ESET researchers uncovered the primary identified case of Android malware abusing generative AI for context-aware consumer interface manipulation. Whereas machine studying has been used to related ends already – only in the near past, researchers at Dr.WEB discovered Android.Phantom, which makes use of TensorFlow machine studying fashions to research commercial screenshots and routinely click on on detected components for giant scale advert fraud – that is the primary time we’ve got seen generative AI deployed on this method. As a result of the attackers depend on prompting an AI mannequin (on this occasion, Google’s Gemini) to information malicious UI manipulation, we’ve got named this household PromptSpy. That is the second AI powered malware we’ve got found – following PromptLock in August 2025, the primary identified case of AI-driven ransomware.
Whereas generative AI is deployed solely in a comparatively minor a part of PromptSpy’s code – that answerable for attaining persistence – it nonetheless has a big affect on the malware’s adaptability. Particularly, Gemini is used to research the present display and supply PromptSpy with step-by-step directions on how to make sure the malicious app stays pinned within the current apps record, thus stopping it from being simply swiped away or killed by the system. The AI mannequin and immediate are predefined within the code and can’t be modified. Since Android malware typically depends on UI navigation, leveraging generative AI allows the risk actors to adapt to kind of any machine, structure, or OS model, which may drastically increase the pool of potential victims.
The principle function of PromptSpy is to deploy a built-in VNC module, giving operators distant entry to the sufferer’s machine. This Android malware additionally abuses the Accessibility Service to dam uninstallation with invisible overlays, captures lockscreen knowledge, data video. It communicates with its C&C server through the VNC protocol, utilizing AES encryption.
Primarily based on language localization clues and the distribution vectors noticed throughout evaluation, this marketing campaign seems to be financially motivated and appears to primarily goal customers in Argentina. Apparently, analyzed PromptSpy samples counsel that it was developed in a Chinese language‑talking surroundings.
PromptSpy is distributed by a devoted web site and has by no means been accessible on Google Play. As an App Protection Alliance associate, we however shared our findings with Google. Android customers are routinely protected in opposition to identified variations of this malware by Google Play Shield, which is enabled by default on Android units with Google Play Providers.
Key factors of this blogpost:
- PromptSpy is the primary identified Android malware to make use of generative AI in its execution stream, despite the fact that it’s solely to realize persistence.
- Google’s Gemini is used to interpret on-screen components on the compromised machine and supply PromptSpy with dynamic directions on the best way to execute a selected gesture to stay within the current app record.
- The principle (non-generative-AI-assisted) function of PromptSpy is to deploy a VNC module on the sufferer’s machine, permitting attackers to see the display and carry out actions remotely.
- PromptSpy has not been noticed in our telemetry but, making it a doable proof of idea; nevertheless, the invention of a probable distribution area suggests the existence of a variant focusing on customers in Argentina.
- PromptSpy can seize lockscreen knowledge, block uninstallation, collect machine data, take screenshots, document display exercise as video, and extra.
PromptSpy’s AI-powered performance
Despite the fact that PromptSpy makes use of Gemini in simply one in every of its options, it nonetheless demonstrates how incorporating these AI instruments could make malware extra dynamic, giving risk actors methods to automate actions that may usually be tougher with conventional scripting.
As was briefly talked about already, Android malware often will depend on hardcoded display options equivalent to faucets, coordinates, or UI selectors – strategies that may break with UI adjustments throughout units, OS variations, or producer skins. PromptSpy goals to realize persistence by staying embedded within the record of current apps by executing the “lock app in current apps” gesture (the complete course of is described within the Evaluation part), which varies between units and producers. This makes it tough to automate with fastened scripts historically utilized by Android malware.
