Safety researchers not too long ago revealed that the private info of thousands and thousands of people that utilized for jobs at McDonald’s was uncovered after they guessed the password (“123456”) for the quick meals chain’s account at Paradox.ai, an organization that makes synthetic intelligence based mostly hiring chatbots utilized by many Fortune 500 companies. Paradox.ai mentioned the safety oversight was an remoted incident that didn’t have an effect on its different clients, however latest safety breaches involving its workers in Vietnam inform a extra nuanced story.
A screenshot of the paradox.ai homepage exhibiting its AI hiring chatbot “Olivia” interacting with potential hires.
Earlier this month, safety researchers Ian Carroll and Sam Curry wrote about easy strategies they discovered to entry the backend of the AI chatbot platform on McHire.com, the McDonald’s web site that a lot of its franchisees use to display job candidates. As first reported by Wired, the researchers found that the weak password utilized by Paradox uncovered 64 million data, together with candidates’ names, e mail addresses and cellphone numbers.
Paradox.ai acknowledged the researchers’ findings however mentioned the corporate’s different consumer situations weren’t affected, and that no delicate info — resembling Social Safety numbers — was uncovered.
“We’re assured, based mostly on our data, this check account was not accessed by any third social gathering aside from the safety researchers,” the corporate wrote in a July 9 weblog publish. “It had not been logged into since 2019 and admittedly, ought to have been decommissioned. We wish to be very clear that whereas the researchers might have briefly had entry to the system containing all chat interactions (NOT job functions), they solely considered and downloaded 5 chats in complete that had candidate info inside. Once more, at no level was any information leaked on-line or made public.”
Nonetheless, a assessment of stolen password information gathered by a number of breach-tracking companies reveals that on the finish of June 2025, a Paradox.ai administrator in Vietnam suffered a malware compromise on their gadget that stole usernames and passwords for a wide range of inside and third-party on-line companies. The outcomes weren’t fairly.
The password information from the Paradox.ai developer was stolen by a malware pressure generally known as “Nexus Stealer,” a type grabber and password stealer that’s bought on cybercrime boards. The knowledge snarfed by stealers like Nexus is usually recovered and listed by information leak aggregator companies like Intelligence X, which reviews that the malware on the Paradox.ai developer’s gadget uncovered a whole bunch of principally poor and recycled passwords (utilizing the identical base password however barely totally different characters on the finish).
These purloined credentials present the developer in query at one level used the identical seven-digit password to log in to Paradox.ai accounts for quite a few Fortune 500 companies listed as clients on the corporate’s web site, together with Aramark, Lockheed Martin, Lowes, and Pepsi.
Seven-character passwords, significantly these consisting solely of numerals, are extremely weak to “brute-force” assaults that may attempt numerous doable password mixtures in fast succession. In line with a much-referenced password power information maintained by Hive Methods, fashionable password-cracking techniques can work out a seven quantity password kind of immediately.
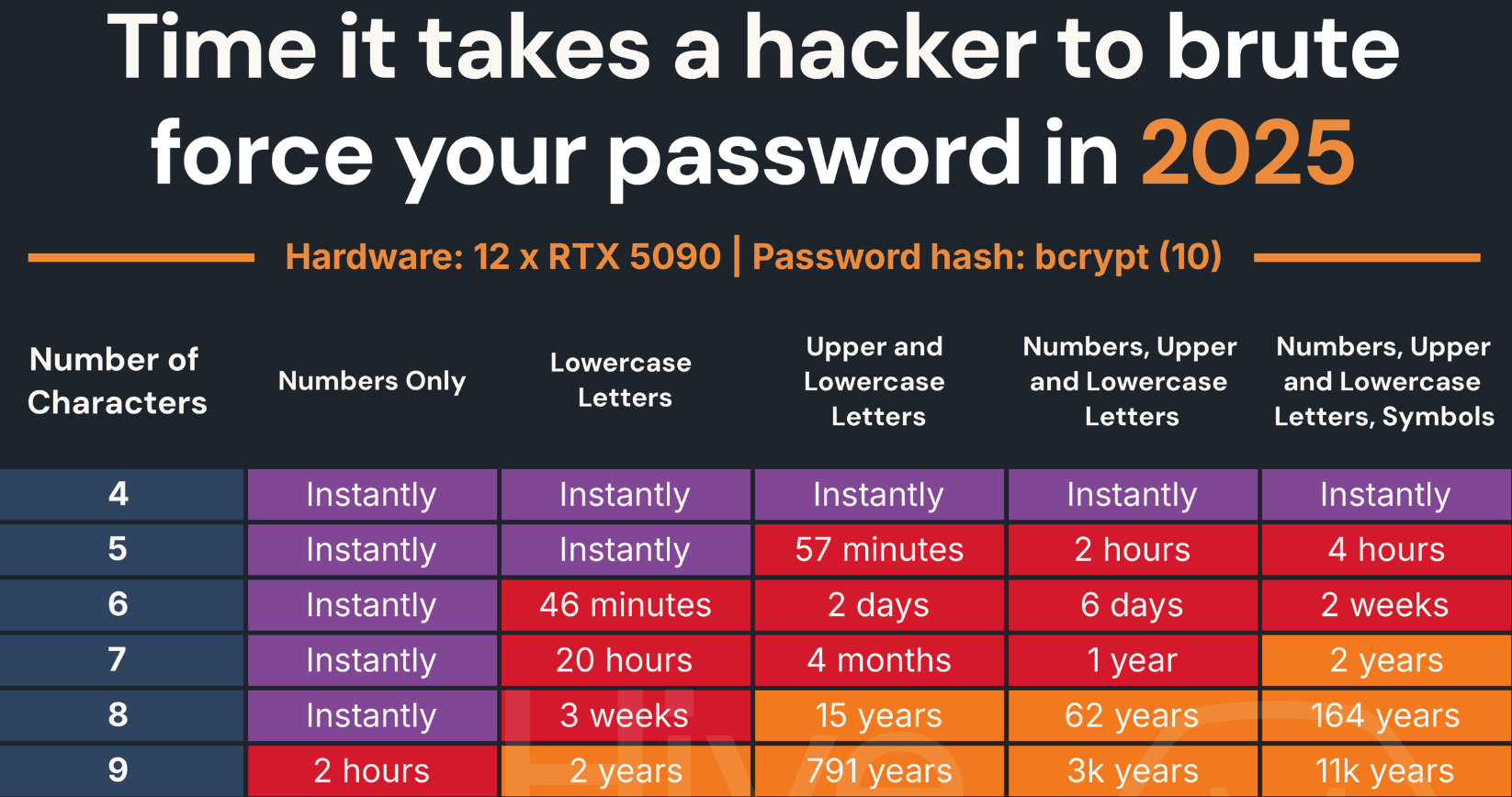
Picture: hivesystems.com.
