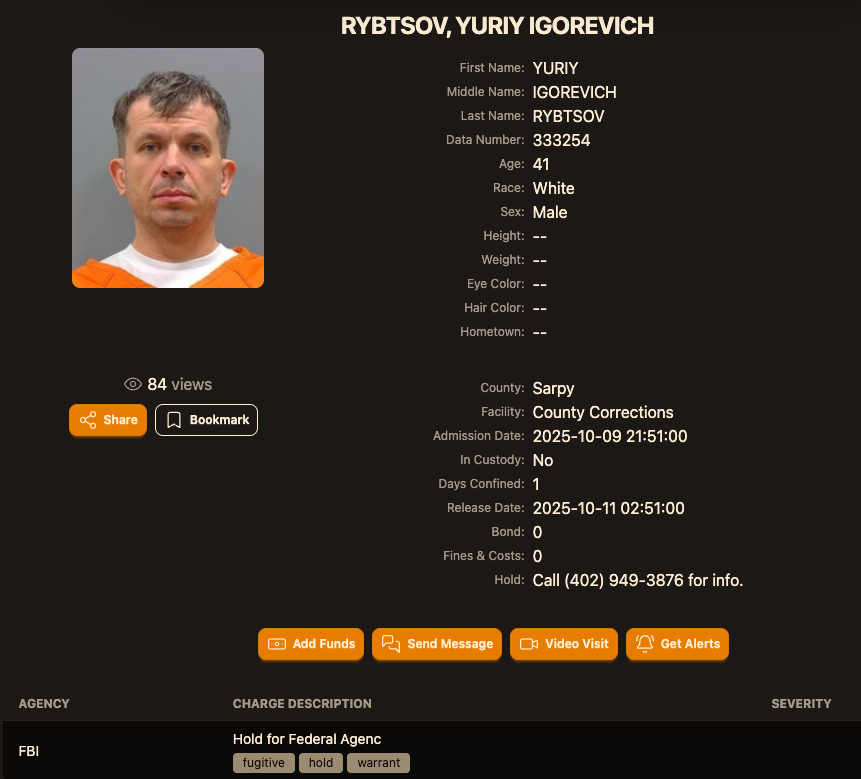
A Ukrainian man indicted in 2012 for conspiring with a prolific hacking group to steal tens of tens of millions of {dollars} from U.S. companies was arrested in Italy and is now in custody in the US, KrebsOnSecurity has discovered.
Sources near the investigation say Yuriy Igorevich Rybtsov, a 41-year-old from the Russia-controlled metropolis of Donetsk, Ukraine, was beforehand referenced in U.S. federal charging paperwork solely by his on-line deal with “MrICQ.” In response to a 13-year-old indictment (PDF) filed by prosecutors in Nebraska, MrICQ was a developer for a cybercrime group often called “Jabber Zeus.”
Picture: lockedup dot wtf.
The Jabber Zeus identify is derived from the malware they used — a customized model of the ZeuS banking trojan — that stole banking login credentials and would ship the group a Jabber on the spot message every time a brand new sufferer entered a one-time passcode at a monetary establishment web site. The gang focused principally small to mid-sized companies, and so they had been an early pioneer of so-called “man-in-the-browser” assaults, malware that may silently intercept any knowledge that victims submit in a web-based kind.
As soon as inside a sufferer firm’s accounts, the Jabber Zeus crew would modify the agency’s payroll so as to add dozens of “cash mules,” folks recruited by way of elaborate work-at-home schemes to deal with financial institution transfers. The mules in flip would ahead any stolen payroll deposits — minus their commissions — through wire transfers to different mules in Ukraine and the UK.
The 2012 indictment focusing on the Jabber Zeus crew named MrICQ as “John Doe #3,” and mentioned this individual dealt with incoming notifications of newly compromised victims. The Division of Justice (DOJ) mentioned MrICQ additionally helped the group launder the proceeds of their heists by way of digital foreign money trade companies.
Two sources aware of the Jabber Zeus investigation mentioned Rybtsov was arrested in Italy, though the precise date and circumstances of his arrest stay unclear. A abstract of latest choices (PDF) revealed by the Italian Supreme Court docket states that in April 2025, Rybtsov misplaced a closing enchantment to keep away from extradition to the US.
In response to the mugshot web site lockedup[.]wtf, Rybtsov arrived in Nebraska on October 9, and was being held beneath an arrest warrant from the U.S. Federal Bureau of Investigation (FBI).
The information breach monitoring service Constella Intelligence discovered breached data from the enterprise profiling web site bvdinfo[.]com displaying {that a} 41-year-old Yuriy Igorevich Rybtsov labored in a constructing at 59 Barnaulska St. in Donetsk. Additional looking on this deal with in Constella finds the identical residence constructing was shared by a enterprise registered to Vyacheslav “Tank” Penchukov, the chief of the Jabber Zeus crew in Ukraine.