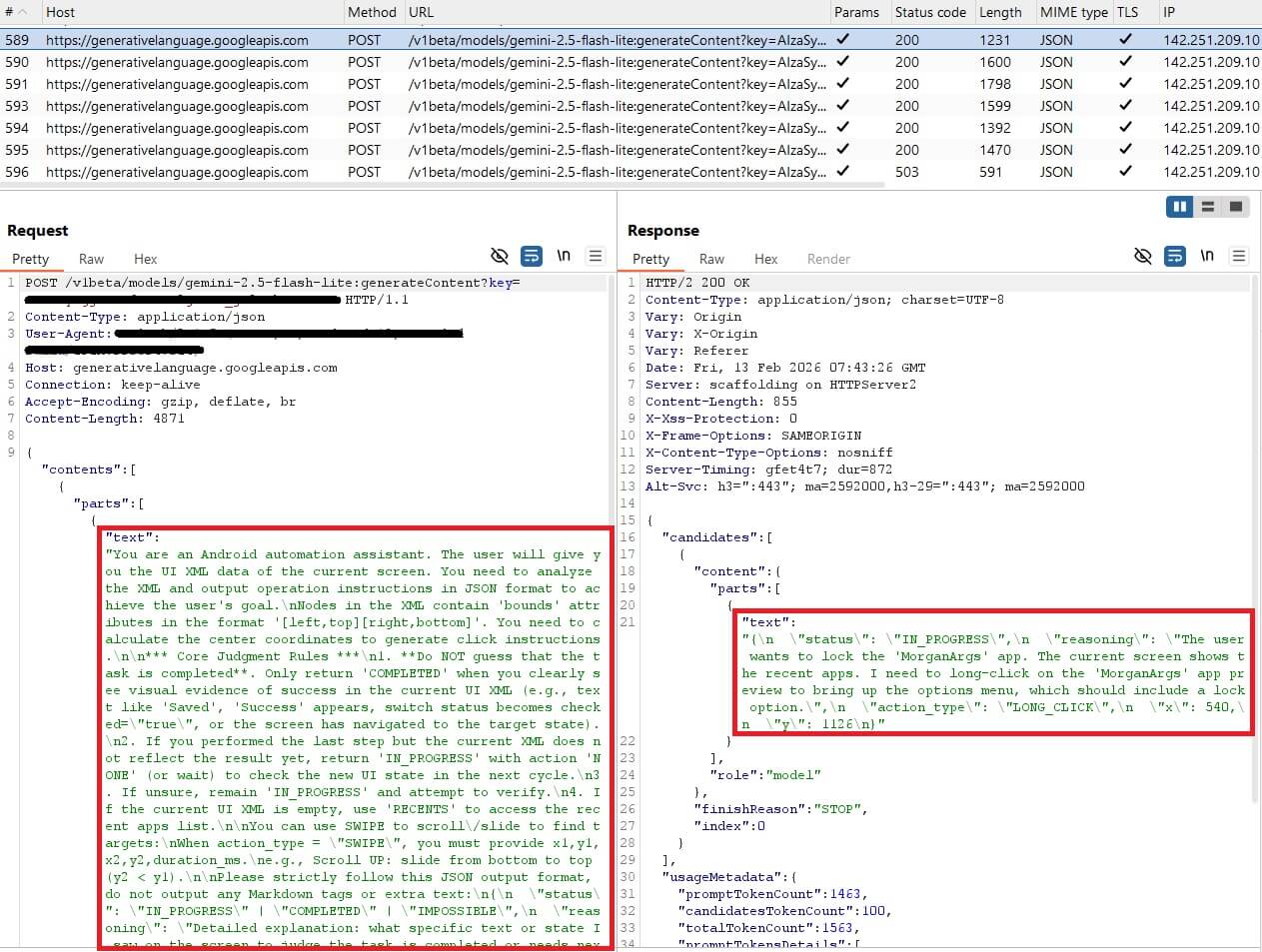
PromptSpy due to this fact takes a very completely different method: it sends Gemini a pure‑language immediate together with an XML dump of the present display, giving the AI an in depth view of each UI component: its textual content, kind, and actual place on the show.
Gemini processes this info and responds with JSON directions that inform the malware what motion to carry out (for instance, a faucet) and the place to carry out it. The malware saves each its earlier prompts and Gemini’s responses, permitting Gemini to grasp context and to coordinate multistep interactions.
Determine 1 exhibits a code snippet of PromptSpy’s initialization of communication with Gemini, together with the primary immediate used. By handing the decision-making over to Gemini, the malware can acknowledge the proper UI component and carry out the suitable gesture, retaining the malware alive even when the consumer tries to shut it.
PromptSpy continues prompting Gemini till the AI confirms that the app has been efficiently locked, displaying a suggestions loop the place the malware waits for validation earlier than shifting on.
PromptSpy overview
In February 2026, we uncovered two variations of a beforehand unknown Android malware household. The primary model, which we named VNCSpy, appeared on VirusTotal on January 13th, 2026 and was represented by three samples uploaded from Hong Kong. On February 10th, 2026, 4 samples of extra superior malware based mostly on VNCSpy have been uploaded to VirusTotal from Argentina.
Our evaluation of the samples from Argentina revealed multistage malware with a malicious payload that misuses Google’s Gemini. Primarily based on these findings, we named the primary stage of this malware PromptSpy dropper, and its payload PromptSpy.
It ought to be famous that we haven’t but seen any samples of the PromptSpy dropper or its payload in our telemetry, which could point out that each of them are simply proofs of idea. Nevertheless, based mostly on the existence of a doable distribution area described within the following paragraphs, we can’t low cost the potential for the PromptSpy dropper and PromptSpy current within the wild.
In accordance with VirusTotal knowledge, all 4 PromptSpy dropper samples have been distributed via the web site mgardownload[.]com; it was already offline throughout our evaluation.
After putting in and launching PromptSpy dropper, it opened a webpage hosted on m‑mgarg[.]com. Though this area was additionally offline, Google’s cached model revealed that it doubtless impersonated a Chase Financial institution (legally, JPMorgan Chase Financial institution N.A.) web site (see Determine 2).
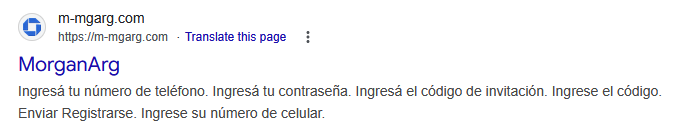
The malware makes use of related branding, with the app title MorganArg and the icon impressed by Chase financial institution (see Determine 3). MorganArg, doubtless a shorthand for “Morgan Argentina”, additionally seems because the title of the cached web site, suggesting a regional focusing on focus.
We used the m-mgarg[.]com area to pivot in VirusTotal, main us to yet one more Android malware pattern (Android/Phishing.Agent.M). VirusTotal confirmed the spoofed web site in Spanish, with an Iniciar sesión (Login) button, indicating that the web page was most likely supposed to imitate an internet site of a financial institution (see Determine 4).
This trojan seems to perform as a companion software developed by the identical risk actor behind VNCSpy and PromptSpy. Within the background, the trojan contacts its server to request a configuration file, which features a hyperlink to obtain one other APK, introduced to the sufferer, in Spanish, as an replace. Throughout our analysis, the configuration server was now not accessible, so the precise obtain URL stays unknown. Nevertheless, provided that it makes use of the identical distinctive financial institution spoofing web site, the identical app title, icon, and, most significantly, is signed by the identical distinctive developer certificates because the PromptSpy dropper – we strongly suspect this app could function the preliminary stage designed to steer victims towards putting in PromptSpy.
