Aisuru, the botnet accountable for a collection of record-smashing distributed denial-of-service (DDoS) assaults this 12 months, just lately was overhauled to help a extra low-key, profitable and sustainable enterprise: Renting a whole bunch of hundreds of contaminated Web of Issues (IoT) units to proxy companies that assist cybercriminals anonymize their visitors. Specialists say a glut of proxies from Aisuru and different sources is fueling large-scale knowledge harvesting efforts tied to numerous synthetic intelligence (AI) tasks, serving to content material scrapers evade detection by routing their visitors by way of residential connections that seem like common Web customers.
First recognized in August 2024, Aisuru has unfold to at the least 700,000 IoT methods, equivalent to poorly secured Web routers and safety cameras. Aisuru’s overlords have used their huge botnet to clobber targets with headline-grabbing DDoS assaults, flooding focused hosts with blasts of junk requests from all contaminated methods concurrently.
In June, Aisuru hit KrebsOnSecurity.com with a DDoS clocking at 6.3 terabits per second — the largest assault that Google had ever mitigated on the time. Within the weeks and months that adopted, Aisuru’s operators demonstrated DDoS capabilities of almost 30 terabits of knowledge per second — nicely past the assault mitigation capabilities of most Web locations.
These digital sieges have been notably disruptive this 12 months for U.S.-based Web service suppliers (ISPs), partially as a result of Aisuru just lately succeeded in taking on a lot of IoT units in america. And when Aisuru launches assaults, the quantity of outgoing visitors from contaminated methods on these ISPs is usually so excessive that it may well disrupt or degrade Web service for adjoining (non-botted) clients of the ISPs.
“A number of broadband entry community operators have skilled important operational influence as a consequence of outbound DDoS assaults in extra of 1.5Tb/sec launched from Aisuru botnet nodes residing on end-customer premises,” wrote Roland Dobbins, principal engineer at Netscout, in a current govt abstract on Aisuru. “Outbound/crossbound assault visitors exceeding 1Tb/sec from compromised buyer premise tools (CPE) units has prompted important disruption to wireline and wi-fi broadband entry networks. Excessive-throughput assaults have prompted chassis-based router line card failures.”
The incessant assaults from Aisuru have caught the eye of federal authorities in america and Europe (lots of Aisuru’s victims are clients of ISPs and internet hosting suppliers primarily based in Europe). Fairly just lately, among the world’s largest ISPs have began informally sharing block lists figuring out the quickly shifting areas of the servers that the attackers use to manage the actions of the botnet.
Specialists say the Aisuru botmasters just lately up to date their malware in order that compromised units can extra simply be rented to so-called “residential proxy” suppliers. These proxy companies enable paying clients to route their Web communications by way of another person’s machine, offering anonymity and the flexibility to look as an everyday Web person in nearly any main metropolis worldwide.

From a web site’s perspective, the IP visitors of a residential proxy community person seems to originate from the rented residential IP handle, not from the proxy service buyer. Proxy companies can be utilized in a respectable method for a number of enterprise functions — equivalent to worth comparisons or gross sales intelligence. However they’re massively abused for hiding cybercrime exercise (assume promoting fraud, credential stuffing) as a result of they’ll make it tough to hint malicious visitors to its authentic supply.
And as we’ll see in a second, this whole shadowy trade seems to be shifting its focus towards enabling aggressive content material scraping exercise that constantly feeds uncooked knowledge into giant language fashions (LLMs) constructed to help numerous AI tasks.
‘INSANE’ GROWTH
Riley Kilmer is co-founder of spur.us, a service that tracks proxy networks. Kilmer stated the entire high proxy companies have grown exponentially over the previous six months — with some including between 10 to 200 instances extra proxies for lease.
“I simply checked, and within the final 90 days we’ve seen 250 million distinctive residential proxy IPs,” Kilmer stated. “That’s insane. That’s so excessive of a quantity, it’s remarkable. These proxies are completely all over the place now.”