Vyacheslav “Tank” Penchukov, seen right here performing as “DJ Slava Wealthy” in Ukraine, in an undated picture from social media.
Penchukov was arrested in 2022 whereas touring to satisfy his spouse in Switzerland. Final yr, a federal courtroom in Nebraska sentenced Penchukov to 18 years in jail and ordered him to pay greater than $73 million in restitution.
Lawrence Baldwin is founding father of myNetWatchman, a menace intelligence firm based mostly in Georgia that started monitoring and disrupting the Jabber Zeus gang in 2009. myNetWatchman had secretly gained entry to the Jabber chat server utilized by the Ukrainian hackers, permitting Baldwin to snoop on the day by day conversations between MrICQ and different Jabber Zeus members.
Baldwin shared these real-time chat data with a number of state and federal regulation enforcement companies, and with this reporter. Between 2010 and 2013, I spent a number of hours every day alerting small companies throughout the nation that their payroll accounts had been about to be drained by these cybercriminals.
These notifications, and Baldwin’s tireless efforts, saved numerous would-be victims a substantial amount of cash. Normally, nevertheless, we had been already too late. Nonetheless, the pilfered Jabber Zeus group chats supplied the idea for dozens of tales revealed right here about small companies preventing their banks in courtroom over six- and seven-figure monetary losses.
Baldwin mentioned the Jabber Zeus crew was far forward of its friends in a number of respects. For starters, their intercepted chats confirmed they labored to create a extremely personalized botnet straight with the creator of the unique Zeus Trojan — Evgeniy Mikhailovich Bogachev, a Russian man who has lengthy been on the FBI’s “Most Needed” listing. The feds have a standing $3 million reward for info resulting in Bogachev’s arrest.

Evgeniy M. Bogachev, in undated images.
The core innovation of Jabber Zeus was an alert that MrICQ would obtain every time a brand new sufferer entered a one-time password code right into a phishing web page mimicking their monetary establishment. The gang’s inside identify for this part was “Leprechaun,” (the video beneath from myNetWatchman exhibits it in motion). Jabber Zeus would really re-write the HTML code as displayed within the sufferer’s browser, permitting them to intercept any passcodes despatched by the sufferer’s financial institution for multi-factor authentication.
“These guys had compromised such numerous victims that they had been getting buried in a tsunami of stolen banking credentials,” Baldwin instructed KrebsOnSecurity. “However the entire level of Leprechaun was to isolate the highest-value credentials — the business financial institution accounts with two-factor authentication turned on. They knew these had been far juicier targets as a result of they clearly had much more cash to guard.”
Baldwin mentioned the Jabber Zeus trojan additionally included a customized “backconnect” part that allowed the hackers to relay their checking account takeovers by way of the sufferer’s personal contaminated PC.
“The Jabber Zeus crew had been actually connecting to the sufferer’s checking account from the sufferer’s IP deal with, or from the distant management operate and by absolutely emulating the machine,” he mentioned. “That trojan was like a sizzling knife by way of butter of what everybody thought was state-of-the-art safe on-line banking on the time.”
Though the Jabber Zeus crew was in direct contact with the Zeus creator, the chats intercepted by myNetWatchman present Bogachev continuously ignored the group’s pleas for assist. The federal government says the actual chief of the Jabber Zeus crew was Maksim Yakubets, a 38-year Ukrainian man with Russian citizenship who glided by the hacker deal with “Aqua.”

Alleged Evil Corp chief Maksim “Aqua” Yakubets. Picture: FBI
The Jabber chats intercepted by Baldwin present that Aqua interacted virtually day by day with MrICQ, Tank and different members of the hacking staff, typically facilitating the group’s cash mule and cashout actions remotely from Russia.
The federal government says Yakubets/Aqua would later emerge because the chief of an elite cybercrime ring of no less than 17 hackers that referred to themselves internally as “Evil Corp.” Members of Evil Corp developed and used the Dridex (a.ok.a. Bugat) trojan, which helped them siphon greater than $100 million from lots of of sufferer corporations in the US and Europe.
This 2019 story in regards to the authorities’s $5 million bounty for info resulting in Yakubets’s arrest contains excerpts of conversations between Aqua, Tank, Bogachev and different Jabber Zeus crew members discussing tales I’d written about their victims. Each Baldwin and I had been interviewed at size for a brand new weekly six-part podcast by the BBC that delves deep into the historical past of Evil Corp. Episode One focuses on the evolution of Zeus, whereas the second episode facilities on an investigation into the group by former FBI agent Jim Craig.

Picture: https://www.bbc.co.uk/programmes/w3ct89y8