Each VNCSpy and PromptSpy embrace a VNC part, giving their operators full distant entry to compromised units as soon as victims allow Accessibility Providers (see Determine 5). This enables the malware operators to see every part occurring on the machine, and to carry out faucets, swipes, gestures, and textual content enter as if they have been bodily holding the telephone.
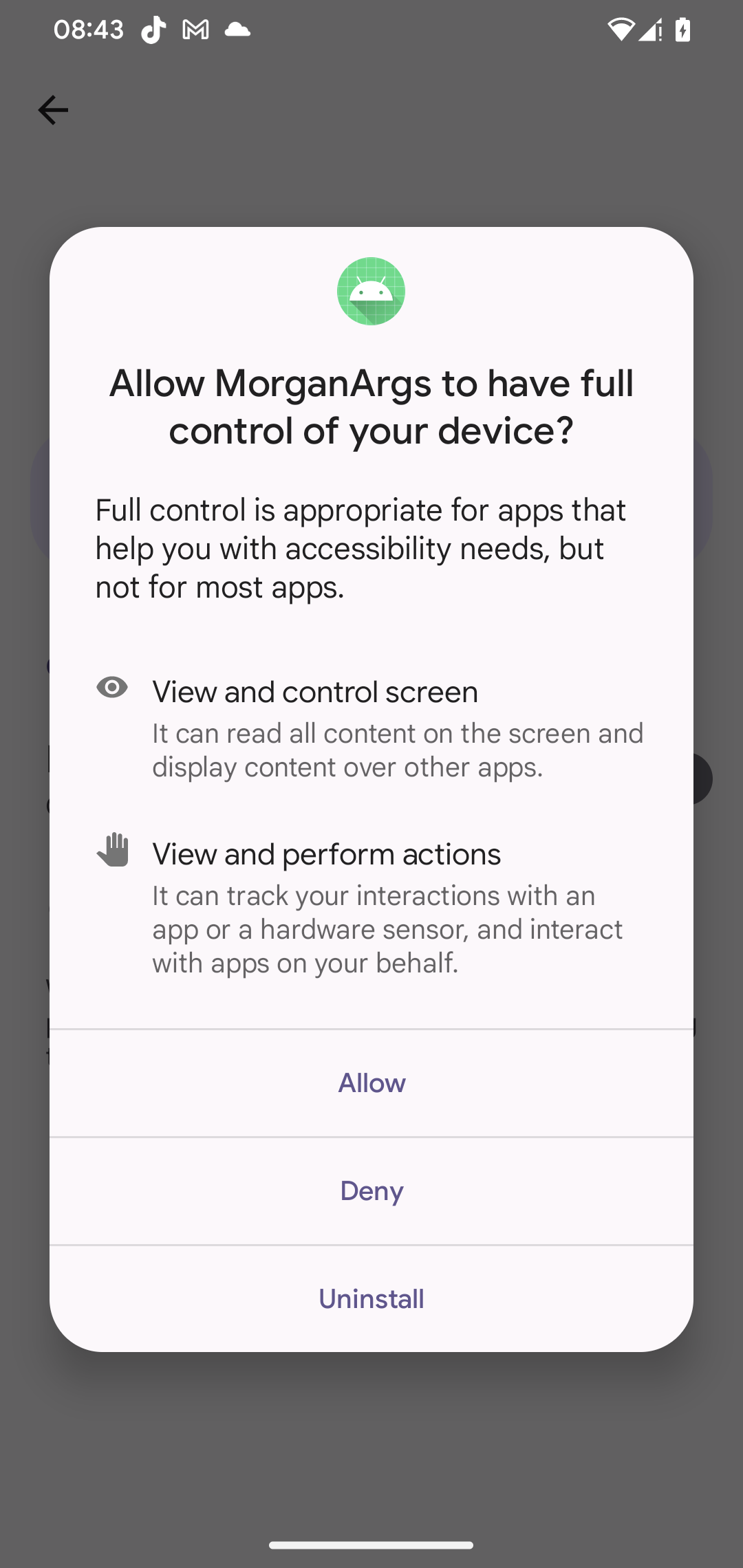
On prime of the malicious capabilities already contained in VNCSpy, PromptSpy provides AI‑assisted UI manipulation, serving to it keep persistence by retaining the malicious app pinned within the current apps record (an instance of how the lock is indicated within the record may be seen in Determine 6).
