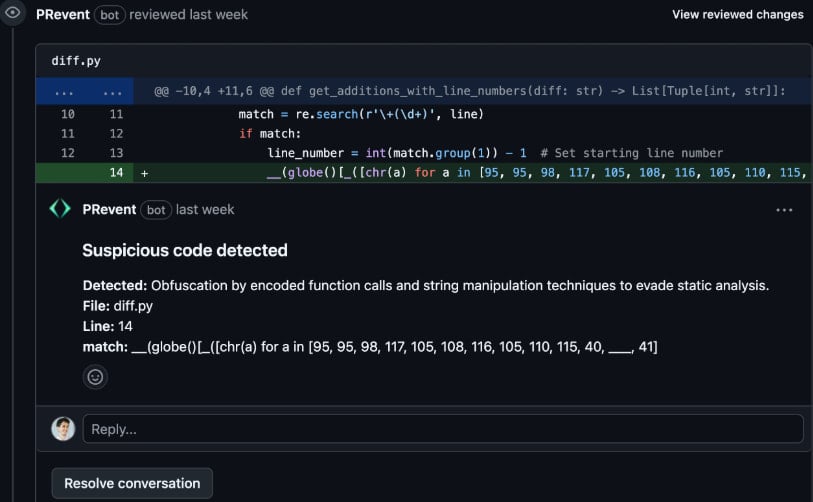
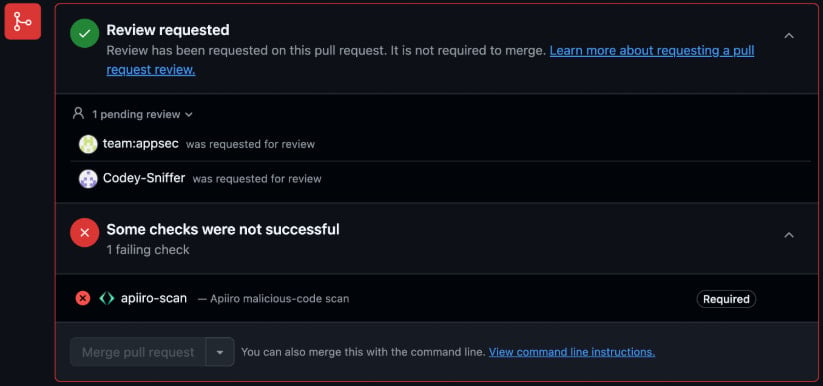
PRevent, which makes use of the identical anti-patterns, is designed to scan pull request occasions in real-time earlier than code is merged, stopping any threats earlier than they attain manufacturing.
Supply: Apiiro
It may be set to dam the merging till a certified reviewer approves it or add feedback on detected points to make sure builders are alerted of the dangers.
Supply: Apiiro
Apiiro acknowledges that its instruments are nonetheless virtually restricted, as they can’t detect malware hidden in compiled binaries nor scan npm and PyPI packages instantly, however plans so as to add extra options like deep code evaluation and AI-assisted scans in future updates.
Each the malicious code detection ruleset and the PRevent software can be found without cost on GitHub, with directions on the way to use them.
BleepingComputer has not examined these safety instruments and can’t assure their effectiveness or security.