To place Kilmer’s feedback in perspective, right here was Spur’s view of the High 10 proxy networks by approximate set up base, circa Might 2025:
AUPROXIES_PROXY 66,097
RAYOBYTE_PROXY 43,894
OXYLABS_PROXY 43,008
WEBSHARE_PROXY 39,800
IPROYAL_PROXY 32,723
PROXYCHEAP_PROXY 26,368
IPIDEA_PROXY 26,202
MYPRIVATEPROXY_PROXY 25,287
HYPE_PROXY 18,185
MASSIVE_PROXY 17,152
Immediately, Spur says it’s monitoring an unprecedented spike in out there proxies throughout all suppliers, together with;
LUMINATI_PROXY 11,856,421
NETNUT_PROXY 10,982,458
ABCPROXY_PROXY 9,294,419
OXYLABS_PROXY 6,754,790
IPIDEA_PROXY 3,209,313
EARNFM_PROXY 2,659,913
NODEMAVEN_PROXY 2,627,851
INFATICA_PROXY 2,335,194
IPROYAL_PROXY 2,032,027
YILU_PROXY 1,549,155
Reached for remark concerning the obvious fast development of their proxy community, Oxylabs (#4 on Spur’s checklist) stated whereas their proxy pool did develop just lately, it did so at nowhere close to the speed cited by Spur.
“We don’t systematically monitor different suppliers’ figures, and we’re not conscious of any cases of 10× or 100× development, particularly on the subject of a number of greater firms which might be respectable companies,” the corporate stated in a written assertion.
Shiny Knowledge was previously referred to as Luminati Networks, the identify that’s presently on the high of Spur’s checklist of the largest residential proxy networks, with greater than 11 million proxies. Shiny Knowledge likewise advised KrebsOnSecurity that Spur’s present estimates of its proxy community are dramatically overstated and inaccurate.
“We didn’t actively provoke nor will we see any 10x or 100x enlargement of our community, which leads me to imagine that somebody is perhaps presenting these IPs as Shiny Knowledge’s in a roundabout way,” stated Rony Shalit, Shiny Knowledge’s chief compliance and ethics officer. “In lots of instances up to now, as a consequence of us being the main knowledge assortment proxy supplier, IPs had been falsely tagged as being a part of our community, or whereas being utilized by different proxy suppliers for malicious exercise.”
“Our community is barely sourced from verified IP suppliers and a sturdy opt-in solely residential friends, which we work onerous and in full transparency to acquire,” Shalit continued. “Each DC, ISP or SDK companion is reviewed and permitted, and each residential peer should actively decide in to be a part of our community.”
HK NETWORK
Even Spur acknowledges that Luminati and Oxylabs are in contrast to most different proxy companies on their high proxy suppliers checklist, in that these suppliers truly adhere to “know-your-customer” insurance policies, equivalent to requiring video calls with all clients, and strictly blocking clients from reselling entry.
Benjamin Brundage is founding father of Synthient, a startup that helps firms detect proxy networks. Brundage stated if there’s growing confusion round which proxy networks are essentially the most worrisome, it’s as a result of almost all of those lesser-known proxy companies have advanced into extremely incestuous bandwidth resellers. What’s extra, he stated, some proxy suppliers don’t admire being tracked and have been identified to take aggressive steps to confuse methods that scan the Web for residential proxy nodes.
Brundage stated most proxy companies in the present day have created their very own software program improvement package or SDK that different app builders can bundle with their code to earn income. These SDKs quietly modify the person’s machine in order that some portion of their bandwidth can be utilized to ahead visitors from proxy service clients.
“Proxy suppliers have swimming pools of regularly churning IP addresses,” he stated. “These IP addresses are sourced by way of numerous means, equivalent to bandwidth-sharing apps, botnets, Android SDKs, and extra. These suppliers will typically both instantly method resellers or provide a reseller program that permits customers to resell bandwidth by way of their platform.”
Many SDK suppliers say they require full consent earlier than permitting their software program to be put in on end-user units. Nonetheless, these opt-in agreements and consent checkboxes could also be little greater than a formality for cybercriminals just like the Aisuru botmasters, who can earn a fee every time one among their contaminated units is compelled to put in some SDK that allows a number of of those proxy companies.
Relying on its construction, a single supplier could function a whole bunch of various proxy swimming pools at a time — all maintained by way of different means, Brundage stated.
“Usually, you’ll see resellers sustaining their very own proxy pool along with an upstream supplier,” he stated. “It permits them to market a proxy pool to high-value shoppers and provide an infinite bandwidth plan for affordable scale back their very own prices.”
Some proxy suppliers seem like instantly in league with botmasters. Brundage recognized one proxy supplier that was aggressively promoting low-cost and plentiful bandwidth to content material scraping firms. After scanning that supplier’s pool of accessible proxies, Brundage stated he discovered a one-to-one match with IP addresses he’d beforehand mapped to the Aisuru botnet.