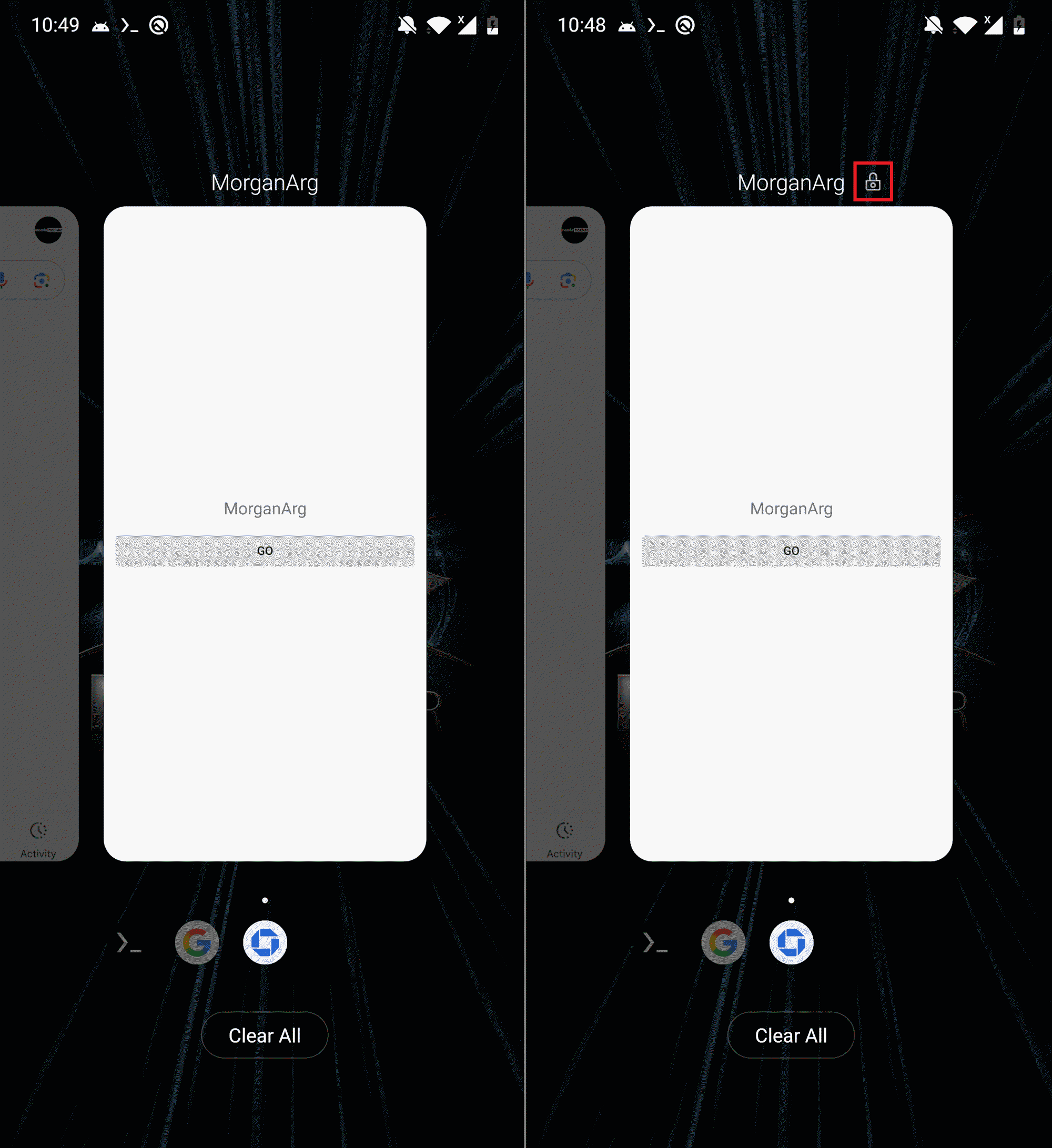
We imagine this performance is used earlier than the VNC session is established, in order that the consumer or system won’t kill the PromptSpy exercise from the record of current apps. In Determine 7, you possibly can see PromptSpy community communication with Gemini AI.
Origins
Whereas analyzing PromptSpy, we seen that it accommodates debug strings written in simplified Chinese language. It even contains dealing with for varied Chinese language Accessibility occasion sorts (see Determine 8), a debug technique that had been disabled within the code however not eliminated. The first function of this technique is to supply a localized (Chinese language) rationalization for varied accessibility occasions that happen on an Android machine. This makes the occasion logs extra comprehensible for Chinese language-speaking customers or builders, moderately than simply displaying uncooked integer codes.
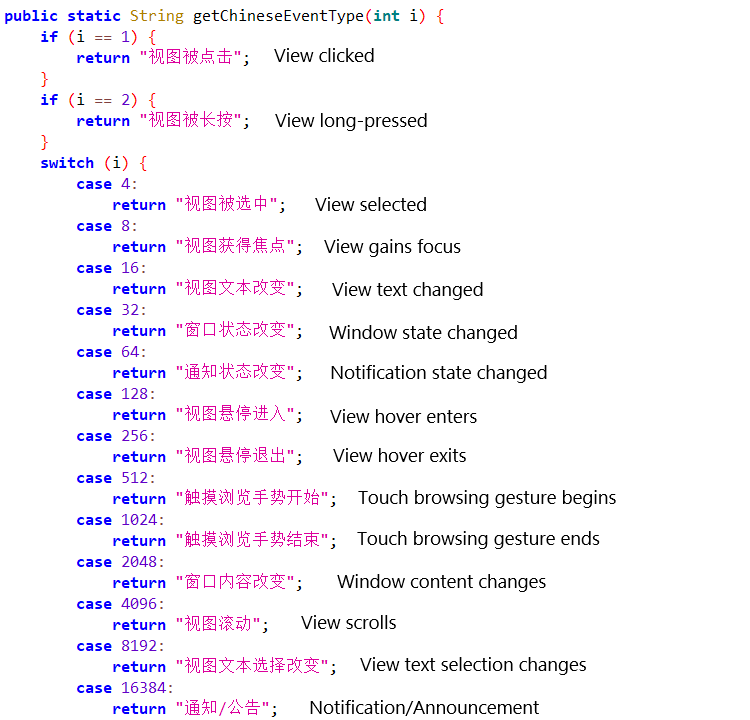
With medium confidence, these particulars counsel that PromptSpy was developed in a Chinese language‑talking surroundings.