In response to questions from KrebsOnSecurity, Paradox.ai confirmed that the password information was not too long ago stolen by a malware an infection on the private gadget of a longtime Paradox developer based mostly in Vietnam, and mentioned the corporate was made conscious of the compromise shortly after it occurred. Paradox maintains that few of the uncovered passwords had been nonetheless legitimate, and {that a} majority of them had been current on the worker’s private gadget solely as a result of he had migrated the contents of a password supervisor from an outdated laptop.
Paradox additionally identified that it has been requiring single sign-on (SSO) authentication since 2020 that enforces multi-factor authentication for its companions. Nonetheless, a assessment of the uncovered passwords reveals they included the Vietnamese administrator’s credentials to the corporate’s SSO platform — paradoxai.okta.com. The password for that account led to 202506 — probably a reference to the month of June 2025 — and the digital cookie left behind after a profitable Okta login with these credentials says it was legitimate till December 2025.
Additionally uncovered had been the administrator’s credentials and authentication cookies for an account at Atlassian, a platform made for software program improvement and challenge administration. The expiration date for that authentication token likewise was December 2025.
Infostealer infections are among the many main causes of information breaches and ransomware assaults at present, they usually consequence within the theft of saved passwords and any credentials the sufferer sorts right into a browser. Most infostealer malware additionally will siphon authentication cookies saved on the sufferer’s gadget, and relying on how these tokens are configured thieves might be able to use them to bypass login prompts and/or multi-factor authentication.
Very often these infostealer infections will open a backdoor on the sufferer’s gadget that enables attackers to entry the contaminated machine remotely. Certainly, it seems that distant entry to the Paradox administrator’s compromised gadget was supplied on the market not too long ago.
In February 2019, Paradox.ai introduced it had efficiently accomplished audits for 2 pretty complete safety requirements (ISO 27001 and SOC 2 Sort II). In the meantime, the corporate’s safety disclosure this month says the check account with the atrocious 123456 username and password was final accessed in 2019, however one way or the other missed of their annual penetration assessments. So how did it handle to go such stringent safety audits with these practices in place?
Paradox.ai instructed KrebsOnSecurity that on the time of the 2019 audit, the corporate’s numerous contractors weren’t held to the identical safety requirements the corporate practices internally. Paradox emphasised that this has modified, and that it has up to date its safety and password necessities a number of occasions since then.
It’s unclear how the Paradox developer in Vietnam contaminated his laptop with malware, however a more in-depth assessment finds a Home windows gadget for one more Paradox.ai worker from Vietnam was compromised by related data-stealing malware on the finish of 2024 (that compromise included the sufferer’s GitHub credentials). Within the case of each workers, the stolen credential information contains Net browser logs that point out the victims repeatedly downloaded pirated motion pictures and tv reveals, which are sometimes bundled with malware disguised as a video codec wanted to view the pirated content material.