Brundage says that by nearly any measurement, the world’s largest residential proxy service is IPidea, a China-based proxy community. IPidea is #5 on Spur’s High 10, and Brundage stated its manufacturers embody ABCProxy (#3), Roxlabs, LunaProxy, PIA S5 Proxy, PyProxy, 922Proxy, 360Proxy, IP2World, and Cherry Proxy. Spur’s Kilmer stated in addition they monitor Yilu Proxy (#10) as IPidea.
Brundage stated all of those suppliers function below a company umbrella identified on the cybercrime boards as “HK Community.”
“The best way it really works is there’s this entire reseller ecosystem, the place IPidea will likely be extremely aggressive and method all these proxy suppliers with the provide, ‘Hey, in case you guys purchase bandwidth from us, we’ll offer you these superb reseller costs,’” Brundage defined. “However they’re additionally very aggressive in recruiting resellers for his or her apps.”
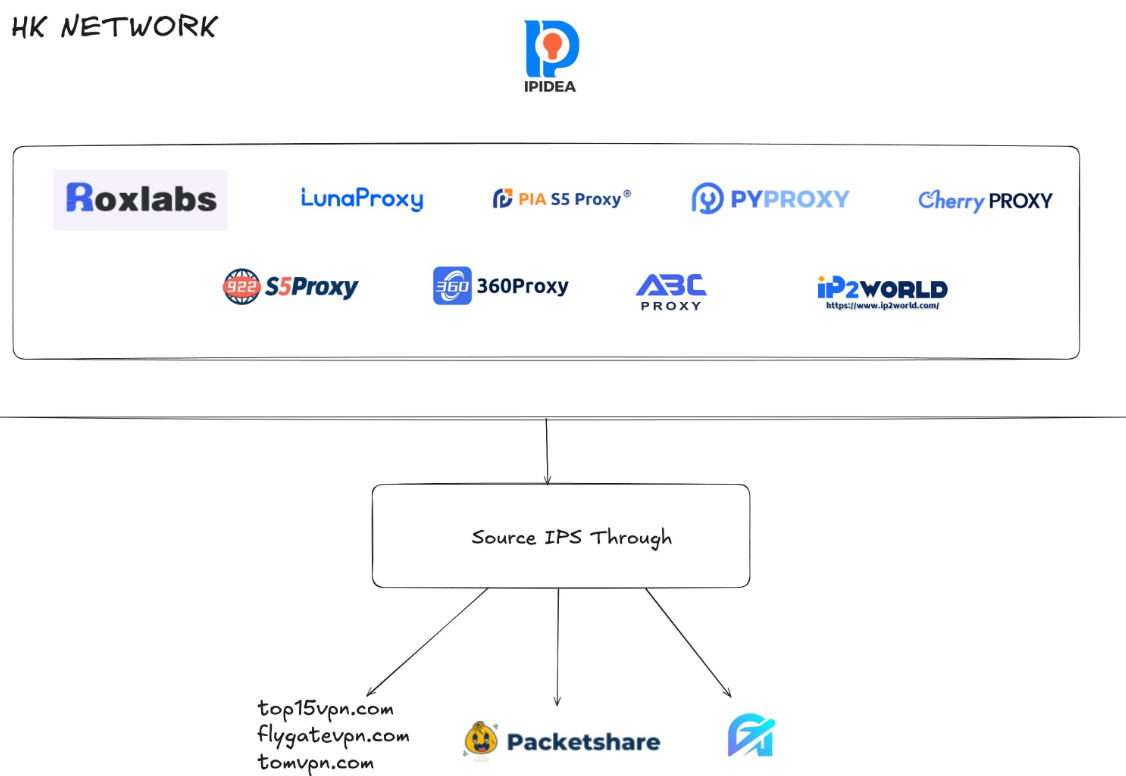
A graphic depicting the connection between proxy suppliers that Synthient discovered are white labeling IPidea proxies. Picture: Synthient.com.
These apps embody a spread of low-cost and “free” digital personal networking (VPN) companies that certainly enable customers to get pleasure from a free VPN, however which additionally flip the person’s machine right into a visitors relay that may be rented to cybercriminals, or else parceled out to numerous different proxy networks.
“They’ve all this bandwidth to dump,” Brundage stated of IPidea and its sister networks. “They usually can do it by way of their very own platforms, or they go get resellers to do it for them by promoting on sketchy hacker boards to achieve extra individuals.”