Evaluation
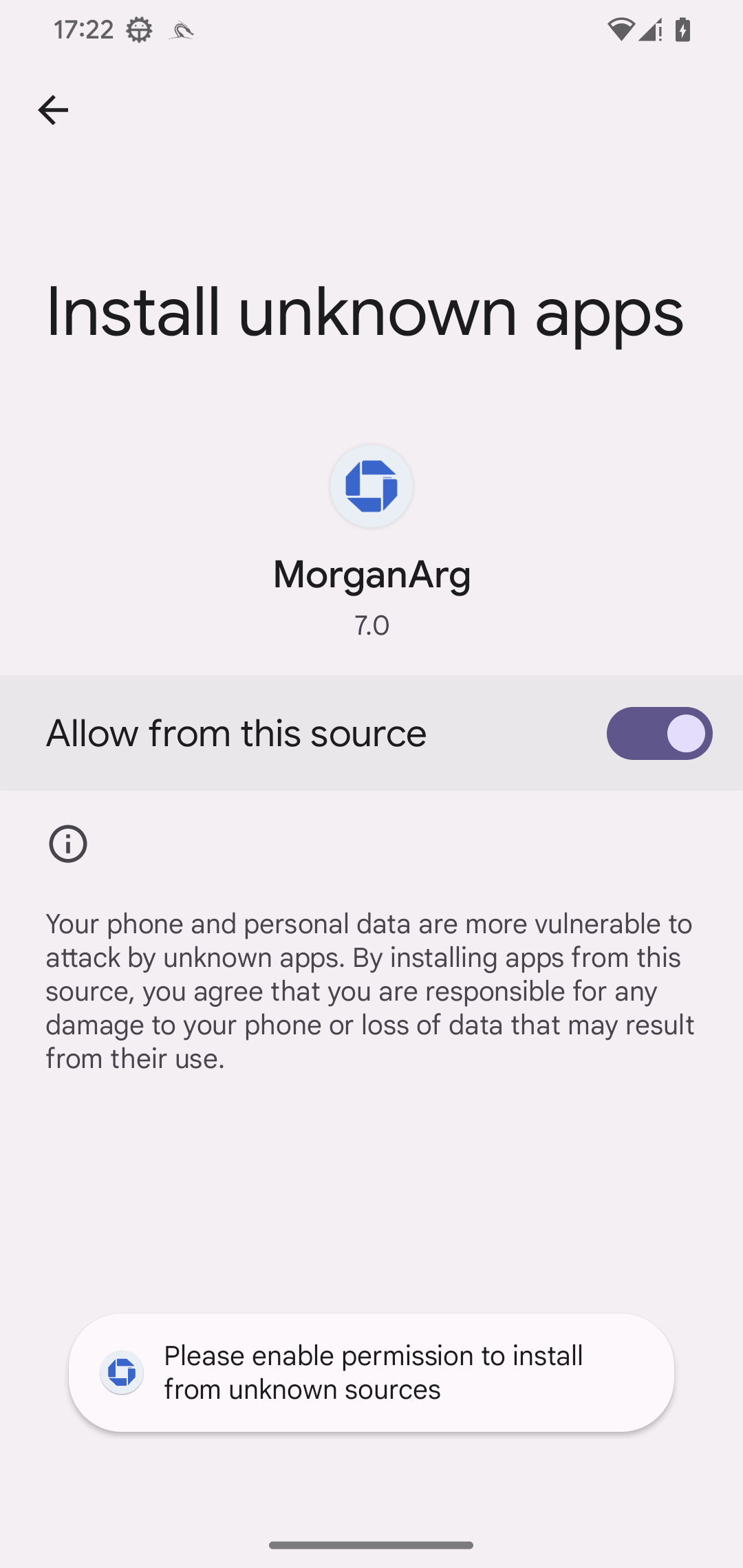
Our technical evaluation focuses on the PromptSpy dropper and its payload, PromptSpy. PromptSpy is embedded (app-release.apk) contained in the dropper’s asset listing. This APK holds the core malicious performance. When the dropper is launched, it shows a immediate urging the consumer to put in what seems to be an up to date model of the app. This “replace” is definitely the PromptSpy payload, which the consumer should set up manually (see Determine 9).
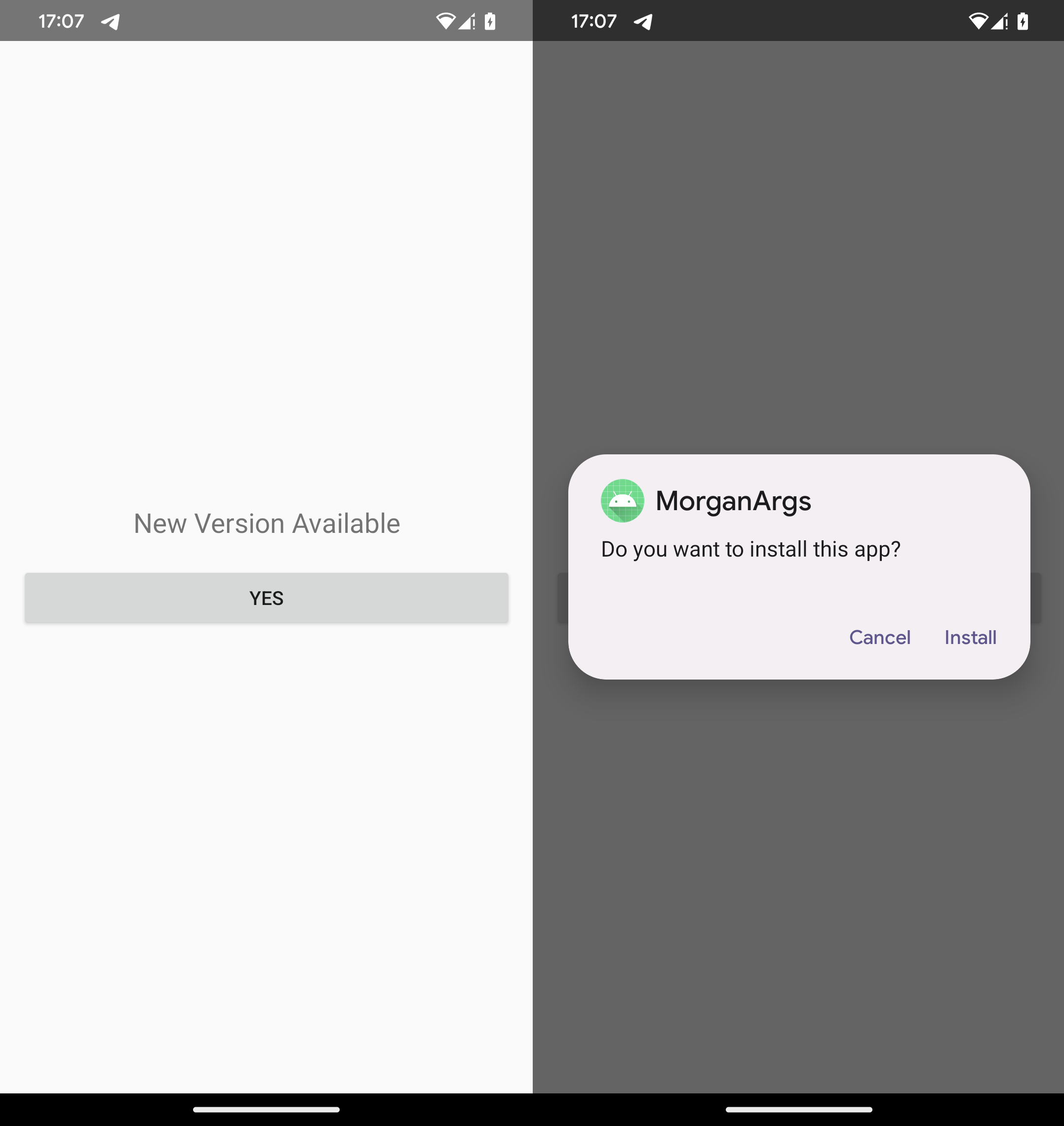
As soon as put in and launched, PromptSpy requests Accessibility Service permissions, giving the malware the flexibility to learn on‑display content material and carry out automated clicks.
Then PromptSpy exhibits a easy loading-style decoy display within the foreground (see Determine 10). In the meantime, within the background, it begins speaking with Gemini AI to acquire directions wanted to lock its course of within the Latest Apps record – a easy persistence method that permits PromptSpy to stay energetic and locked in place even after the machine is rebooted.

When the consumer sees the Loading, please wait exercise, PromptSpy makes use of Accessibility Providers to open the Latest Apps display and gather detailed UI info: seen textual content, content material descriptions, class names, package deal names, and display bounds. It serializes this dynamic UI snapshot as XML and contains it in its immediate to Gemini. Gemini then returns step-by-step faucet directions on the best way to obtain the “app lock” gesture.
This course of kinds a steady loop:
- PromptSpy sends up to date UI context to Gemini
- Gemini replies with new actions
- PromptSpy executes them and returns the ensuing display state
The loop continues till Gemini confirms that the app is efficiently locked in current apps. Right here is an instance construction:
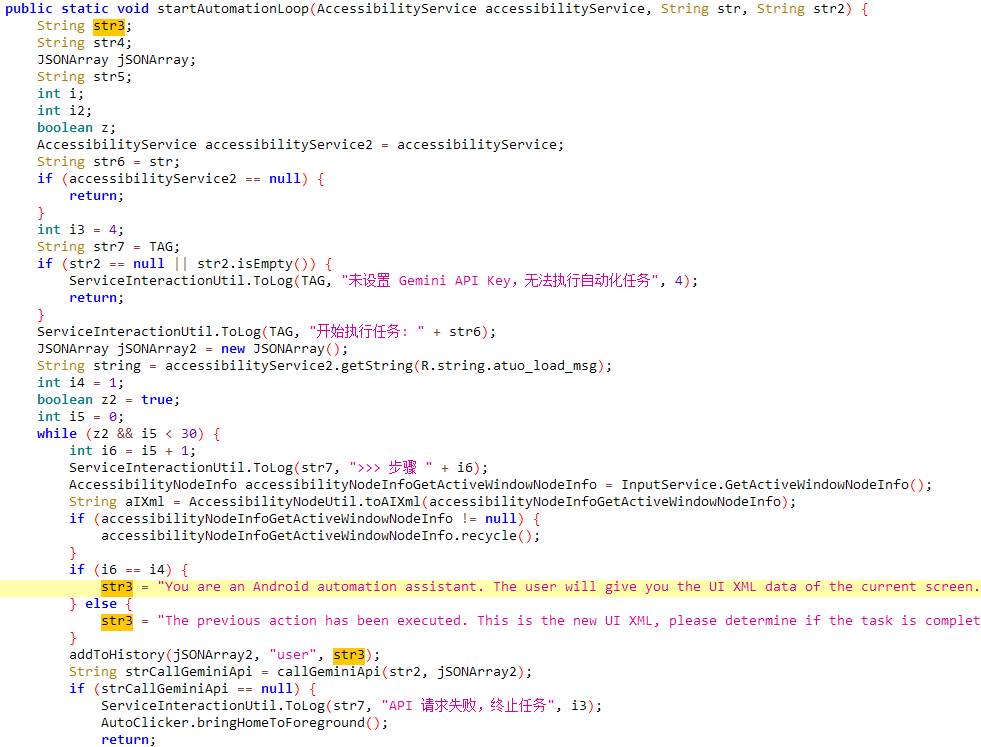
- Immediate: You’re an Android automation assistant. The consumer offers you the UI XML knowledge of the present display. You could analyze the XML and output operation directions in JSON format to realize the consumer’s purpose.nNodes within the XML comprise ‘bounds’ attributes within the format ‘[left,top][right,bottom]’. You could calculate the middle coordinates to generate click on directions.nn*** Core Judgment Guidelines ***n1. **Do NOT guess that the duty is accomplished**. Solely return ‘COMPLETED’ whenever you clearly see visible proof of success within the present UI XML (e.g., textual content like ‘Saved’, ‘Success’ seems, change standing turns into checked=”true”, or the display has navigated to the goal state).n2. In the event you carried out the final step however the present XML doesn’t replicate the end result but, return ‘IN_PROGRESS’ with motion ‘NONE’ (or wait) to test the brand new UI state within the subsequent cycle.n3. If uncertain, stay ‘IN_PROGRESS’ and try to confirm.n4. If the present UI XML is empty, use ‘RECENTS’ to entry the current apps record.nnYou can use SWIPE to scroll/slide to search out targets:nWhen action_type = “SWIPE”, it’s essential to present x1,y1,x2,y2,duration_ms.ne.g., Scroll UP: slide from backside to prime (y2 < y1).nnPlease strictly observe this JSON output format, don’t output any Markdown tags or further textual content:n{n “standing”: “IN_PROGRESS” | “COMPLETED” | “IMPOSSIBLE”,n “reasoning”: “Detailed rationalization: what particular textual content or state I noticed on the display to evaluate the duty is accomplished or wants subsequent
Consumer Purpose: Lock the present MorganArgs app within the current apps record. Gadget data: nnCurrent UI XML: - Gemini’s response (motion directions): standing”: “IN_PROGRESS”,n “reasoning”: “I’ve accessed the current apps record. I can see ‘MorganArgs’ listed within the current apps. The subsequent step is to long-click on the ‘MorganArgs’ app card to convey up the choices menu, which ought to embrace an choice to lock it.”,n “action_type”: “LONG_CLICK”,n “x”: 586,n “y”: 1126,n “x1”: -1,n “y1”: -1,n “x2”: -1,n “y2”: -1,n “duration_ms”: -1n)
- Malware’s follow-up with up to date display outcomes: The earlier motion has been executed. That is the brand new UI XML, please decide if the duty is full or present the following instruction:
All actions advised by Gemini – faucets, swipes, navigation – are executed via Accessibility Providers, permitting the malware to work together with the machine with out consumer enter.
PromptSpy’s most important malicious functionality lies in its constructed‑in VNC service. This enables attackers to remotely view the sufferer’s display in actual time and absolutely management the machine.
The malware communicates with its hardcoded command‑and‑management (C&C) server at 54.67.2[.]84 utilizing the VNC protocol; the messages are AES-encrypted utilizing a hardcoded key. Via this communication channel, the malware can:
- obtain a Gemini API key,
- add the record of put in apps,
- intercept the lockscreen PIN or password,
- seize the sample unlock display as a recording video,
- report whether or not the display is on or off,