Considered one of IPidea’s core manufacturers is 922S5Proxy, which is a not-so-subtle nod to the 911S5Proxy service that was vastly in style between 2015 and 2022. In July 2022, KrebsOnSecurity revealed a deep dive into 911S5Proxy’s origins and obvious homeowners in China. Lower than per week later, 911S5Proxy introduced it was closing down after the corporate’s servers had been massively hacked.
That 2022 story named Yunhe Wang from Beijing because the obvious proprietor and/or supervisor of the 911S5 proxy service. In Might 2024, the U.S. Division of Justice arrested Mr Wang, alleging that his community was used to steal billions of {dollars} from monetary establishments, bank card issuers, and federal lending applications. On the identical time, the U.S. Treasury Division introduced sanctions in opposition to Wang and two different Chinese language nationals for working 911S5Proxy.
The web site for 922Proxy.
DATA SCRAPING FOR AI
In current months, a number of consultants who monitor botnet and proxy exercise have shared that a substantial amount of content material scraping which finally advantages AI firms is now leveraging these proxy networks to additional obfuscate their aggressive data-slurping exercise. That’s as a result of by routing it by way of residential IP addresses, content material scraping corporations could make their visitors far trickier to filter out.
“It’s actually tough to dam, as a result of there’s a danger of blocking actual individuals,” Spur’s Kilmer stated of the LLM scraping exercise that’s fed by way of particular person residential IP addresses, which are sometimes shared by a number of clients directly.
Kilmer says the AI trade has introduced a veneer of legitimacy to residential proxy enterprise, which has heretofore principally been related to sketchy affiliate cash making applications, automated abuse, and undesirable Web visitors.
“Net crawling and scraping has at all times been a factor, however AI made it like a commodity, knowledge that needed to be collected,” Kilmer stated. “Everyone wished to monetize their very own knowledge pots, and the way they monetize that’s completely different throughout the board.”
Kilmer stated many LLM-related scrapers depend on residential proxies in instances the place the content material supplier has restricted entry to their platform in a roundabout way, equivalent to forcing interplay by way of an app, or retaining all content material behind a login web page with multi-factor authentication.
“The place the price of knowledge is out of attain — there’s some exclusivity or cause they’ll’t entry the info — they’ll flip to residential proxies in order that they seem like an actual individual accessing that knowledge,” Kilmer stated of the content material scraping efforts.
Aggressive AI crawlers more and more are overloading community-maintained infrastructure, inflicting what quantities to persistent DDoS assaults on important public assets. A report earlier this 12 months from LibreNews discovered some open-source tasks now see as a lot as 97 % of their visitors originating from AI firm bots, dramatically growing bandwidth prices, service instability, and burdening already stretched-thin maintainers.
Cloudflare is now experimenting with instruments that may enable content material creators to cost a price to AI crawlers to scrape their web sites. The corporate’s “pay-per-crawl” characteristic is presently in a personal beta, and it lets publishers set their very own costs that bots should pay earlier than scraping content material.
On October 22, the social media and information community Reddit sued Oxylabs (PDF) and a number of other different proxy suppliers, alleging that their methods enabled the mass-scraping of Reddit person content material though Reddit had taken steps to dam such exercise.
“Recognizing that Reddit denies scrapers like them entry to its website, Defendants scrape the info from Google’s search outcomes as a substitute,” the lawsuit alleges. “They achieve this by masking their identities, hiding their areas, and disguising their net scrapers as common individuals (amongst different strategies) to bypass or bypass the safety restrictions meant to cease them.”
Denas Grybauskas, chief governance and technique officer at Oxylabs, stated the corporate was shocked and dissatisfied by the lawsuit.
“Reddit has made no try to talk with us instantly or talk any potential considerations,” Grybauskas stated in a written assertion. “Oxylabs has at all times been and can proceed to be a pioneer and an trade chief in public knowledge assortment, and it’ll not hesitate to defend itself in opposition to these allegations. Oxylabs’ place is that no firm ought to declare possession of public knowledge that doesn’t belong to them. It’s doable that it’s simply an try and promote the identical public knowledge at an inflated worth.”
As huge and highly effective as Aisuru could also be, it’s hardly the one botnet that’s contributing to the general broad availability of residential proxies. For instance, on June 5 the FBI’s Web Crime Criticism Middle warned that an IoT malware menace dubbed BADBOX 2.0 had compromised tens of millions of smart-TV packing containers, digital projectors, automobile infotainment models, image frames, and different IoT units.