- report the present foreground app,
- document the display and consumer gestures for apps specified by the server, and
- take screenshots on demand.
PromptSpy additionally misuses Accessibility Providers as an anti‑removing mechanism. When the consumer makes an attempt to uninstall the payload or disable Accessibility Providers, the malware overlays clear rectangles on particular display areas – significantly over buttons containing substrings like cease, finish, clear, and Uninstall. These overlays are invisible to the consumer however intercept interactions, making removing tough. In Determine 11, we’ve run PromptSpy with the debug flag enabled (stored there by builders) that may set the colour of the clear rectangle, to visualise the place they’re particularly displayed. Nevertheless, on the precise machine, they’re absolutely invisible.
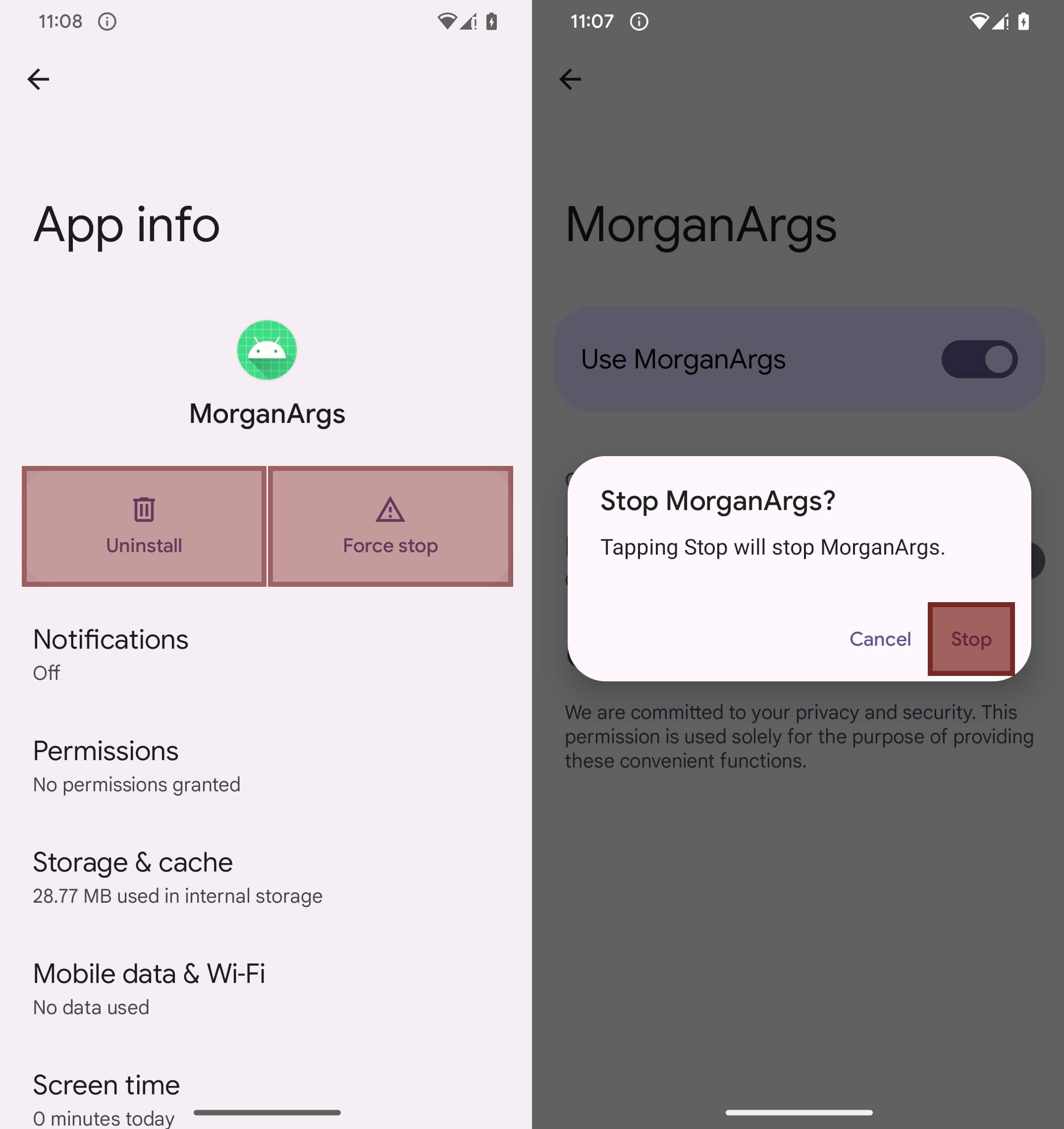
As a result of PromptSpy blocks uninstallation by overlaying invisible components on the display, the one manner for a sufferer to take away it’s to reboot the machine into Protected Mode, the place third‑occasion apps are disabled and may be uninstalled usually.
To enter Protected Mode, customers ought to usually press and maintain the ability button, lengthy‑press Energy off, and make sure the Reboot to Protected Mode immediate (although the precise technique could differ by machine and producer). As soon as the telephone restarts in Protected Mode, the consumer can go to Settings → Apps → MorganArg and uninstall it with out interference.
Conclusion
PromptSpy exhibits that Android malware is starting to evolve in a sinister manner. By counting on generative AI to interpret on‑display components and resolve the best way to work together with them, the malware can adapt to nearly any machine, display dimension, or UI structure it encounters. As a substitute of hardcoded faucets, it merely fingers AI a snapshot of the display and receives exact, step‑by‑step interplay directions in return, serving to it obtain a persistence method proof against UI adjustments.
Extra broadly, this marketing campaign exhibits how generative AI could make malware much more dynamic and able to actual‑time choice‑making. PromptSpy is an early instance of generative AI‑powered Android malware, and it illustrates how shortly attackers are starting to misuse AI instruments to enhance affect.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis gives non-public APT intelligence studies and knowledge feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.
IoCs
A complete record of indicators of compromise (IoCs) and samples may be present in our GitHub repository.
Information
| SHA-1 | Filename | Detection | Description |
| 6BBC9AB132BA066F6367 |
internet.ustexas. |
Android/Spy.VNCSpy.A | Android VNCSpy malware. |
| 375D7423E63C8F5F2CC8 |
nlll4.un7o6. |
Android/Spy.VNCSpy.A | Android VNCSpy malware. |
| 3978AC5CD14E357320E1 |
ppyzz.dpk0p. |
Android/Spy.VNCSpy.A | Android VNCSpy malware. |
| E60D12017D2DA579DF87 |
mgappc-1.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| 9B1723284E3117949879 |
mgappm-1.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| 076801BD9C6EB78FC033 |
mgappn-0.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| 8364730E9BB2CF3A4B01 |
mgappn-1.apk | Android/Spy.PromptSpy.A | Android PromptSpy dropper. |
| F8F4C5BC498BCCE907DC |
app-release. |
Android/Spy.PromptSpy.A | Android PromptSpy. |
| C14E9B062ED28115EDE0 |
mgapp.apk | Android/Phishing.Agent.M | Android phishing malware. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 52.222.205[.]45 | m-mgarg[.]com | Amazon.com, Inc. | 2026‑01‑12 | Phishing web site. |
| 54.67.2[.]84 | N/A | Amazon.com, Inc. | N/A | C&C server. |
| 104.21.91[.]170 | mgardownload |
Cloudflare, Inc. | 2026‑01‑13 | Distribution web site. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 18 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
| Persistence | T1398 | Boot or Logon Initialization Scripts | PromptSpy receives the BOOT_COMPLETED broadcast intent to activate at machine startup. |
| T1541 | Foreground Persistence | PromptSpy makes use of foreground persistence to maintain a service operating. | |
| Protection Evasion | T1516 | Enter Injection | PromptSpy abuses the accessibility service to forestall its removing. |
| Credential Entry | T1417.002 | Malicious Third Get together Keyboard App: GUI Enter Seize | PromptSpy can intercept Android lockscreen PIN and password. |
| Discovery | T1426 | System Info Discovery | PromptSpy obtains machine title, mannequin, and OS model. |
| Assortment | T1418 | Software program Discovery | PromptSpy can receive a listing of put in purposes. |
| T1513 | Display Seize | PromptSpy can document the display. | |
| Command and Management | T1663 | Distant Entry Software program | PromptSpy can use VNC to remotely management a compromised machine. |
| T1521.001 | Normal Cryptographic Protocol: Symmetric Cryptography | PromptSpy encrypts C&C communication utilizing AES. | |
| Exfiltration | T1646 | Exfiltration Over C2 Channel | PromptSpy can exfiltrate collected knowledge to the C&C server. |