In July, Google filed a lawsuit in New York federal courtroom in opposition to the Badbox botnet’s alleged perpetrators. Google stated the Badbox 2.0 botnet “compromised greater than 10 million uncertified units operating Android’s open-source software program, which lacks Google’s safety protections. Cybercriminals contaminated these units with pre-installed malware and exploited them to conduct large-scale advert fraud and different digital crimes.”
A FAMILIAR DOMAIN NAME
Brundage stated the Aisuru botmasters have their very own SDK, and for some cause a part of its code tells many newly-infected methods to question the area identify fuckbriankrebs[.]com. This can be little greater than an elaborate “screw you” to this website’s writer: One of many botnet’s alleged companions goes by the deal with “Forky,” and was recognized in June by KrebsOnSecurity as a younger man from Sao Paulo, Brazil.
Brundage famous that solely methods contaminated with Aisuru’s Android SDK will likely be compelled to resolve the area. Initially, there was some dialogue about whether or not the area may need some utility as a “kill change” able to disrupting the botnet’s operations, though Brundage and others interviewed for this story say that’s unlikely.
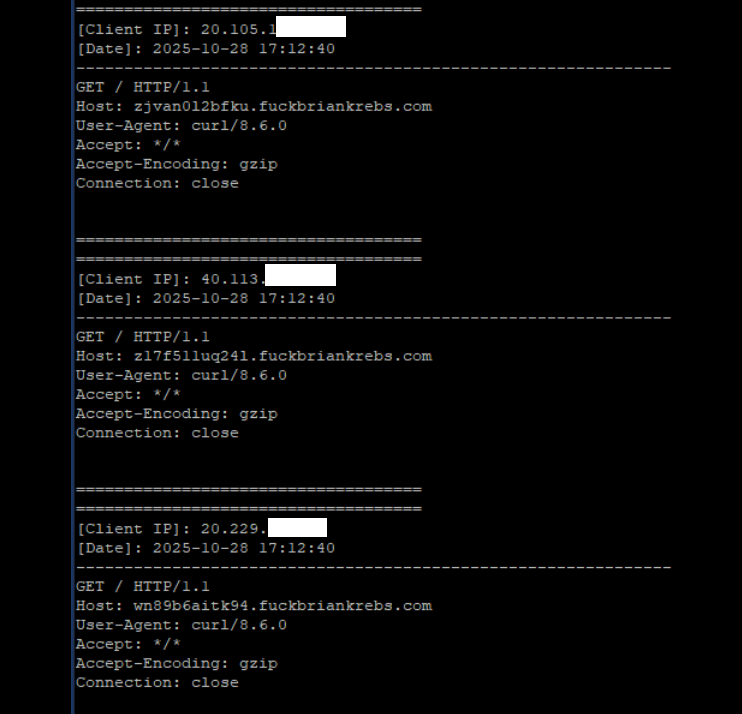
A tiny pattern of the visitors after a DNS server was enabled on the newly registered area fuckbriankrebs dot com. Every distinctive IP handle requested its personal distinctive subdomain. Picture: Seralys.
For one factor, they stated, if the area was by some means essential to the operation of the botnet, why was it nonetheless unregistered and actively for-sale? Why certainly, we requested. Fortunately, the area identify was deftly snatched up final week by Philippe Caturegli, “chief hacking officer” for the safety intelligence firm Seralys.
Caturegli enabled a passive DNS server on that area and inside a number of hours obtained greater than 700,000 requests for distinctive subdomains on fuckbriankrebs[.]com.
However even with that visibility into Aisuru, it’s tough to make use of this area check-in characteristic to measure its true dimension, Brundage stated. In any case, he stated, the methods which might be phoning dwelling to the area are solely a small portion of the general botnet.
“The bots are hardcoded to simply spam lookups on the subdomains,” he stated. “So anytime an an infection happens or it runs within the background, it should do a type of DNS queries.”

Caturegli briefly configured all subdomains on fuckbriankrebs dot com to show this ASCII artwork picture to visiting methods in the present day.
The area fuckbriankrebs[.]com has a storied historical past. On its preliminary launch in 2009, it was used to unfold malicious software program by the Cutwail spam botnet. In 2011, the area was concerned in a notable DDoS in opposition to this web site from a botnet powered by Russkill (a.okay.a. “Grime Jumper”).
Domaintools.com finds that in 2015, fuckbriankrebs[.]com was registered to an e mail handle attributed to David “Abdilo” Crees, a 27-year-old Australian man sentenced in Might 2025 to time served for cybercrime convictions associated to the Lizard Squad hacking group.

